How to configure a site-to-site VPN
[fusion_builder_container hundred_percent="no" hundred_percent_height="no" hundred_percent_height_scroll="no" hundred_percent_height_center_content="yes" equal_height_columns="no" menu_anchor="" hide_on_mobile="small-visibility,medium-visibility,large-visibility" status="published" publish_date="" class="" id="" background_color="" background_image="" background_position="center center" background_repeat="no-repeat" fade="no" background_parallax="none" enable_mobile="no" parallax_speed="0.3" video_mp4="" video_webm="" video_ogv="" video_url="" video_aspect_ratio="16:9" video_loop="yes" video_mute="yes" video_preview_image="" border_size="" border_color="" border_style="solid" margin_top="" margin_bottom="" padding_top="" padding_right="" padding_bottom="" padding_left=""][fusion_builder_row][fusion_builder_column type="2_3" layout="2_3" spacing="" center_content="no" link="" target="_self" min_height="" hide_on_mobile="small-visibility,medium-visibility,large-visibility" class="" id="" background_color="" background_image="" background_image_id="" background_position="left top" background_repeat="no-repeat" hover_type="none" border_size="0" border_color="" border_style="solid" border_position="all" border_radius="" box_shadow="no" dimension_box_shadow="" box_shadow_blur="0" box_shadow_spread="0" box_shadow_color="" box_shadow_style="" padding_top="" padding_right="" padding_bottom="" padding_left="" margin_top="" margin_bottom="" animation_type="" animation_direction="left" animation_speed="0.3" animation_offset="" last="no"][fusion_content_boxes layout="icon-with-title" columns="1" title_size="25" heading_size="2" title_color="" body_color="" backgroundcolor="" icon="fa-network-wired fas" iconflip="" iconrotate="" iconspin="no" iconcolor="#ff9800" icon_circle="" icon_circle_radius="" circlecolor="" circlebordersize="4" circlebordercolor="" outercirclebordersize="5" outercirclebordercolor="#ff9800" icon_size="" icon_hover_type="pulsate" hover_accent_color="#ef7b00" image="" image_id="" image_max_width="" link_type="" button_span="" link_area="" link_target="" icon_align="left" animation_type="" animation_delay="" animation_offset="" animation_direction="left" animation_speed="0.3" margin_top="" margin_bottom="" hide_on_mobile="small-visibility,medium-visibility,large-visibility" class="" id=""][fusion_content_box title="How to configure a site-to-site VPN" backgroundcolor="" icon="" iconflip="" iconrotate="" iconspin="no" iconcolor="" circlecolor="" circlebordersize="" circlebordercolor="" outercirclebordersize="" outercirclebordercolor="" image="" image_id="" image_max_width="" link="" linktext="Read More" link_target="" animation_type="" animation_direction="left" animation_speed="0.3" animation_offset=""]
A site-to-site VPN connection lets branch offices use the Internet as a conduit for accessing the main office's intranet. A site-to-site VPN allows offices in multiple fixed locations to establish secure connections with each other over a public network such as the Internet.
In this video I will show you how to correctly and securely interconnect two remote locations to enable remote users to securely use a single server over an aggressive VPN link.
In the process of planning your site to site VPN implementation, you will have to ask yourself a few questions:
1 - Does one or both ends of has a dynamic public IP address? If so, you will have to use an aggressive mode VPN.
2 - Does both ends of the VPN connection have similar brand VPN routers (similar encryption options, if not you will have to decide on the device's matching options?)
In Main mode, the Phase 1 parameters are exchanged in multiple rounds with encrypted authentication information
In Aggressive mode, the Phase 1 parameters are exchanged in a single message with unencrypted authentication information.
Main mode is more secure. Aggressive mode might not be as secure as Main mode, but it is faster than Main mode. Aggressive mode is typically used for remote access VPNs or if one or both peers have dynamic external IP addresses.
In this case we will have to use an aggressive VPN connection since one of my branch offices (in QUERETARO) does not have a static public IP address.
Since we will be configuring 2 SonicWall Devices, let's name them QUERETARO (dynamic IP) and RA (Static IP)
- Configuration on the dynamic side (RA in my case)
On the dynamic IP SonicWall (QUERETARO) in my case:
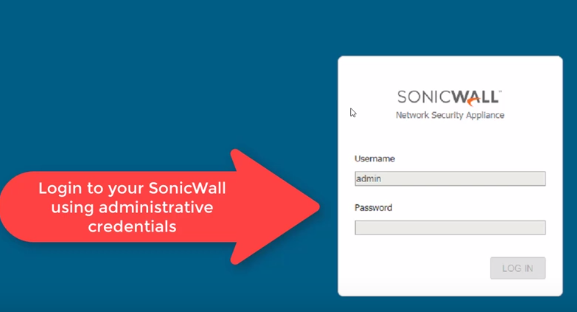
Login to the SonicWall firewall interface with your administrator credentials
d":5117} -->
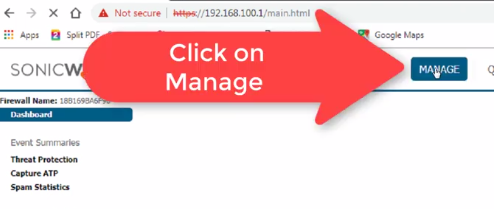
Click on Manage on the top menu
d":5118} -->
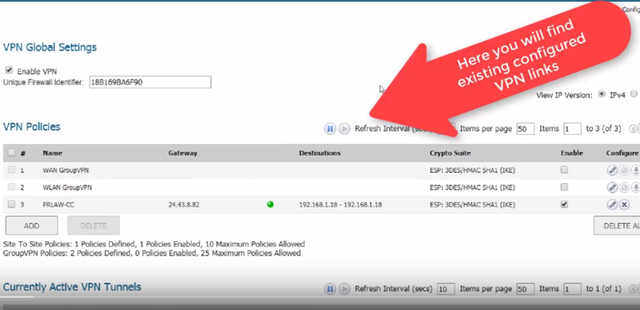
Click on VPN on the left-hand side menu and then click on Basic Settings
d":5119} -->

On the next screen you will find the already configured VPN connections and you will be able to add a new one,
d":5120} -->
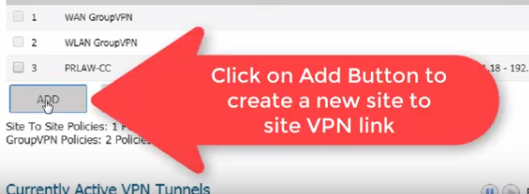
Click on the Add button to add a new site-to-site VPN
d":5121} -->
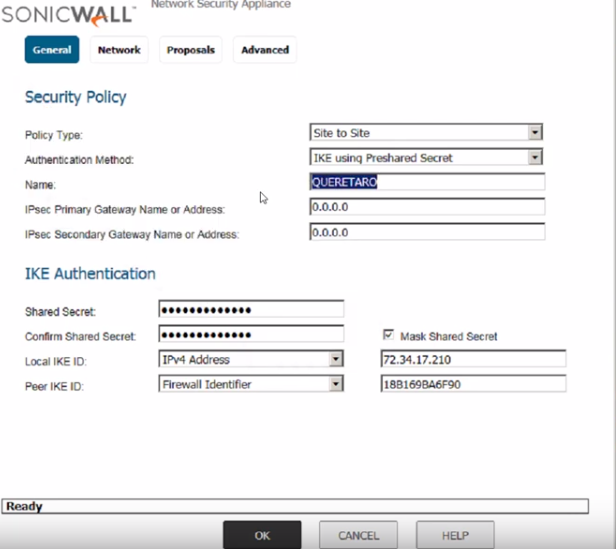
On the Dialog, on the General tab you will be able to configure the basics of your vpn connection, on the Field Name, enter a friendly name for the VPN connection, I will use RA for mine, in the "Shared Secret" field, enter the secret password required to authenticate both ends of the vpn link and confirm the secret on the below field, on the "IPsec Primary Gateway Name or Address" field enter the static public IP address or host name of the other end of the VPN, on the "Local IKE ID" field we would select Firewall identifier since the local SonicWall does not have a static IP or host name I can use on the "Peer IKE ID" field I am going to use the remote SonicWall (RA in this case) static public IP
d":5122} -->
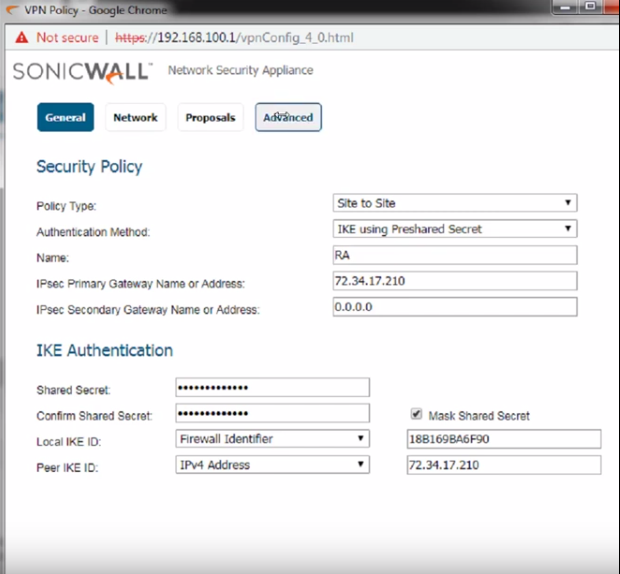
Now let's proceed to define the local and remote networks for QUERETARO's side of the VPN, this is necessary to ensure the SonicWall device "knows" how to handle the routing
Click on "Network" tab at the top
d":5123} -->
For the field "Choose local network" I am going to select the LAN subnet since I want all computers in QUERETARO to have access to RA's remote server over the VPN link
d":5124} -->
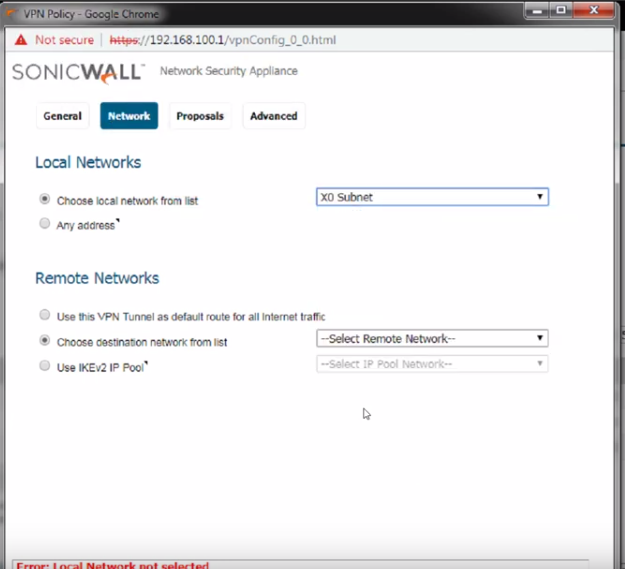
T
For the field "Choose destination network from the list" , I will chose "Create new address object..." since I just want to allow access to one server located at the RA site, we need to define its IP address on the remote network so the SonicWall knows how to do the routing
d":5125} -->
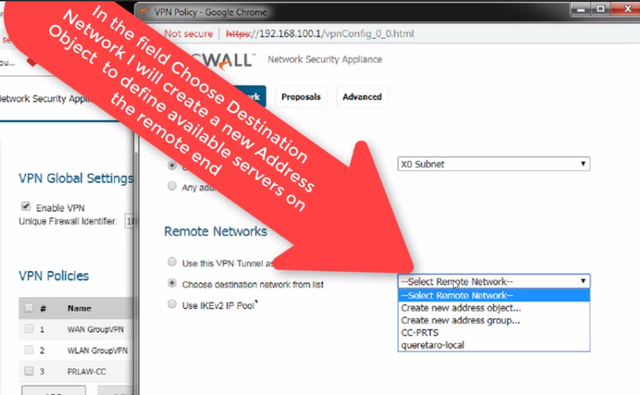
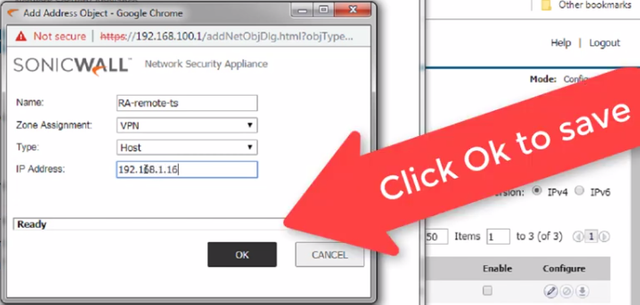
Once the "Add address Object" dialog opens,
Type a friendly name for RA's remote server, on the "Zone Assignment" field, select VPN , since this server can be only reached over the VPN link, on the "IP Address" field, enter the remote server's internal IP address on RA's remote local area network, once fulfill all the information requested Click "Ok" to finish adding the object.
d":5127} -->
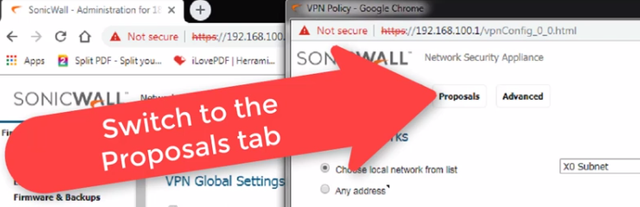
Now let's define the VPN negotiation parameters,
Click on "Proposals" tab at the top
d":5128} -->
For the exchange field, select "Aggressive mode", all de other fields we can define the specifics of the link negotiation, but most importantly, they need to be the same in both ends of the VPN
d":5129} -->
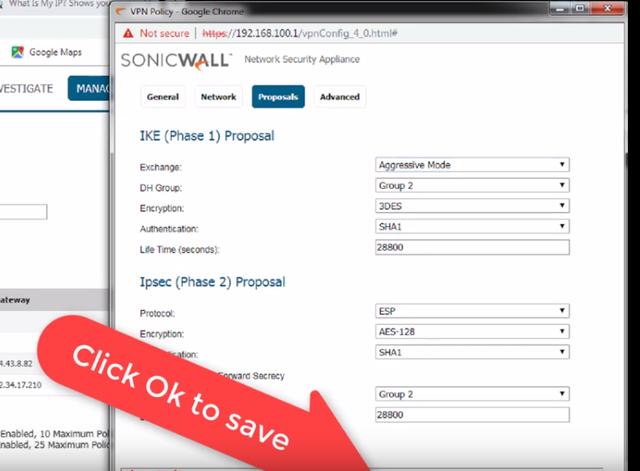
Click OK to complete adding the VPN.
2 – Let’s connect to the other SonicWall device, the static IP (RA side on my case)
Now let's connect to RA's SonicWall and configure the VPN on that side, the steps are similar
Login to the SonicWall interface with your administrator credentials
d":5130} -->
Click on "Manage" on the top menu
d":5131} -->
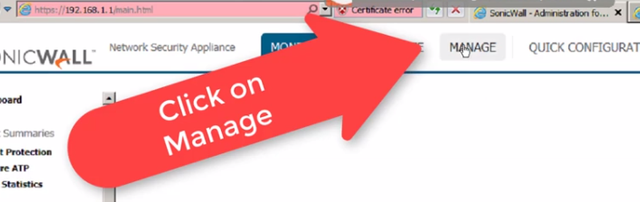
Click on "VPN" on the left-hand side menu and then click on "Basic Settings"
d":5132} -->
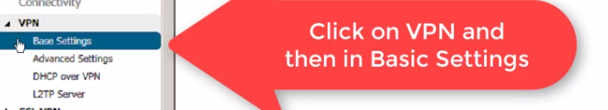
On the next screen you will find the already configured VPN connections and you will be able to add a new one,
d":5133} -->
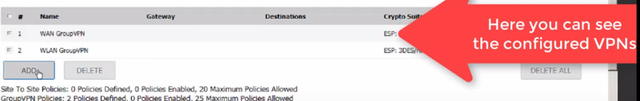
Click on the "Add" button to add a new site-to-site VPN
d":5134} -->

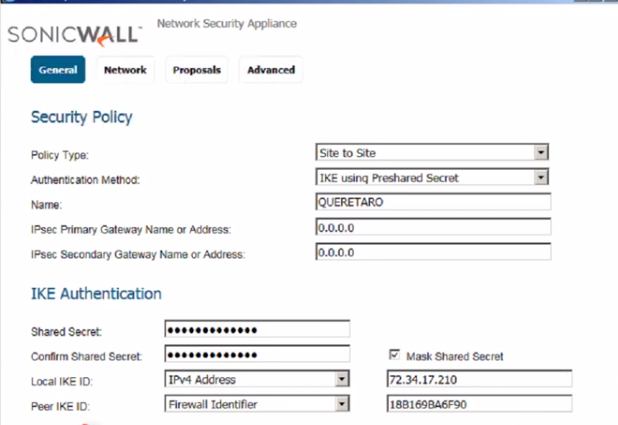
On the Dialog, on the "General" screen you will be able to configure the basics of your vpn connection
On the Field "Name", enter a friendly name for the VPN connection, on the "Shared Secret" field, enter the secret password required to authenticate both ends of the vpn link and confirm the secret on the below field, on the "IPsec Primary Gateway Name or Address" field leave it at 0.0.0.0 since the other end has a dynamic IP address, on the "Local IKE ID" field we would enter the SonicWall’s (RA in this case) static public IP, on the "Peer IKE ID" field I am going to use the remote(QUERETARO) Firewall identifier since the remote does not have a static IP or host name I could use ow let's proceed to define the local and remote networks for RA's side of the VPN, this is necessary to ensure the SonicWall device "knows" how to handle the routing:
d":5136} -->
Click on "Network" tab at the top
d":5137} -->

For the field "Choose local network”, I will choose "Create new address object..." since I just want to allow access to one server located at the RA site.
Once the "Add address Object" dialog opens, type a friendly name for the server we want to allow access to, on the "Zone Assignment" field, select LAN , since this server is located on the local area network at RA, on the "Type" field, select "Host" since I just one server to be accessible, on the "IP Address" field, enter the local server's internal IP address on RA's local area network
d":5138} -->
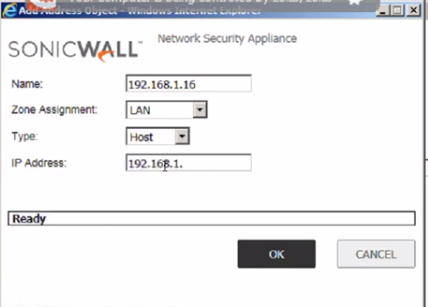
Click "Ok" to finish adding the object.
For the field "Choose destination network from the list" we will create another Address Object representing QUERETARO's local area ip range since we want all the computers on that site to have access to RA's server over the VPN link
d":5139} -->
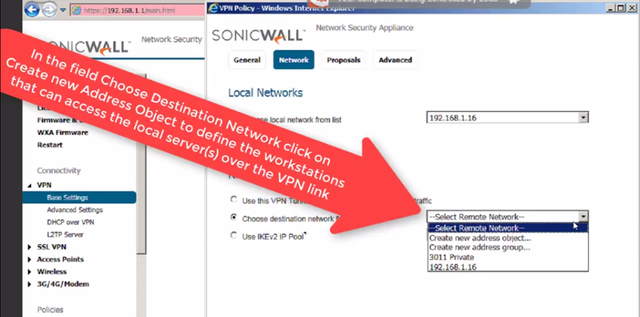
Once the "Add address Object" dialog opens,
Type a friendly name for QUERETARO's network we want to allow access, on the "Zone Assignment" field, select VPN, n the "Type" field, select "Network" since we want all the computers on QUERETARO to have access, on the "Network" field, enter QUERETARO's local area network, on the "Netmask" field, enter QUERETARO's local area network mask
d":5140} -->
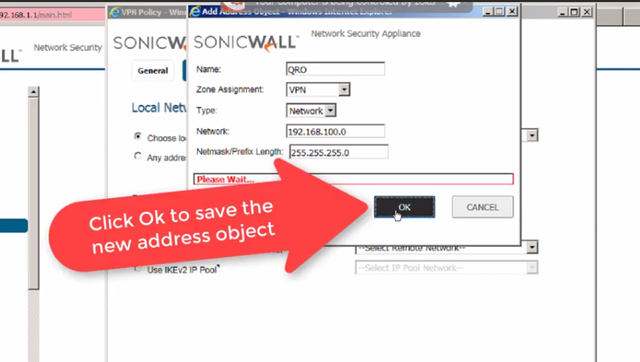
Click "Ok" to finish adding the object.
On "Proposals", make sure you have the same negotiation parameters we defined on the QUERETARO side and specially that the "Exchange" field is set to "Aggressive Mode"
d":5141} -->
Click "Ok" to complete adding the VPN link
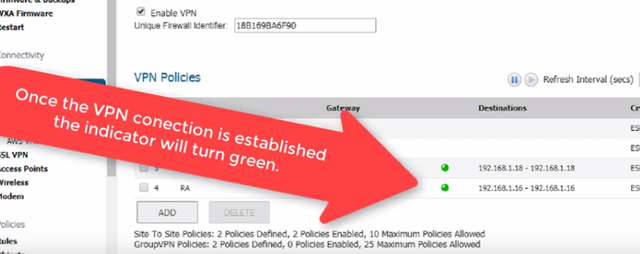
The connection process will take place and you will see a green indicator on the RA network and you should be able to ping and access the provisioned server over the VPN link.
d":5142} -->
[/fusion_content_box][/fusion_content_boxes][/fusion_builder_column][fusion_builder_column type="1_3" layout="1_6" spacing="" center_content="no" link="" target="_self" min_height="" hide_on_mobile="small-visibility,medium-visibility,large-visibility" class="" id="" background_color="" background_image="" background_image_id="" background_position="left top" background_repeat="no-repeat" hover_type="none" border_size="0" border_color="" border_style="solid" border_position="all" border_radius="" box_shadow="no" dimension_box_shadow="" box_shadow_blur="0" box_shadow_spread="0" box_shadow_color="" box_shadow_style="" padding_top="" padding_right="" padding_bottom="" padding_left="" margin_top="" margin_bottom="" animation_type="" animation_direction="left" animation_speed="0.3" animation_offset="" last="no"][fusion_widget_area name="avada-blog-sidebar" title_size="" title_color="" background_color="" padding_top="" padding_right="" padding_bottom="" padding_left="" hide_on_mobile="small-visibility,medium-visibility,large-visibility" class="" id="" /][/fusion_builder_column][/fusion_builder_row][/fusion_builder_container]
Posted from my blog with SteemPress : https://cubanhacker.com/sonicwalls-firewalls-come-licensed-for-multiple-site-to-site-vpn-connections-%ef%bb%bf/