2017 OWASP Top 10 for PHP Developers Part 2: Broken Authentication and Session Management
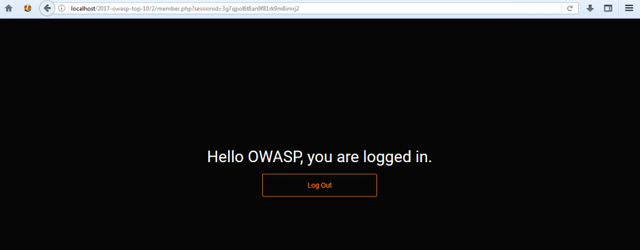
While browsing the web, you click on a link. The link leads you to a page like this:
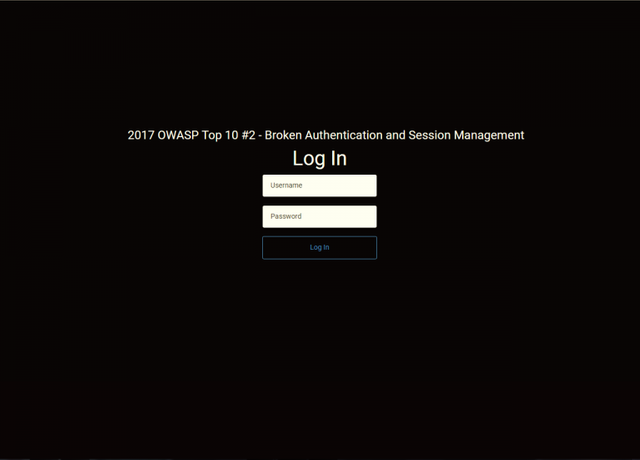
Looks like a usual login page, right? Let’s try logging in.

You go off to Discord and your friend asks for the URL of the login page, you provide him with this:
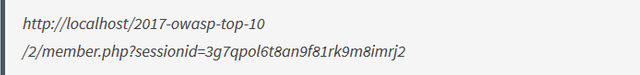
Your friend clicks on the URL and..
Wait – he’s logged in? He did not authenticate, how is this possible?
To understand why this happened, we need to jump back in time and remember the URL that was sent. The URL looked like this:
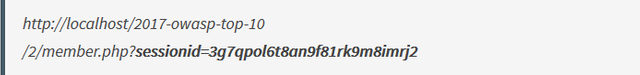
Including a session ID in the URL might not seem very significant at first, but think about it: what if this was your bank? You just sent off a URL that allows access to your account with money in it. Not a very fun scenario, is it?
Such a flaw is known as Broken Authentication and Session Management and it is #2 on the 2017 OWASP Top 10.
In this and the upcoming blog posts I’ll try to cover all of the 2017 OWASP Top 10 vulnerabilities. I will not be covering injection because I already did that in a previous blog post, so I will start from a flaw number two.
What is it?
Such a vulnerability can allow an attacker to capture or bypass the authentication method that is used by a web application. An application might be vulnerable to broken authentication and session management if:
- The URL displays a session ID.
- The session does not expire.
- Sensitive data is sent over an unencrypted connection.
- The credentials that are used to login to a web application are predictable.
- The passwords are stored in plain text without any protection in place (without hashing and / or salting).
I’ll go through each of these scenarios one by one beginning from the top.
Displaying the session ID in the URL
This is so bad that I can’t even fathom it. Displaying a session ID in the URL allows anyone – anyone – to hijack your session by simply copying the URL. What’s the risk you ask? Refer to the example above.
This is the most common way Broken Authentication and Session Management is exploited. It’s easy to patch, yet, according to the 2017 OWASP top 10 list, such a flaw is indeed prevalent.
Failing to terminate a session
Failing to terminate a session is another way of how such a vulnerability could be introduced – having a session which does not expire could allow an attacker to gain unauthorized access to a web application.
You visit a café, log in to your bank account and leave your PC unattended while you go talk to the waitress, come back 5 minutes later and the next thing you see is that you have no money – because your bank did not terminate sessions, someone walked up to your PC, switched to a browser tab and stole your money.
Sending sensitive data over an unencrypted connection
Any sensitive information that is being sent to a web application should be encrypted, meaning it should be sent through the HTTPS protocol instead of using HTTP.
Sending sensitive data over HTTP introduces a web application to a number of risks, most notably, eavesdropping on communications – if your login information is sent over HTTP and your Wi-Fi connection is being monitored, a potential attacker could intercept the traffic.
Predictable login credentials
If a user is using predictable credentials to log into his account, the account could be easily compromised.
Instead, use strong and unique passwords everywhere – each of your passwords should contain uppercase, lowercase letters, numbers and symbols.
It should also be noted that on this occasion, password managers are enormously helpful – if you’re not yet using one, start doing it now.
Insecure password storage
Strong passwords are important, but storing them securely is enormously important too. People might use very strong passwords, but if they are stored in plain text the security of a service could be compromised by anyone just having a peek at them.
If you must store passwords, use a strong hashing algorithm like BCrypt, and, if you have many users, also salt the passwords. A salt is used as an additional input to a hash – it makes cracking large volumes of passwords harder for an attacker.
Wrap-up
Broken Authentication and Session Management is one of the common weaknesses found in modern-day software.
The risks of such a vulnerability depend on a web application and what privileges a user has when logged in, and the consequences of such a flaw being exploited can range from an attacker viewing data he is not authorized to view to you getting your identity stolen – even though such a vulnerability might not seem very severe at first, it is not something that should be taken lightly.