How to setup a secure VPN based EOS.IO network
This week we started a new endeavor on the EOS BP Infrastructure telegram group to test secure ways to build our network and avoid possible DDoS attacks upon the EOS network launch.
To understand why this approach is useful to avoid DDoS attacks please read this article:
https://steemit.com/cryptocurrency/@eostribe/addressing-ddos-risks-at-eos-launch
This tutorial is made possible by collaboration with @cryptolions, @eluzgin, @xebb, @jemxpat, @eoscafe, @eosvibes
Let's break this down on the required steps to build a "very-secure" EOS network between trusted peers.
Requirements:
- EOS.IO - DAWN-2018-04-27-ALPHA or newer
- Wireguard
Install Wireguard on Ubuntu
$ sudo add-apt-repository ppa:wireguard/wireguard
$ sudo apt-get update
$ sudo apt-get install wireguard
Wireguard key generation
WireGuard requires base64-encoded public and private keys. These can be generated using the wg(8) utility:
$ umask 077
$ wg genkey | tee privatekey | wg pubkey > publickey
Wireguard setup
Save the text code below on /etc/wireguard/wg0.conf
[Interface]
Address = 192.168.10.1/24
DNS = 1.1.1.1
SaveConfig = true
ListenPort = 5555
PrivateKey = CCIt1u.....
[Peer]
PublicKey = tIoYj42V.....
AllowedIPs = 192.168.10.2/32
Endpoint = peer-public-endpoint.com:port
[Peer]
PublicKey = tIoY5hsjc.....
AllowedIPs = 192.168.10.3/32
Endpoint = other-peer-public-endpoint.com:port
.
.
.
Modify wg0.conf to inform your private key contained on the privatekey file generated on the previous step and add the public key from all other peers in the network (on the [Peer] sections, repeat for each one)
Use wg-quick to enable wireguard
$ sudo wg-quick up wg0
If you need to add more peers just edit /etc/wireguard/wg0.conf and run:
$ sudo ip link del dev wg0 && sudo wg-quick up wg0
Test Wireguard
$ sudo wg show
You should see something like this:
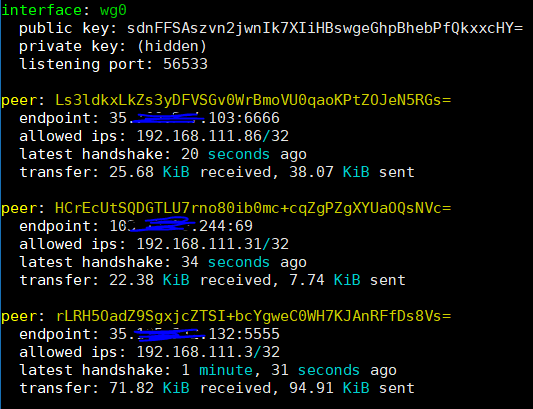
EOS.IO Peer-key secure setup
To add another layer of security we can whitelist the connections allowed on the EOS node using the built-in peer-key feature.
Create a new key pair for peering purposes
$ cleos create key
Edit you config.ini file and add your peer key pair and the public key from other peers on peer-key (one line for each with double quotes)
allowed-connection = specified
peer-private-key = ["MY_PEER_PUBLIC_KEY","MY_PEER_PRIVATE_KEY"]
p2p-peer-address = 192.168.10.2:9876
peer-key = "PEER1_PUBLIC_KEY"
p2p-peer-address = 192.168.10.3:9876
peer-key = "PEER2_PUBLIC_KEY"
.
.
.
Launching
Launch the network without block production by setting enable-stale-production = false.
Only bios node should produce when he joins at the end of the meshing process.
Troubleshooting EOS.IO handshakes
If you see something similar to the message below on the logs it usually mean that the peer hasn't added the correct peer-private-key settings on the config.ini file
Peer xyz:9876 - 17cc856 sent a handshake with an unauthorized key: EOS1111111111111111111111111111111114T1Anm.
One can check the current peers connections in order to verify signatures on the /v1/net/connections api endpoint if the eosio::net_api_plugin is enabled.
Finally eosio boot node can join and jumpstart the chain. Those measures will allow the eosio node IP to be undisclosed until the final moment, drastically reducing the window for a DDOS attack on the boot node.
Bonus: You can still add HTTPS support using self-signed certificates by following our last tutorial here

Today on May 2, 2018 and exactly one month before EOS main net launch a group of BP candidates have successfully conducted an experiment of establishing a mesh network of BP nodes over secure VPN network supported by WireGuard software.
Participated in experiment:
EOS Tribe
EOS Cafe
EOS Rio
EOS New York
EOS Mesoamerica
Special thanks to @jemxpat - friend of EOS for his technical expertise and guidance on setting up VPN network!
Great work guys and I am looking forward to our Dan and Paul here are EOS UK getting involved in this next week. In the interim my gift (and curse) is proof reading so thought I would just flag this question about maybe there is a missing word here, see screenshot http://bit.ly/2HVmLnq Probably most readers would know what you mean but this is my way of letting you know I have read every word you've written, and offering some level of contribution even if I can't get down and grep'y with you tech meisters!
Keep up the great work, what an amazing piece of collaboration from this amazing community :-)
Thanks a lot Roger, you were right! We just fixed it :)