Smart Cards, A chip with so much applications
Good day everyone and I'm happy to bring to us yet another interesting IT component and I'll be talking about smart cards. Smart cards are workaholics but yet, they're so much unnoticed and the few that noticed how important these cards are did so under distress. Let's get going.
Image source Wikimedia. Creative Commons Attribution-Share Alike 3.0 Unported license.
How many of us have paused to give some accolades to our sim cards (Lol, I guess Nigerians can relate to this)? How many of us are aware of the job performed by our ATM cards? I was having one terrible day some days back and it happened that I had also ran out of cash, I dashed into an ATM gallery to pick up some notes and as if that day was destined to piss me off, the queues at the ATM were like soldiers matching out into the battlefield.
I joined the queue, and before I could realize it, seconds turned into minutes and finally it was almost my turn. A guy standing just before me and the machine (and also happened to be checking his wrist watch frequently) inserted his card into the machine and was greeted by an unfriendly message, "card not smart". He tried it couple of times and I opted to help but first I had to check the pins on the card, I realized that a tiny piece is missing from the metallic exposures on the card. I told him the card is gone, he just shook his head and left (if only he was kind to his card).
From my illustration above, I guess some already got the idea of what smart card is. But credit and debit cards are not always smart cards, they’re mostly magnetic strip card. Smart cards, also called integrated circuit cards are small PVC cards with an embedded microprocessor. The simplest example of a smart card is the Subscriber Identity Module, SIM cards. They’re not the same as magnetic strip cards in the sense that magnetic strip cards only “store” data, usually by playing with magnetic fields of the tiny magnetized iron particles on the card.
))
A magnetic strip card which is technology used for many debit and credit cards. Image credit Wikimedia. Creative Commons Attribution-Share Alike 4.0 International license.
Smart cards offer far more security that barcodes and magnetic strip cards, this is because, the information stored in a magnetic strip cards can be read off and encoded into another card and this amounts to identity theft.
All an experienced hacker needs to do is to have physical access to your magnetic strip card, like most debit and credit cards and he will have access to your funds with little effort. Smart cards provide two level authentication (this is known as chip and pin system) which cannot to be seen on barcodes or magnetic strip cards.
History of Smart cards
Though smart cards are fairly young technology, the idea actually started from a club, the Diners Club. The club in a bid to simplify payment process gave out plastic cards to their customers, these cards contained lines which signified the values they held. It dated back to 1955 and is regarded as the earliest implementation of transaction with cards.
Shortly after this, an America’s financial institution, Bank of America bought the idea and developed the first ever credit card. The card could only store limited amount of information and this is majorly due the level of technological development, hence, could only store few characters with no ability to perform any form of data processing and no security feature(s) was implemented. Of course, the technology could not stand the test of time, but today, the cards that was issued by Bank of America is known as VISA card which came before many other cards including MasterCard.
Due to the fact that the cards described above offered little to no security, identity theft was on the rise and this gave rise to magnetic strip cards, this is not the same as the modern magnetic strip cards though. The cards could accommodate roughly 200 bits for every inch of the card and this translates to a card that can store about 80 characters each having a size of nearly 1 byte. These characters encoded on strip cards can easily be decoded using several other means, making it practically unsecure for saving delicate or classified personal and financial information.
The first attempt to develop a card which had “mind” of its own was invented by a Japanese technologist, Arimura Kunitaka. This he achieved by combining many logic circuits, forming a simple arithmetic logic unit with addition of some storage capacity. Kunitaka filed a patent for his idea in early 1970s.
))
Roland Moreno, the father of Microchip. Image credit Wikimedia. Image by Raphaël Labbé. Creative Commons Attribution-Share Alike 2.0 Generic license.
Due to complexities of processing units, Intel Corporation offered a helping hand in the search for a smarter card by developing the first SOC barely a year later and it opened door to many possibilities. The first man to leverage on Intel’s invention was Roland Moreno, in the year 1974. He was the first man to develop a smart card with modern processor architecture.
Moreno pioneered a smart card manufacturing company named Innovatron and it partnered with financial institutions was producing smart cards which was preloaded with certain amount of money. These smart cards were used for shopping and purchases in environments that could support the technology. Not long enough, in 1980, many other manufacturers waded into the smart card business, the most notable ones were Schlumberger and Bull CP8. These two companies are still the leading firms in the smart card technology today.
Smart card architecture and their mode of communication
Smart cards as earlier stated are mostly plastic cards with embedded chips which defines the functions of the card and their categories. There are basically two types or categories of smart cards, these are
- Microprocessor smart cards and
- Memory smart cards
Microprocessor smart cards
Microprocessor smart cards are true smart cards in the sense that as their name imply, they are cards with added intelligence. A microprocessor smart card contains integrated circuit chip along with a well improved memory system. To further wow you, they also spot an operating system. Heard of Java cards? Java card is actually a name given to the Java language developed to run like an operating system on tiny embedded system enabling them to run minimal applications created to perform limited or specialized tasks called applets.
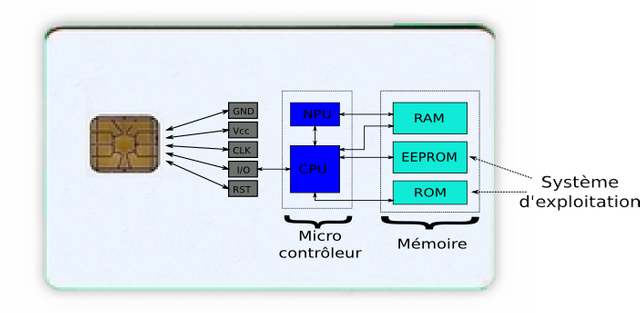
A microprocessor smart card. Image source Wikimedia. Creative Commons Attribution-Share Alike 4.0 International, 3.0 Unported, 2.5 Generic, 2.0 Generic and 1.0 Generic license.
Microprocessor smart cards are almost a complete computer with memory system ranging from volatile to non-volatile memory. These are random access memory which only retains data as long as the system has power and loses it once the system loses its power (volatile), the read only memory which is used to store boot or startup files, the electronic erasable programmable read only memory which is used by applets and comes in handy when interacting with users.
Initially, the SIM cards used by MTN in my country (Nigeria) had internal memory of 128KB and was written boldly on the SIM. Due to increase in the demand for SIM cards and the growing competition in the telecom industry, they sort to reduce the memory size of these smart cards. Today most if not all the SIM cards produced have internal memory size of 32KB and this can be seen written on some SIM cards.
))
Radio frequency smart cards are good example of contactless smart cards. Image credit Wikimedia. Creative Commons license.
Due to their minimal size, the microprocessor embedded in these cards runs the reduced instruction set architecture making them fast in operation and can maintain speeds up to 32 MHz. They have word lengths ranging from 8 bit to 32 bit depending on their application and speed requirements.
A very notable characteristic of microprocessor smart cards is the presence of a metallic contact at one side and one end of the card. This is the pinout from the microprocessor and is the connecting point of the processor and the external system, the card accepting device (CAD). This is seen as the weak point of many microprocessor smart cards as it is mostly the first point of damage to the card maybe due to issues like contact and corrosion.
The memory smart cards
To better understand the difference between the two types of cards, imagine two separate rooms containing very sensitive information. One of the rooms is wide open with soldier armed to the teeth and stands just in front of the room while the other is locked with a special key. Though both are secured, one is smarter and more secured than the other. The former can be seen as the microprocessor smart cards while the later is the memory cards.
Memory cards are also called protected memory cards this is due to the fact that memory card contain some algorithms which describes or assigns the different privilege a user or a system has, this could be read access, write access, read/write or deny as the case maybe.
These cards are designed for environments that are cost conscious, hence, they’re cheaper than the microprocessor smart cards. They also have limited memory when compared to smart memory card with maximum memory size of 16 KB. Their memory structure are made of mainly non-volatile memories like the read only memory and electronic erasable programmable read only memory with the processor replaced with simple logic system usually for access security.
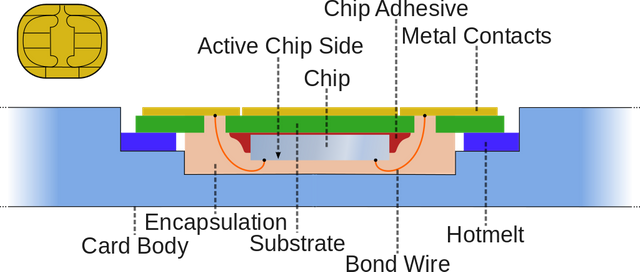
A cross section of contact smart card. Image source Wikimedia. Creative commons license 3.0
In addition to making use of metallic contact on their surface for interacting with its environment, it also uses what is known as contactless access mechanism which presents many advantages more space for card design and development since they have no physical metallic contact point on card, therefore, card component can be in any desired part of the card and not a standard point like the contact cards.
Application Protocol Data Unit (APDU) and Smart card communication
A smart card though a mini computer is still an embedded system which means it’s not a complete system. It works alongside a card accepting devices called a smart card reader. These two systems communicate securely using what is called application protocol data unit, APDU. To understand what an APDU is let’s talk about PDU (protocol data unit).
A PDU is a term used in computer networks to describe the different forms data take as it traverses different OSI (Open System Interconnect, a standard model of the internet developed by the International Standard Organization, ISO) model protocol stacks. For the seven layers of the internet model, through the Application layer, Presentation layer and Session layer, data remains data, hence, the PDU for these three layers is called data. At the Transport layer, data is segmented and joined, hence the PDU at the transport layer is known as Segment. At the Network layer, logical addressing scheme is added to each segments and are called Packets (the PDU at the network layer), it is only packets that can traverse inter-networks.
))
At the transport layer, the data stream is broken down into segments (PDU at layer 4), at the network layer, addressing scheme is added to each segment encapsulating it into packets, finally at the physical layer, the data is transmitted as bits. The encapsulation for the APDU is shown on the column to the right. Image credit Wikimedia. Creative Commons Attribution 3.0 Unported license.
At the Datalink layer, physical addressing scheme is further attached to the logical addressing scheme and data is encapsulated as Frames (the PDU at the datalink layer). Frames can only be passed around within a network any need to pass it to another network will warrant removal of physical addresses making it a packet. At the Physical layer, Frames are broken down into bits, hence, the PDU at the physical layer is called Bits.
APDU is also a communication standard defined by the International Standard Organization and just like the normal PDU, its communication mode is bi-directional. Due to the fact that its bit transfer rate is very small, it is less prone to attacks. The communication system is categorized into two, the response APDU which is used by smart card itself to communicate with the CAD and the command APDU which is used by the CAD to communicate with the smart card.
For the smart card to communicate with the CAD, it first ensures that the medium is safe by first generating random integers, enclose it with a header of size 2 bytes. It transmits this to the CAD at the rate of 9600 bits per second and keeps a copy and encrypt it this copy. On reception of this data by the CAD, the device also encrypts the data and sends the result of this encryption to the smart card. When the smart receives this encrypted data, it compares it with the encrypted copy it retained, if the result is a match, the medium is tamper proof and can then transmit data in both ways.
Smart Card Security
As stated earlier, smart cards are highly secured card which offers two level authentication but how does it accomplish such feature from the user perspective? I would simply say, it all lies in its file system. Smart card maintains a hierarchical file system with a central file which contains every other file and acts like a root directory. This file is known as the master file. The master file houses two other types of files, the Dedicated and Elementary file.
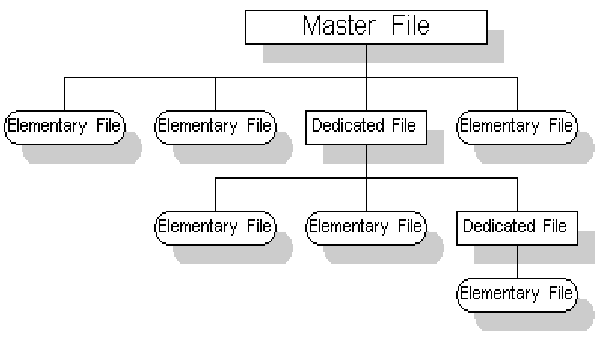
Smart card hierarchical file system. Image source Researchgate. Creative commons license.
Security of these files is handled by their header which contains security algorithms meant to deny or accept certain access. We as the users don’t directly make use or see these files rather, access to these files are done by applications as intended by the operating system, like the Java card. Not every application has access to these files, hence, applications are assigned privileges and this governs their level of access. We empower the applications to access these files and perform different tasks like make calls or store information by providing verification requirements as the application tries to access any required file.
There are five levels of priority given to application and this depends on the success of file verifications. These levels of priority are:
- Always
- Card holder verification 1
- Card holder verification 1
- Administrative
- Never
An application that have the value of card holder verification 1, has fulfilled the first verification requirement(s) and the same is applicable to application with value of card holder verification 2. The Never value is the opposite of Always value and indicates the application has no access to the file system, this is due to failed verification or absence of verification. Just as the name implies, application with the administrative value presides over the priority of other values.
To us as users, these values are given in terms of personal Identification Numbers or PINs. These numbers are stored locally in the file system. For example, a locked SIM card always requests for the PIN irrespective of the device that wants to read its content or use its service(s). There are basically two security keys or strings stored in the smart card, these are Unblocking key and User key. The unblocking key is required to gain access to the system if the user key is entered unsuccessfully for a predefined trial times.
Applications and Summary
The need to provide a secure means of saving and processing very personal information has led us to the discovery of smart cards. They’re smart indeed with a functional microprocessor and memory with input and output system. They communicate with their host using tiny but fast and secured protocol called application protocol data unit which cannot be intercepted easily with a higher computer.
Smart cards have the ability to connect to the internet directly which is something other cards like the magnetic strips cannot do. Hence, they’re largely used in the telecom industry for the subscriber identity module which used to identify a mobile node within the network. Since they have storage ability, they’re employed largely in secured organization in conjunction with biometric technology for employee identification and also health insurance cards. Think secure personal data storage and processing, think smart card.
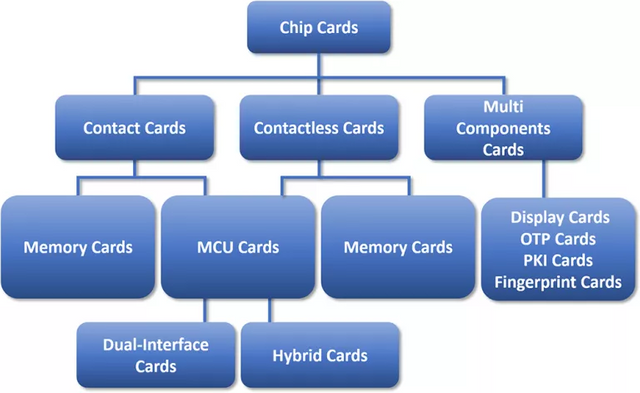
Summary of smart card distributions and classifications. Image source Embeddedsecuritynews. Creative commons license.
I hope that this has been informative for you and I’d like to thank you for reading.
REFERENCES
- Smart card ~Wikipedia
- What is smart card ~Embeddedsecuritynews
- Java card ~Wikipedia
- Smart card APDU ~Wikipedia
- Difference between credit card, debit card and smart cards ~Coursecommerce
- History of smart cards ~Hospitalityupgrade
- Microprocessor card ~Usmartcards
If you write STEM (Science, Technology, Engineering, and Mathematics) related posts, consider joining #steemSTEM on steemit chat or discord here. If you are from Nigeria, you may want to include the #stemng tag in your post. You can visit this blog by @stemng for more details. You can also check this blog post by @steemstem here and this guidelines here for help on how to be a member of @steemstem. Please also check this blog post from @steemstem on proper use of images devoid of copyright issues here.


This is a massive one! The fact that it began with a story made me stay glued.
As a Nigerian, Permanent Voters Card was the first pop in my mind...lolWhat is full meaning of PVC card
Sorry Nigeria's permanent voter's card is not a smart card, PVC I meant was polyvinyl chloride
Okay I am cleared on that now, Thanks! @henrychidiebere
This post has been voted on by the steemstem curation team and voting trail.
There is more to SteemSTEM than just writing posts, check here for some more tips on being a community member. You can also join our discord here to get to know the rest of the community!
Hello @henrychidiebere!
Your article are always top notch and very well written. It would be amazing if you could also share your ideas and thoughts on other people's posts a little more often. :D
Cheers mate!
Thanks @dedicatedguy, I recently got myself in a new work environment and things have been really tough for me. For the most part I try to drop one or two paragraphs a day before going to bed and it results in my making posts less than once a week. I know I'm lacking in the community engagement part and I'll try to add at least one comment per day to my schedule. Thanks again for the observation.
This is a great info piece. I've read about it and talked to others about it to try and learn more but this creates a great concise source of information to reference.
I'd love to see an article that goes over how systems such as Google Pay (formerly Android pay) and other phone based contactless systems work!
Thanks @prlndra I really don't know much about Google pay and working principles of many Google products are not all that readily available on the Internet.
I know Google probably uses their own secret sauce but I imagine the phone based tap and pay payments systems have some standard that's documented somewhere. I would love to read a concise post like this on the topic if you ever get the time!
I think the ability of smart card to connect directly with the Internet makes it even smarter than other kinds of care.
Nice write up
Correctly said, of course it have full protocol stack like the TCP and that makes such connection possible.
So many things we use everyday but don't even know the technology that made it possible. Thanks for the post, I've learned a lot.
You're welcome buddy and thanks to you too.
smart card have truly helped our society to be smarter and safer. if not, a whole lot of things would have gone wrong because of the flaws of the magnetic strip card. Now, i would have to be extra careful with my card.
nice write up
What we have here in Nigerian banking system is mostly magnetic strip cards, we really need to be careful with it
so interesting
Magnetic strip cards are the reason most people in Nigeria distrusts debit/credit card as they think the new smart debit/credit cards are as susceptible to hack as the magnetic strip card was.
Funny enough many don't know the cards are not that safe. Wonder when they'll be implementing our debit and credit cards with contactless smart cards😛. Thanks buddy👍
Wow! Great information