The Processor Bug: Everything You Need To Know About The Massive Meltdown And Spectre Leaks And How It Affects Your Computer
Rumors have been circulating for a while regarding a potentially catastrophically dangerous bug that is present in most modern computer processors, including the majority of Intel’s CPU line-up. The bug allows for exploits to run and can make it possible to read memory directly from your system’s kernel and other processes, something that should, in fact, be impossible due to a process called memory isolation. [1]
Image source: Pixabay
Because this bug opens up the door for exploits to reach this memory, sensitive information such as passwords and encryption keys are vulnerable. Most modern processors from Intel, AMD and ARM are vulnerable to this bug, which means that most of your devices need to be updated as soon as possible to protect yourself from malicious hacking attempts.
Researchers have now published details about the Meltdown and Spectre vulnerabilities. Manufacturers of the processors have already released patches to fix this bug once and for all, but in some cases, systems take a major performance hit, especially when running the Linux operating system.
Image source: Public Domain Pictures
This article will go in-depth on the processor bug, Meltdown, and Spectre, and will detail everything you need to know about these vulnerabilities.
What exactly is going on?
The origin of the bug can be traced back to June 2017, when a couple of researchers from Google’s Project Zero team discovered a bug that was present in a number of processors. The Project Zero Team is a special division by Google with the objective to find ‘zero-day’ leaks in software. Zero-day leaks are dangerous, undiscovered bugs that could potentially be abused for exploits and malware. [2]
The researchers from Project Zero then notified the developers of Intel, ARM, and AMD in secret to make sure that the bug would be able to be fixed before exploits started showing up. The non-disclosure agreement was supposed to end somewhere next week, which should have given all of the chip manufacturers plenty of time to create, test and implement a fix.

Image source: Pixabay
Recently, someone discovered that the Linux kernel had been updated slightly, and they quickly discovered that the added files were a patch for this specific security leak. The news quickly spread and the leak was suddenly made public before the end of the secrecy agreement. In a hurry, CPU manufacturers issued out press releases and the patches that would be able to fix the problem. [3]
The majority of computer users have a system with the Windows 10 operating system. As of yesterday, Microsoft has released a patch that addresses the processor bug and it is being rolled out via Windows Update. [4]
Technical details: how does the leak work?
As stated above, the processor bug allows for exploits to read sensitive data of the memory which should be protected. This potentially compromised data is being processed by the CPU, where an attack or exploit can take place.
The bug operates on a speculative execution feature, which is present in most modern processors, including those found in game consoles, for example. In short, if there’s a value necessary for a certain calculation that is still calculating or being retrieved out of the memory, your CPU will speed up the process by guesstimating what the result will be, which allows your system to continue with the requested operation or command. This is called a branch prediction. In most cases, these branch predictions are pretty accurate.
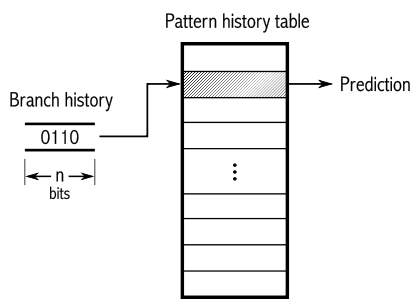
Image source: Wikipedia
However, when this branch prediction fails and is incorrect, the CPU will dispose of the wrong value. At the exact moment that this incorrect value is disposed of, the bug allows the generated cache for this command to be approachable for any program running on a computer system. Sensitive data can be stored in this generated cache and be read by a malicious program.
What are the differences between the Meltdown and Spectre leaks?
Meltdown and Spectre are the two leaks that were discovered. The two operate in different ways but are equally as dangerous. For now, it is assumed that the Meltdown bug only affects Intel processors. Spectre also affects AMD and ARM (mobile) processor architectures. In short, Meltdown allows for reading the kernel memory which should be protected, while Spectre allows the same thing for ongoing system processes.
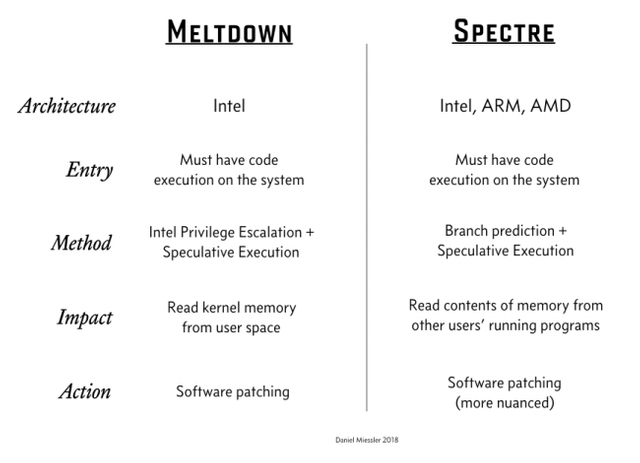
Image source: Daniel Miessler
Security expert Daniel Miessler created the picture shown above which quickly elaborates on the differences between Meltdown and Spectre. [5]
Meltdown, specified by the code CVE-2017-5754, allows applications without administrator rights to access data which normally requires this security clearance. This means that protected kernel data could possibly leak to regular software.
Luckily, a patch for Meltdown is fairly simple. By simply disabling the combined speculative execution for kernel- and user-data, the Meltdown leak is essentially fixed. However, this fix does come at a price: the theoretical performance of the CPU decreases. In most cases, this hit in performance won’t be noticeable, unless in tasks where’s there plenty of activity in the input/output processes. Even though most exploits would be patched, security experts claim that processors affected by Meltdown will always have somewhat of an attack surface remaining, despite the countermeasures. The only way to get rid of Meltdown completely is to eliminate the bug from the production process of CPUs altogether.
Spectre 1 and 2 (defined as CVE-2017-5753 and CVE-2017-5715) operate on a slightly different method. Spectre is more complicated to abuse, and unfortunately, also more complicated to patch. The two bugs allow for virtual machines to access data from an entirely different virtual machine, or even the host operating system. This means that a virtual machine can effectively break out of its sandbox restrictions which is exactly what virtual machines aren’t supposed to do. Because of this possibility, Spectre can be incredibly dangerous. Disabling speculative execution for all of these sensitive instructions isn’t a perfect fix for Spectre. Luckily, specific exploits are patchable with relative ease.

Image source: The Hacker News
Which processors and computer systems are vulnerable?
Since practically all processors are being manufactured by either Intel, AMD, and ARM, most modern devices are vulnerable if the patch hasn’t been installed. Intel and AMD are active on the market for desktop and notebook CPU’s, as well as chips for gaming consoles such as the Xbox One and PlayStation 4. ARM architecture is mostly used in mobile devices such as smartphones and tablets. [6] [7]
The investigators from Google’s Project Zero team have demonstrated that the bug works on an Intel Xeon chip (which are used in servers), as well as a regular consumer CPU from the relatively recent Haswell generation. As stated above, Meltdown has not been proved to work on CPU’s from AMD or ARM. However, there is a slight chance that a refined, more optimized version of the Meltdown code could perform a successful attack on these processor architectures. Researchers believe that Meltdown works on Intel CPU’s dating back all the way to 1995.

Image source: Flickr (Creative Commons)
Project Zero researchers successfully demonstrated the Spectre vulnerability on processor architectures from Intel, AMD and ARM. Regarding the latter, the Cortex-A75 chips are vulnerable to both Spectre and Meltdown. ARM’s Cortex-A15, A57, and A72 are protected against Spectre and aren’t in need for a patch against Meltdown.
How can I protect myself against the leak?
The most important thing is to always keep your software and devices up to date. The updates are there for a reason, even though many believe that they’re an annoyance rather than an improvement.

Image source: Wikimedia Commons
Windows 10 | Microsoft has already released a patch via Windows Update. It is, however, important to update your anti-virus suite as well, as some anti-virus software access kernel-calls of your system, which will result in the Windows update not showing up.
Android | The Android operating system has also received a security update which fixes the vulnerability and is incorporated in the January Security Patch. Unfortunately, not all Android manufacturers are quick in releasing these updates and your phone or tablet may still be at risk. [8]
iOS and Mac OS | As of January 5th, 2018, Apple has responded to the leaks with software updates. iOS 11.2, tvOS 11.2 and macOS 10.13.2 are now protected against Meltdown, with a fix for Spectre coming soon. Safari and watchOS will also be updated in the near future. [9]
Web browsers | Web browsers are currently implementing countermeasures against the bug. Firefox has started with taking the first steps for better protection in Firefox 57, while Chrome will have built-in protection when version 64 releases on January 23rd. [10]
Gaming consoles | As of this moment, no specific fixes for the current gaming consoles have been released, although they will most likely be patched in an update. It’s recommended to avoid using your console’s built-in web browser.
Linux | The Linux-kernel has received patches in version 4.15. Developers are currently working on more complicated Kaiser-patches which offer better protection against Meltdown.
If you want to be safe – always update your systems as soon as possible. This doesn’t only apply to Meltdown and Spectre, as security exploits are discovered every single week.
Does the patch for the processor bug affect system performance?
Because of the way that the bug works, a performance decrease is inevitable – at least, in theory. Some suggested that the performance hit would be as much as 30%, but that number is exaggerated for normal use-case scenarios.
A number of different technology and hardware websites have run their own tests with the identical system before and after the patch was applied. There is a general consensus: the patch does affect performance, but the difference is minimal.
Cinebench 15, for example, only shows a performance loss of around 1%. The same number applies to gaming performance and input/output operations (such as reading and writing on a solid state drive). In other words, consumers won’t notice this performance difference at all.
Image source: Public Domain Pictures
However, very specific scenario’s will definitely suffer from the security fixes. Phoronix has released benchmarks where input/output performance is essentially halved under Linux. It’s the open-source operating system that seems to be having the most performance issues with recently released security fixes resulting in a noticeable performance hit. [11]
Luckily, most consumers don’t have to worry about their computer suddenly becoming slower.
However, it remains essential to install your updates in order to be protected from Meltdown and Spectre, collectively known as the processor bug – possibly one of the worst and most dangerous bugs discovered in the last few years.
References:
- [1] Intel: Analysis of Speculative Execution Side Channels
- [2] LWN and Graz University of Technology
- [3] Google Project Zero
- [4] Microsoft
- [5] Daniel Miessler
- [6] ARM
- [7] AMD
- [8] Android
- [9] Apple
- [10] Chromium
- [11] Phoronix
Enjoyed this post? Feel free to upvote and follow @RebelHeart!

Great post! Some of the more technical nuances are beyond me, but this is very informative and well referenced throughout. I'm glad you put in that "how can I protect myself" section so we know what to do about the leaks.
Thanks, really appreciate it!
quality, excellent quality post
Even more informative than the 3 online computer magazine articles i read before this.
I'm flattered, thank you. :)
Security is being strict attacks are getting wild
Definitely, security will become more and more important.