Gathering OSINT Like a Hacker (Hacking-103a)
Today I'm going to teach you to perform recon on a REAL organization. This is the first(and most important) step in hacking. The organization we'll be performing recon on is hyatt.com. They have an open bug bounty program which allows us to do what's covered below legally. By learning how to perform recon you'll discover the various attack surfaces of a target and where they're weak/strong. This is the most important phase and often the most over looked. So what are our goals when performing recon? There are quite a few. In general we want to gather:
IP Addresses(to find machines to potentially scan & attack)
WHOIS information
Social media accounts of employees
information from breach data
data that is not supposed to be accessible by the public but is
anything else about the target available on the internet
Doing all these things are what is known as passive recon as it does not leave a trail on the organizations machines. All the above can considered part of gathering Open-Source Intelligence(OSINT). So how do we do all this?
Gathering OSINT:
Before we begin actively scanning our target we need to gather as much openly available information as possible. We will do this by using the following(all explained in detail):
WhoIs
We use whois to find information about the site owner(which can include email, name, address and phone number), the date the site was created, & info about the domain & hosting provider(so we can possibly attack them). Using whois is very easy. Simply go to a terminal and type:
sudo apt-get update && sudo apt-get install whois
whois domain.com (where domain.com is the name of the website)
You should see something similar to the following
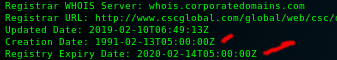
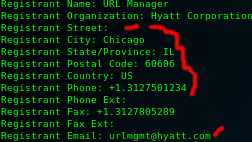
Creation date shows you how long a site has existed. This is useful b/c the longer the site exists the more information you are likely to find even if it was changed/deleted. You can check for old site pages at waybackmachine.com
Reg Expiry date tells you when they need to renew the domain. If they don't renew it by that time it is possible to seize control of that domain.
Reg Email tells you the email likely used to log in to the registrar. This email can be targeted by sending malware to it or be combined with breach data(as covered below) to find potential passwords, thereby possibly allowing you to login with this information.
So we now have all this information. Let's now find ip addresses to attack.
nslookup/ping
NSlookup/ping commands tell us the ip addresses used for a website. We can then take this ip addresses and start running scans against them. To run nslookup/ping go to terminal and type:
- nslookup domain.com
OR
- ping domain.com
You should see something like below:
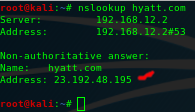
Sometimes this number will change if nslookup/ping is run multiple times. This can indicate the presence of a load balancer or a proxy service like Cloudflare. If you find a service like Cloudflare is being used(which is used to prevent DDOS attacks and hide the true IP address of a system) you need to use a program like Cloudfail to uncover the true IP address. Without the true IP address you will be unable to scan the real system for vulnerabilities. This does not mean that you will not be able to find a way in but it limits your options for hacking it to things like social engineering, password reuse, and sending malware to a user.
Social Media
Next we want to analyze social media. Doing this can give us ridiculous amounts of information including:
all the employees we could target(as well as the ability to target them through social-engineering/sending malware)
the type of infrastructure and systems a company uses. Some examples of this are:
- if you look on LinkedIn and see that they have several people listed as an Azure engineer you can know they're running Azure.
- if you look on job websites and see the requirements of people they're looking to hire you can see what type of systems they use.
Google Dorks
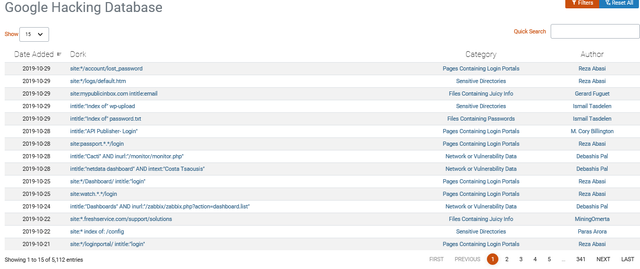
Google dorks are search queries for Google that can reveal vulnerable systems or sensitive info that isn't supposed to be available but is. This can include everything from supposedly hidden files, login pages, and more. The best way to learn how to use them is to practice searching with them. Thousands of options are available and can be found here. Below is an example of the dork database:
Analyzing Breach data
The following section is one of my favorite parts. It is extremely powerful. As you may recall above in my whois search of hyatt.com we found the email "[email protected]". It would be really useful to see if this email has ever been involved in a data breach. There are two ways of accomplishing this. One leaves a slight trail and has some limitations while the other is extremely powerful and requires some investment and technical know how. Both will be covered.
Searching Via HaveIBeenPwnd.com
There is a website called HaveIbeenPwnd that will let you search through breach data to see if an email address has ever been involved in a breach. In the below example I searched for the email given to us in the whois search and what do you know it has been involved in 3 breaches! 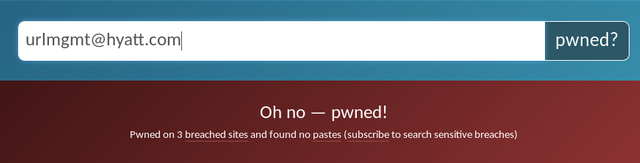
Once you find an email that has been involved in a breach you now need to find the actual info leaked which could be passwords, personal information, and more. In the website above the specific breach information is located if you scroll down. Once we have this we now need to find a way to access or download the breach data
Searching/Downloading Breach Data
Now that you know the breaches an email address was part of you need to find them and search them. You can do this by paying $5 and using a website like snusbase or even better by going to a website like raidforums and paying about 5 bucks per database which you can then download & search securely without leaving a trail. Downloading and searching breach data will be covered in-depth in a soon to come tutorial. You can download virtually all the databases you could need for about $100-$150.
It is a worthwhile investment every hacker or pentester should invest in. Even better it is legal to have provided you are doing "security research" and not using it for anything malicious. You can find everything from addresses, social security numbers, passwords, all accounts tied to a single email address/password, and much more!
This information can be used to tailor social engineering attempts to an employees personal/work email, blackmail an employee(if they happen to be found on an incriminating website like Adult Friend Finder or Ashley Madison), and tie seemingly unrelated accounts to each other(via searching for an identical password and all accounts tied to that password).
Conclusion
You now have some very powerful ways to perform recon on an organization. This phase is most likely the one you'll spend the greatest amount of time on. There are ways to make this more organized and quicker through tools like Maltego(which will be covered in a later post). The next tutorial will be even more hands-on as we will actively scan a real life vulnerable machine! As a final note these skills are very powerful and should only be used with good. If you misuse these tools one way or the other karma will catch up with you. As always if you have any questions or comments leave me a comment and don't forget to upvote if you found it useful. Until next time be safe out there and happy hacking!
Very good tutorial! Just gave you a follow. Should have discovered your blog earlier
Hey thanks a lot I appreciate the kind words. Glad to have you as a follower! I have so much more tutorials planned and as we move forward they will get even better so stick around :)