Check your ROUTERS for Malware VPNFilter! - FBI tells users to Reboot/Reset routers
ALL users should reboot devices, but here's devices affected list:
- Linksys E1200
- Linksys E2500
- Linksys WRVS4400N
- Mikrotik RouterOS for Cloud Core Routers: Versions 1016, 1036, and 1072
- Netgear DGN2200
- Netgear R6400
- Netgear R7000
- Netgear R8000
- Netgear WNR1000
- Netgear WNR2000
- QNAP TS251
- QNAP TS439 Pro
- Other QNAP NAS devices running QTS software
- TP-Link R600VPN
Feds take aim at potent VPNFilter malware allegedly unleashed by Russia.
The FBI is advising users of consumer-grade routers and network-attached storage devices to reboot them as soon as possible to counter Russian-engineered malware that has infected hundreds of thousands devices.
FURTHER READING
Hackers infect 500,000 consumer routers all over the world with malware
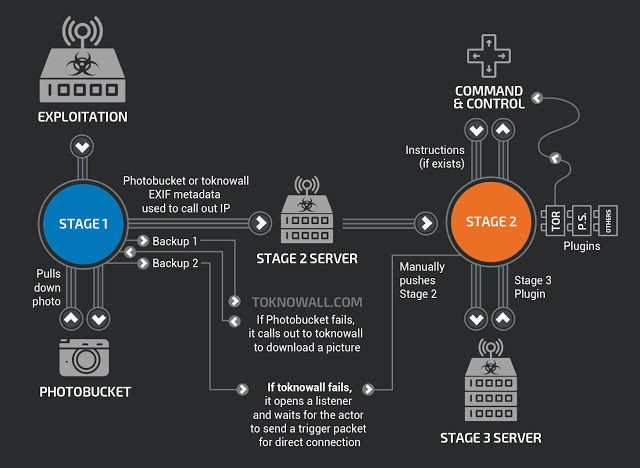
Researchers from Cisco’s Talos security team first disclosed the existence of the malware on Wednesday. The detailed report said the malware infected more than 500,000 devices made by Linksys, Mikrotik, Netgear, QNAP, and TP-Link. Known as VPNFilter, the malware allowed attackers to collect communications, launch attacks on others, and permanently destroy the devices with a single command. The report said the malware was developed by hackers working for an advanced nation, possibly Russia, and advised users of affected router models to perform a factory reset, or at a minimum to reboot.
FURTHER READING
FBI seizes domain Russia allegedly used to infect 500,000 consumer routers
Later in the day, The Daily Beast reported that VPNFilter was indeed developed by a Russian hacking group, one known by a variety of names, including Sofacy, Fancy Bear, APT 28, and Pawn Storm. The Daily Beast also said the FBI had seized an Internet domain VPNFilter used as a backup means to deliver later stages of the malware to devices that were already infected with the initial stage 1. The seizure meant that the primary and secondary means to deliver stages 2 and 3 had been dismantled, leaving only a third fallback, which relied on attackers sending special packets to each infected device.
Limited persistence
The redundant mechanisms for delivering the later stages address a fundamental shortcoming in VPNFilter—stages 2 and 3 can’t survive a reboot, meaning they are wiped clean as soon as a device is restarted. Instead, only stage 1 remains. Presumably, once an infected device reboots, stage 1 will cause it to reach out to the recently seized ToKnowAll.com address. The FBI’s advice to reboot small office and home office routers and NAS devices capitalizes on this limitation. In a statement published Friday, FBI officials suggested that users of all consumer-grade routers, not just those known to be vulnerable to VPNFilter, protect themselves.
Authorities and researchers still don’t know for certain how compromised devices are initially infected. They suspect the attackers exploited known vulnerabilities and default passwords that end users had yet to patch or change.
The advice to reboot, update, change default passwords, and disable remote administration is sound and in most cases requires no more than 15 minutes. Of course, a more effective measure is to follow the advice Cisco gave Wednesday to users of affected devices and perform a factory reset, which will permanently remove all of the malware, including stage 1. This generally involves using a paper clip or thumb tack to hold down a button on the back of the device for 5 seconds. The reset will remove any configuration settings stored on the device, so users will have to restore those settings once the device initially reboots. (It's never a bad idea to disable UPnP when practical, but that protection appears to have no effect on VPNFilter.)
There's no easy way to know if a router has been infected by VPNFilter. For more advanced users, Cisco provided detailed indicators of compromise in Wednesday’s report, along with firewall rules that can be used to protect devices. Ars has much more about VPNFilter here.
#spyware #hackers #tech #computers #router #routers #secure #hacking #internet #web #network #lan #wan #firewall #ip #ipaddress #antivirus
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
http://www.dslreports.com/forum/r31976501-The-FBI-kindly-requests-that-you-reboot-your-router-ASAP
Congratulations @overcome! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!