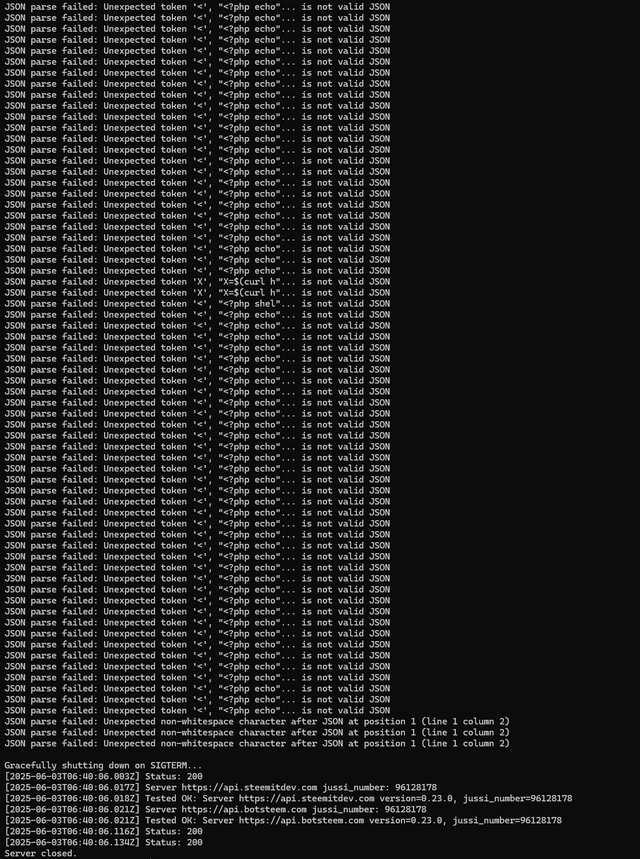
Steem Load Balancer Got Malformed JSON payload (scan or attack?)
The https://steem.justyy.com got a SIGTERM and I checked the logs and see quite a few requests with Malformed JSON payload.
I can see:
<?php echo ...
shell_exec
These are attack payloads — but the server is rejecting them:
- They’re probably from bots or automated vulnerability scanners
- They're testing if the server blindly executes incoming data (like a poorly secured PHP server might)
Example payloads you saw:
- ?php echo ... ? → looking for PHP code injection
- shell_exec("...") → looking for command injection vulnerabilities
Steem to the Moon🚀!
- You can rent Steem Power via rentsp!
- You can swap the TRON:TRX/USDT/USDD to STEEM via tron2steem!
- You can swap the STEEM/SBD to SUI via steem2sui!
- You can swap the STEEM/SBD to SOL Solana via steem2sol!
- You can swap the STEEM/SBD to ETH Ethereum via steem2eth!
- You can swap the STEEM/SBD to Tether USDT (TRC-20) via steem2usdt!
- You can swap the STEEM/SBD to TRX (TRON) via steem2trx!
- You can swap the STEEM/SBD to BTS (BitShares) via steem2bts!
- Register a free STEEM account at SteemYY!
- Steem Block Explorer
- ChatGPT/Steem Integration: You can type !ask command to invoke ChatGPT
- Steem Witness Table and API
- Other Steem Tools

Great post! Featured in the hot section by @punicwax.