Why IoTeX will transform Internet of Things with its Blockchain
Early stage Blockchain for IoT
What is it?
A decentralised network for IoT powered by a privacy centric blockchain.
Background
The Internet of Things is rapidly emerging as the manifestation of the networked society vision - everything that benefits from a connection is connected. Yet this far reaching transformation is just the beginning. The number of connected IoT devices is expected to grow by 21% annually, rising to 18 billion in 2022. The global market of IoT is expected to grow from $170bn in 2017 to $560bn by 2022 at a compound growth rate of 26.9%. Many industry experts have pegged IoT as the next industrial revolution.
What problem does it solve?
Scalability
The majority of IoT devices are connected and controlled in a centralised way as of today. IoT devices are connected to backend infrastructure on public cloud services or on server farms to transmit data and receive control commands. The scale of IoT is bottle-necked by the scalability and elasticity of these backend infrastructures, servers and data centres. The substantially high operating cost of running IoT is unlikely to be covered by the profit from selling devices. Many IoT vendors cannot provide cost-effective devices and applications that are scalable and reliable enough for real world scenarios.
Lack of Privacy
IoT is expected to enable mass participation of end users on mission critical services such as energy, mobility, legal and democratic stability. Privacy challenges originate from IoT interacting with the physical world in a direct and automatic way, with the amount of data collected increasing substantially when it scales up. Some common threats include:
- Identification: Associating a consistent identifier.
- Localisation and tracking: Obtaining an individual's location.
- Profiling: Compiling information dossiers about individuals to infer interests by association with other profiles and data sources.
- Privacy-violating interaction and presentation: Conveying private information through a public medium and in the process disclosing it to an unwanted audience.
- Life cycle transitions: Devices often store hug amounts of data about their own history throughout their entire life cycle that could be leaked during changes of control spheres in a device's life cycle.
- Inventory attack: The unauthorised collection of information about the existence and characteristics of personal things.
- Linkage: Linking previously separated systems such that the combination of data sources reveals information that the subject did not disclose to the previously isolated sources and did not want to reveal
All of these common privacy threats are due to: data leakage at device level or data leakage during communication or data leak by centralised parties.
Lack of Functional Values
Most existing IoT solutions lack meaningful value creation. Being connected is the most used value position. However, simply enabling connectivity does not make a device smart or useful. A greater portion of the value that IoT produces comes from interaction, cooperation and autonomous coorindation of heterogeneous entities. Unfortunately, 85% of legacy IoT devices lack ability to interact or cooperate with each other due to compatibility issues. The data sharing for business and operational insights is nearly impossible.
What is the core technology?
Scalability
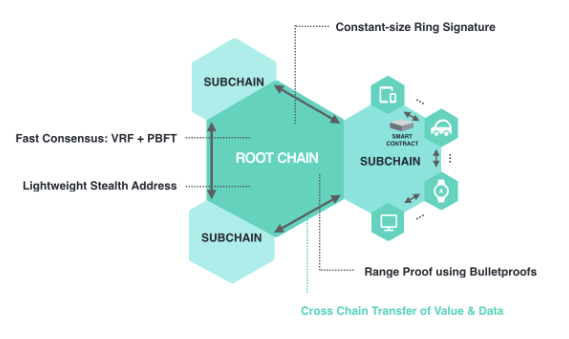
IoTeX uses blockchains in blockchains for a well balanced distributed network that maximises scalability and privacy in a cost-effective way. IoTeX is a network of many blockchains that are hierarchically arranged, where many blockchains can run concurrently with one another while retaining interoperability. In the IoTeX world, the root blockchain manages many independent blockchains, or subchains. A subchain connects to and interacts with IoT devices that share something in common. If a subchain does not function well, the root chain is unaffected. In addition, cross blockchain transactions are supported to transfer value and data from subchains to the root chain or from one subchain to another via the root chain.
The root blockchain is a public chain accessible by anyone with three main objectives
- Relay value and data across subchains in a privacy-preserving way to enable interoperability among subchains.
- Supervision of subchains
- Settlement and anchoring of payments and trust for subchains
Subchains
IoTeX comes with a framework for developing and provisioning a tailored subchain for decentralised IoT applications by encapsulating low layer primitives like gossip protocol and consensus mechanism. The permission mode, specification, parameters and transaction types of the subchain can be customised to fit into its application.
IoTeX subchains use an account-based model which is better for tracking state transactions.
Smart contracts are supported by the IoTeX subchains and run of top of the light and efficient virtual machine. IoTeX are evaluating WASM (Web Assembly), an emerging web standard for building high performance web applications. WASM is fast and can be made deterministic and san-boxed with some modifications as attempted by EOS. With smart contracts, IoT devices connected to the same subchain utilise the shared states in two ways
- First, devices can interact with the physical environment based on their subchain states (e.g. light bulbs turn on and off by themselves based on a "clock state" on the subchain
- Devices can mutate the state on subchains when the physical environment changes (e.g. thermostat updates temperature via a smart contract based on its sensor data)
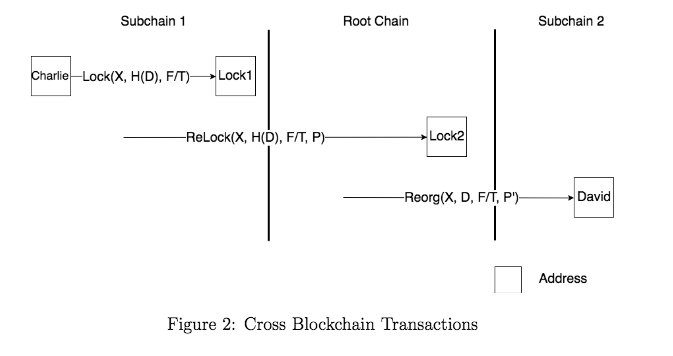
Cross Blockchain Communication
Cross blockchain communication is expected to be used with high frequency in IoT applications. There is always the need for an IoT device in a subchain to coordinate with another device in a different subchain. Again, limited by IoT devices low computation and storage footprint, IoTex is motivated to design cross blockchain communication in a fast and cost-effective way.
Pegging and Block Finality
Pegging is a mechanism for scaling the Bitcoin network via sidechains. It heavily relies on Simplified Payment Verification (SPV) and allows Bitcoins to effectively "move" from the Bitcoin blockchain to the sidechain and back. As of today. pegging serves as a primitive for almost all cross blockchain communication protocols (e.g. Cosmos, Lisk, Rootstock). Two separate pegging flows can be easily coupled together to make the so-called 2WP (Two Way Pegging) to transfer tokens back and growth. Block finality is the guarantee that the new block generated is final and cannot be changed. For IoT applications, cross blockchain transferring of value and data is expected to be fast and cost-effective which requires a finalising consensus mechanism on both root chain and subchains. IoTeX consensus achieves instant block finality.
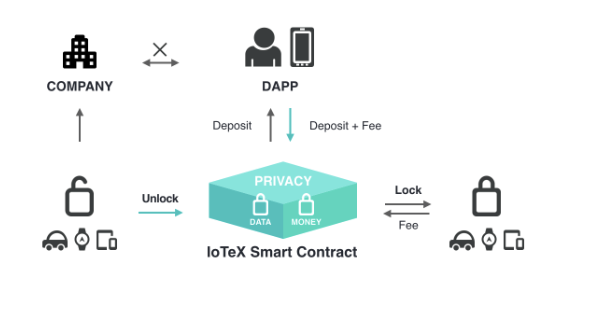
Privacy
IoTeX integrates stealth address for receiver privacy, ring signature for sender privacy and Pedersen Commitments for hiding transaction amount with the following innovations and improvements
- A lightweight stealth address scheme designed to exempt receivers from scanning the entire blockchain to be aware of incoming transcations
- Ring signature is optimised to make it compact in size with a distributed trusted setup
Speed
IoTeX blockchain has fast consensus with instant finality, greatly improving the throughput of the network and reducing transactional cost.
Architecture
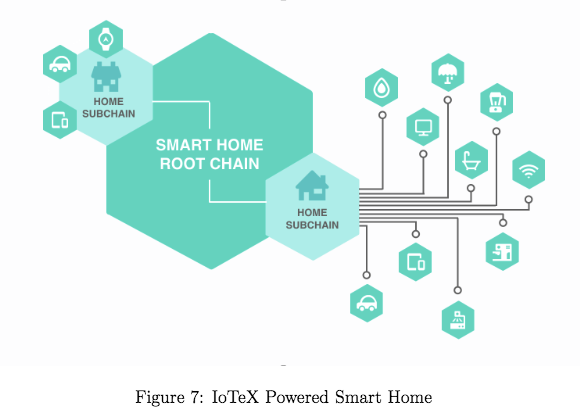
The flexible and lightweight IoTeX based system architecture is designed for key IoT applications across industries.
What are the use cases?
The IoTeX blockchain supports a variety of IoT ecosystems, shared economies, smart home, autonomous vehicles and supply chain.
Industry developers who will build on the IoTex blockchain include:
- IoT hardware manufacturers
- IoT device control system developers
- Supply chain data integrators
- Data crowd-sourcing vendors
- Autonomous car developers
Summary
IoTeX is a scalable, private and extensible blockchain dedicated for IoT with its architecture and core technology including:
- Blockchains in blockchains to maximise scalability and privacy
- True privacy on blockchain based on relayable payment code
- Constant-size ring signature without trusted setup and first implementation of bulletproofs
- Fast consensus with instant finality based on VRF and PoS for high throughput and instant finality
- Flexible and lightweight IoTeX based system architectures