What is public key encryption
In this article, I will briefly go over what public key cryptography, or asymmetric cryptography, is.
Basics
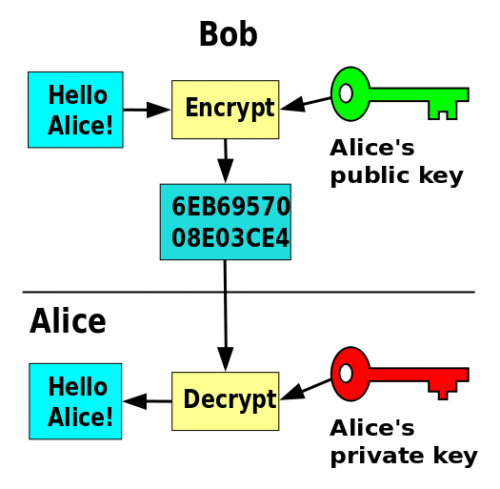
In a public key cryptography environment, there are two keys, a public, and a private key. While the public key can be made, as the name implies, public, the private key should be kept a secret, or other users can easily decrypt all messages sent by you.
But how are, for example, messages encrypted. Well, that can be explained really fast. Messages are encrypted by using a public key and can only be decrypted with the corresponding private key. As the two keys are related mathematically this is possible.
But if the keys are related mathematically, can't I just calculate the private key with a public key. The answer is yes, but very inefficiently, so it could take centuries, or even longer, to do this. But this just applies to traditional computers, as quantum computers can calculate private keys from public keys in a very short amount of time. But that's a topic for another article.
Use cases
Cool, but where is asymmetric cryptography used?
All of you use this encryption daily, as cryptocurrencies, like STEEM, use this cryptography. But other examples are PGP, GPG or even RSA. Also, WhatsApp implemented end-to-end encryption, which is basically another way of saying public key cryptography, a while ago.
Why should I use it?
Well, I'm not your boss, but using this on the internet is very important if you want to get privacy, as intelligence services can't see, at least with a man-in-the-middle attack, what you're writing. Also, if you want to use any kind of cryptocurrency, you have to use it, but I presume you already knew that.
TL;DR
Public key cryptography is a very powerful tool, to hide messages in plain sight. But also every cryptocurrency, at least the ones I know, make use of it.
I hope you found this post interesting. As always, do your own research on the topic. This is just a very superficial explanation and should only animate you to educate yourself more on this topic.


I have been searching through everywhere to find out how to use the public encryption keys @nerdlab any ideas how to actually implement it?
Looks like some folks have a different long term goal in mind for the blockchain and YOUR True monetary and post values.
https://steemit.com/abuse/@iloveupvotes/this-is-the-operation-going-on-behind-your-back-and-all-the-people-that-fund-this-theft-ring
Watch as they flag even this comment to silence the truth from you.