UNCLOAK - ELIMINATING CYBER THREATS USING BLOCKCHAIN

Introduction
It is said that "Development in IT (Information Technology) sector has lifted much of the work from the shoulders of people"
It has enabled easy management of various things like accounts, data costing, communication, data storage, business, banking etc. 70% of the companies take help from this technology in order to increase their productivity and decrease the amount of workload on the human force. So one can understand how much nowadays cooperate world relies on Computers and Internet. If it stops working for a day, than half of the world will stop working, and this will affect world markets very extensively.
So, if internet not working for a day can have such a huge impact, then one can think of, what if nodes of internet and technology gets attacked by electronic bugs and viruses which can harness your data and can take down terminals which may lead to stoppage of work and misuse of that data for the destructive purpose. Also through this, one can leak company's classified news, data, history etc. This can have extensive effects on companies, governmental bodies, private agencies, corporate banks, the world market and directly on all the people living!
Viruses, malware, worms, Spywares, Trojans are various forms of digital gems that can make your network ill. The Internet is solely responsible for its emergences, spreading and mass destruction. It can get downloaded in one's device through the internet and can either alter your data or leak your data to benefit its producer. As the internet is used by almost all human beings on earth, it's outrage can be disastrous like an outrage of Wannacry Virus in the all the ATM systems of the world, that disrupted many countries financial system.
Solution offered
UNCLOAK a blockchain based cybersecurity threat management company that will cyber search all the possible gems in the network, locate it without it reaching to end points where it can eating the systems.
UNCLOAK will find threats that exist in the system. It brings security personnel and Artificial Intelligence (AI) both together to detect this threat. The human force that finds this vulnerabilities will be rewarded with companies token. But the database keeps on getting updated by the AI. Thus the newly produced gems get detected faster than earlier it used to and thus end user is protected against these threats that may interfere in their network.
Ethical hackers are known as Hunters of the susceptibility in the network. They will be informed about the threat that is going to be released in nodes. They have to vote in for it being a threat or not. On successful identification, they will be rewarded with company released tokens. Whereas AI keeps surveillance tracker on, where it checks suspicious things which are getting transferred in the web and also in dark world of web where only unethical hackers trade. Than appropriate action will be taken on those identified objects.
UNC and UCC are the two tokens released by the company. UCC will be as a reward for the ones who detected the infections and UNC will be trade-able to the ones who ask for cybersecurity services.
ICO and the Team
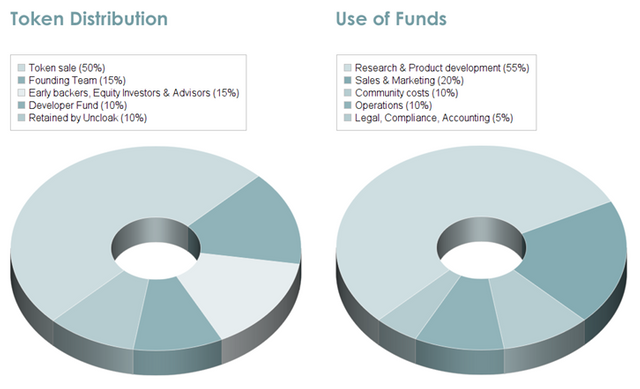
UNCLOAK realized UNC token will be on sale to the end-user who may be susceptible of getting attracted with the disease. After 50% of it being consumed in token sale, 10% will be retained for it to be converted back to UCC and used as a method to appreciate one's effort, while remaining will be kept reserved for founding team, for inviting more hunters etc. i.e for company's development, and for advisors and all. Funds collected will be used in the development of the company.
Conclusion
Every coin has two sides, so also this internet technology. One can connect to their friends and family living thousands of meters away but one can also get connected to data leakage system that may affect your computers health etc. With growing use of the internet, getting attacked by malicious programs will also increase. Thus a Threat Detection System was required that can quickly find the incoming army of viruses before it reaches to the users and start affecting their systems.
Thus it is said that 'It is necessary to find the cause of the disease to cure it! Similarly, It is necessary to find emerging vulnerabilities before thinking of eliminating it.'
Website - https://uncloak.io/
Whitepaper - https://whitepaper.uncloak.io/
Telegram - https://t.me/uncloakio
ANN - https://bitcointalk.org/index.php?topic=3375925.0
Published by - smithjones
Profile - https://bitcointalk.org/index.php?action=profile;u=1936039
“Identify Threats, Protect Networks!”
it will do good in the future