Top 10 criteria for choosing a VPN provider
In my previous post, "How to choose a VPN provider", I gave a high level overview of how to choose a VPN provider. Here's just a quick Top 10 list of things to look for. Be aware that your mileage may vary. Decide what is important to you!
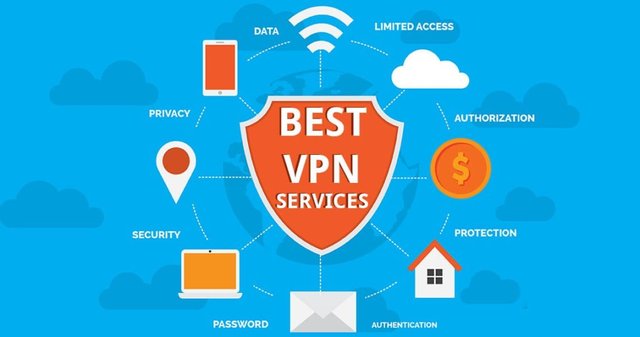
image credit: themelines.com
Top 10 features to look for in a VPN provider?
Important features to look for in a VPN provider begin with location. If VPNs have not been outlawed in your country, you probably want a provider that operates servers in your area. Using servers located close to you reduces network latency. On the other hand, if your goal is to skirt geogrpahic restrictions, having locations in nearby countries would be a high priority.
Speed! We all want it. Whether or not there's a server located close to you, the upstream and downstream speeds are important to all of us. Serious degradation of service results in frustration and a poor user experience. This is not only a function of location, but the network architecture, server load, and more.
Price - there I said it. I talk about security and privacy and technical stuff, but price is important to many of us. Most providers seem to offer steep discounts for their longer term plans. Many offer one day, weekend, or other short term trial plans as well, so you can try before you buy.
Payment method is a concern to the privacy crowd for obvious reasons. Most of the good VPN providers accept payment in Bitcoin and other cryptocurrencies, which leaves anonymity up to the buyer. Some are very careful to keep payments data like credit card info isolated from other account information.
Logging of account activity is a concern because any records kept must be surrendered to government agencies in the countries a VPN provider operates in. If nothing is logged, nothing can be disclosed. Some log everything, some log only bandwidth use and connection times, and a few actually claim to log nothing. There is no transparency here however, so do a lot more research into how a particular company operates before trusting their claims.
Custom clients can automatically kill all activity when the VPN connection is dropped, to avoid exposing the user. If this is not supported, your ISP can force a dropped connection periodically in order to see what you do. Even if you're being vigilant, clients like web browsers will often make requests for resources that you have not explicitly requested. This feature is usually referred to as a kill switch. Don't settle for one that makes you list applications to kill - there are plenty of processes that will not show up on a list of "applications", so this is not a good solution.
DNS leaks and IPv6 leak protection is important also. It does you no good to hide your traffic if your DNS queries are still being resolved by your ISP's nameservers. Your ISP will basically know all domains you navigate to with a web browser, send emails to, etc. so all DNS queries need to be sent through this connection. Similarly there are commonly issues with IPv6 leaks, but most custom clients will deal with this for you as well. These leaks can also occur from the VPN network as well, but when they happen on your device, it renders this strategy useless.
Infrastructure matters. Lots of servers in lots of locations is what you want to see. It takes years of relative stability to establish operations in locales around the world and it makes for a robust network.
Router support should be solid. The first place to look when you're implementing your VPN strategy is your home router. If you install a VPN client on this device, then all connected devices will send their traffic through the VPN connection. This has obvious advantages over installing clients on each device, although most providers are generous about the number of devices you can have connected simultaneously. Also note that tunneling one VPN through another is not a problem, so clients should remain installed on your mobile device at all times regardless of other arrangements.
Mobile support is critically important. Your smartphone is as capable as your home computer, only it has aditional components and capabilities that make it a greater security concern. Phones often connect to public Wi-fi networks for example, which are high-risk environments. I recommend using OpenVPN client on mobile devices because it's a trustworthy standard. It should be noted that others disagree, and prefer the ease-of-use provided by custom iOS and Android clients. These may be buggy however, so caveat emptor.
Remember your mileage may vary. The point is that you should figure out what matters most to you and judge providers based on that. For example, linux users will always want to choose VPNs that adhere to OpenVPN standard, and will need to ensure there are safeguards in place to avoid DNS/IPv6 leakage, and killswitch functionality.
Posted from my blog with SteemPress : https://chainwars.one/top-10-criteria-choosing-vpn-provider/
Great post! 👍
You got an upvote, you need to follow this account for more upvotes in the future 👊🏼