What is a zombie computer? Your computer is not zombie? How to save your computer from being zombie?

If you see Hollywood horror movies like Jimmy Land, Resident Evil, or Dead Snow, then you have a rough idea about "Jimmy". The zombies were mainly caused by viruses, people who were once healthy people. According to the movie they can attack any healthy person and kill people. Different scientists create different viruses and make zombies for different purposes. However, Jimmy's curiosity on the screen of the movie is curious but the zombie computer is not at all curious.
Check your mail account right now and see if there are hundreds of spam mails lying in the spam folder, maybe you get hundreds of such spam emails every day. Where do these mails come from? What hackers do you manually send hundreds of mails? Unfortunately, no! These activities are mostly done using a zombie computer. Hackers do not have only one or two infected computers, a study has found - A hacker can control more than 1.5 million infected computers from just one computer.
In today's article we will know how hackers can control your computer by making them zombie, why they do it and how to save your computer from this attack. So let's get started ...
What is a zombie computer?
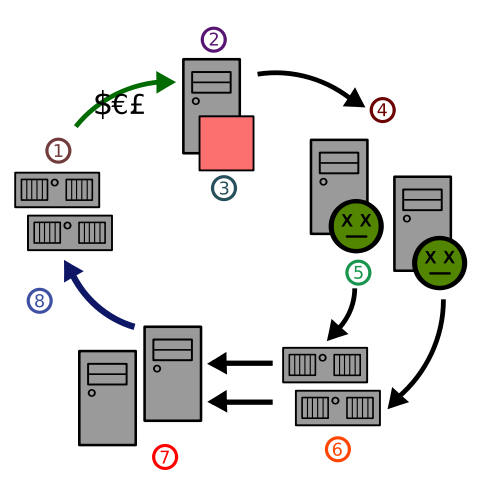
- Spammer website (2) Spammer (3) Spamware (4) Computer infected (5) Virus (6) Mail server (7) User (8) Web traffic
Like a movie I'm not talking about the computer-the computer is back after death and the rest of the computer is infected. Rather, it means zombie computers, computers that have been infected by viruses, malware, or Trojans have been hijacked and they are being controlled by others. Maybe a single person is controlling your computer, and maybe a team of hackers is controlling your computer. And the most horrific thing is that you have little idea, what can be done with your computer.
Many people think, "Brother, I'm a gentleman, what does someone do by hacking or hacking my computer?" Yes, maybe someone will not target you, but you can be the victim of this attack. This attack is not affected by the appearance of the person. Affecting one of your computers means they get a soldier's growth.
When hackers create an entire army of infected computers, they are called botnets. Only those Botanet commanders can order the zombie computers in that Botanet, and this whole computer is controlled via the Internet. It is impossible to trace the behavior of botnet from any computer on this system. Most computer users might not know - their computer is getting somebody else's mischief.
Computer hacking

You may be surprised to know that most computer hacking is done by people who have no knowledge about computer programs. They use a lot of small programs to find your computer operating system or any computer software installed on your computer and try to control your computer. Who is called Craye ** to these attackers. Botanet investigators said their programs are too stereo, and many try to hack with others' viruses. Cray ** These viruses inject your PC into zombie computers.
But if you want to infect your computer, then the virus software is installed on your computer. They send malicious software to your computer by sending spam mails to you, through a pituiti network or through any internet website. CrAp ** Who changes the name and extension of its malicious software, so that you understand it is any other software or work file. As much as you are aware of these attacks from the Internet or from Takehbah, Cray ** will find new ways to find new ways to attack you.
Sometimes when you visit a website, or when you open a webpage, you get various popup messages, sometimes there are no offer information in that message, and you are asked to subscribe to the mail. There is a cross button to cut each popup or a cancell button. Most of the time we click on the canal button, cray ** which can hide the malware download link in this button and the technique can be downloaded to your system.
These malware files are usually in your familiar file format, usually in image files or in a .MP4 or .PDF file. Because these files are formatted as familiar, you will undoubtedly open them. After opening, many computer antivirus capture them - they get away immediately. But when they are not captured on computers, nothing happens after they open, they think the file was wasted or there was a problem with the file. Now the malware fits perfectly with the computer operating system and connects to the auto-start program so that whenever you turn on the computer malware will become active. Malware makes it easy to control your computer's internet traffic and get permission to remote access your computer.
In this way, cray **, which causes hundreds of thousands or thousands of computers to be infected and create an army or botnet with all the zombie computers.
What does Botnet work?
The question is, "Well, what is it that makes this computer so much annoying or creating a Botnet?" Well, the answer is a lot easier, such as Kray ** who hijacked your computer by deceiving you, and using your computer. In order to deceive more people in various ways for money, the main work of the KRA **. But the question is, how are they done?
Spam
Spam is really a lot of annoying thing. Fortunately, your email provider's system now has a lot of advanced spam filters. According to the FBI, most spam mail comes from zombie computers. It is relatively easy to trace spam mail from a particular computer, but cray ** sends spam mail to someone using a zombie computer as a proxy, and many others send spam mails from the botnet, which can be traced to trace hay. . It is possible to send millions of Spam mails together from a Botnet. Now the question is what is spam email? Actually this is the weapon by which krai * spread their malware and make new computers zombies.
How to survive zombie?
You surely never want that your computer is zombie. So you have to protect it from being zombie, but how? There is no reason to worry, my friends, I teach some best steps, that you can be the most protected by observing them. And if you want to follow all the tunes from Techhawb's Security category, they will help you to protect yourself from various hacks or attacks.
#Antivirus must be of course
You have to practice best security in order to be safe, but with good antivirus it is necessary. You can use good antivirus such as Iset, QuickHill, Bit Defender etc., but never remember to use an antivirus version. If you can, stop using all the software, you can get attacked by Kenona first. If you have used the free version of antivirus such as AVG or Avast, then keep them updated regularly and try using a paid antivirus. Along with antivirus, you must install a good spyware scanner. These scanners monitor your computer's internet traffic and warn you when viewing something suspicious. Must update the anti-spyware program.
Use the firewall
To protect your network, install a good firewall. Enhance your router with the default firewall, and update it as soon as the router frameware update arrives. If you do not use a router, use a good firewall on your computer, there are many antivirus present with the default firewall.
Strong password
So far as I wrote articles about computer security, I have used "strong passwords" in almost all of them. Use any password in any account that is easy to guess, and do not use the same password in more than one place, but the length of the password is as good as possible. Use the good password manager to remember all the passwords.
What do you do when zombie?
If your computer is already infected or become a zombie computer, then you should first need to be a computer expert, if it is not possible, then scan your system with good quality antivirus and anti-malware, in this case your computer and cray ** Connecting malware will die. If the virus is not possible to detect, unfortunately your computer's hard drive format and new operating system may need to be installed. Of course, do not forget to backup your data here.
Leaned a lot to avoid my computer become zombie. Try to follow the safety precautions mentioned by you.
upvoted and commented
awesome
nice