Protect Your Sensitive Data in Windows/Linux using Veracrypt Encrypted File Containers(PersSec102)
In my last post I taught you how to use military grade Full Disk Encryption(FDE) to make sure you data stays safe from thieves or the government. Though FDE is powerful there is one BIG problem:
If an attacker(most likely a sophisticated one) has access to your device while it is powered on, FDE won't help you.
This is because your password(key) is stored in RAM and can be dumped with the right tools. The only way to make sure that doesn't happen is to immediately power your device off.
So what can we do to protect our data while our device is on?
The answer is simple. Use a Veracrypt encrypted container for our extra sensitive data. The entire process takes only about 4 minutes to start encrypting(which will then take another 30 min to a day depending on the size you choose) Let's get started!
Installing Veracrypt:
First you must download the install file. You can do that here
and choose either the Windows or Linux file
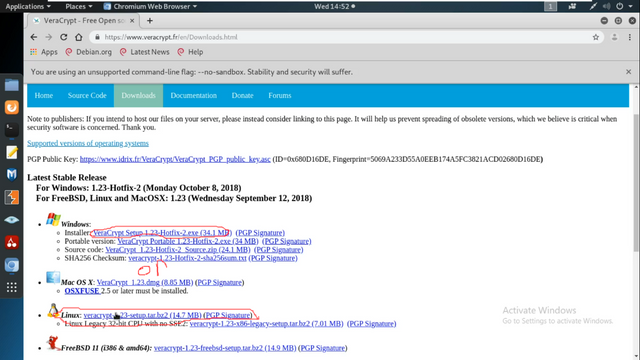
Installing in Windows:
1.) Download the executable and install it using default options
Installing in Linux:
1.) Double click file and it should open up window with 4 different files. Drag and drop file labeled veracrypt-1.23-setup-gui-x64 to location of your choosing
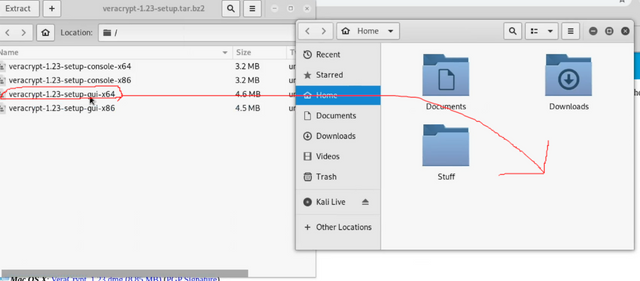
2.) In terminal go to location you downloaded it using cd command and type the following:
- chmod 755 veracrypt-1.23-setup-gui-x64
(if filename is different then make sure it matches) - ./veracrypt-1.23-setup-gui-x64
Some boxes will pop up. Click I agree, Install and OK when relevant
You should now something similar to this:
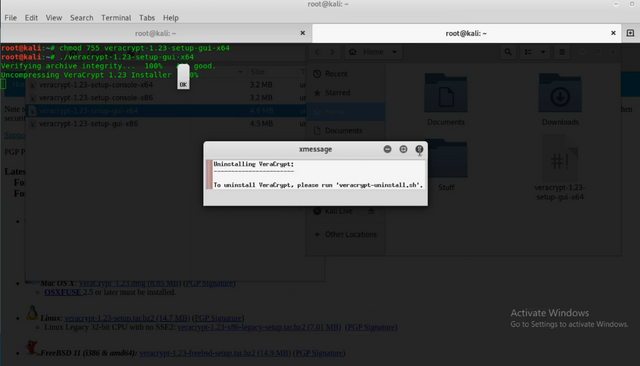
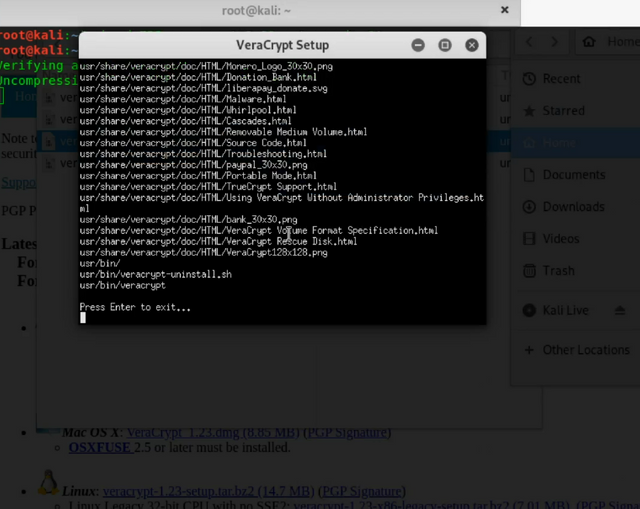
Click the X and a black box should appear. Press Enter.
Congratz you've now installed it on Linux. You can open it by hitting Windows key on your keyboard and typing Veracrypt or through the start menu and typing. The next portion works for both Windows and Linux.
Creating Your Container
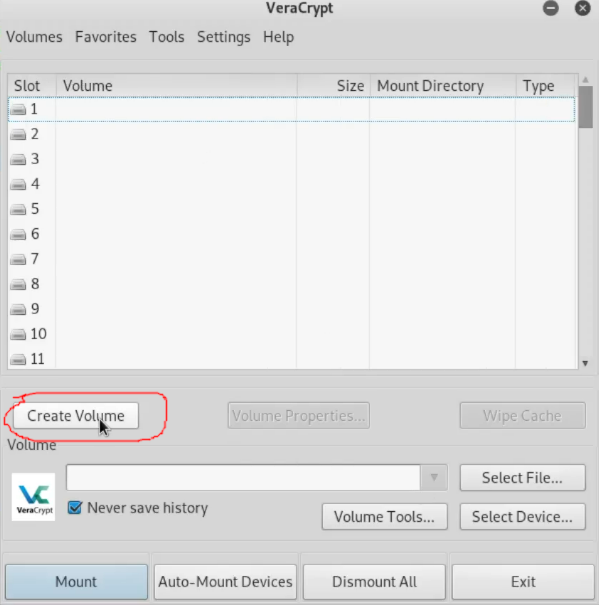
First click on Create Volume
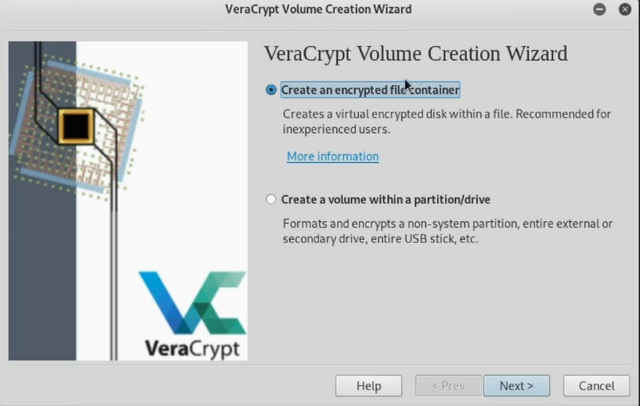
Next click on Create an encrypted file container
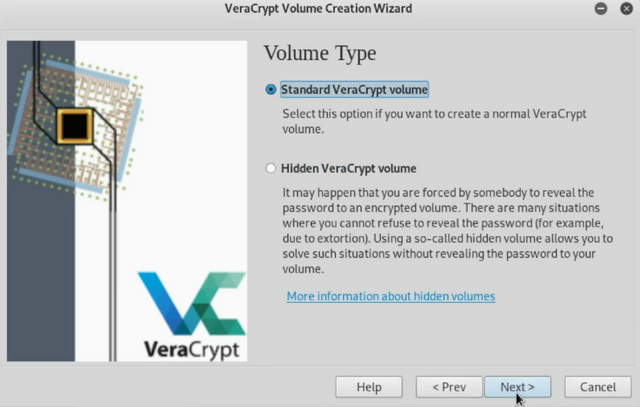
Next choose Standard volume
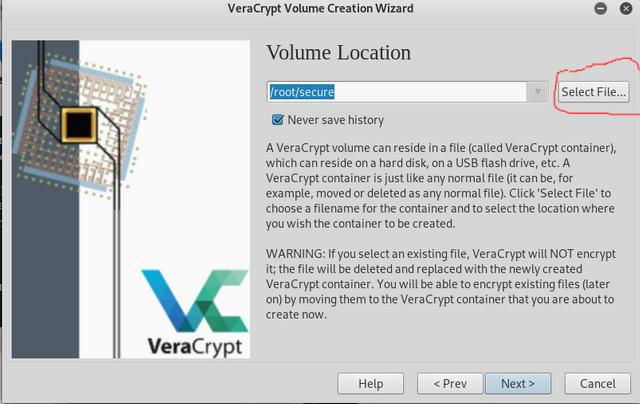
Now we need to create a file. In Windows right click on desktop and create new text file. In Linux in the terminal type: touch secure
Now in Veracrypt program click on select file and go to where your new file is and select it. An icon will pop up saying it already exists. Click Replace then click Next
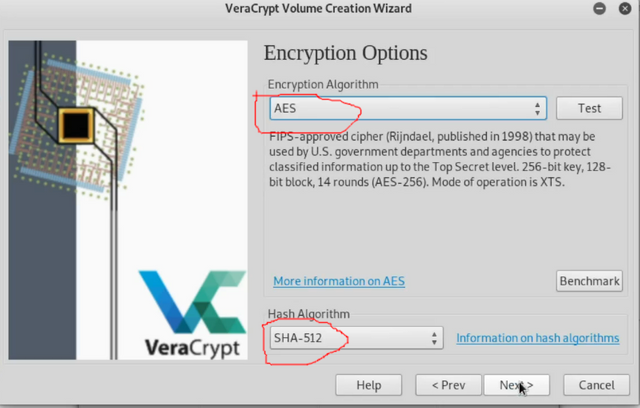
Now on encryption options make sure AES and SHA512(or SHA-256) or selected. Click Next
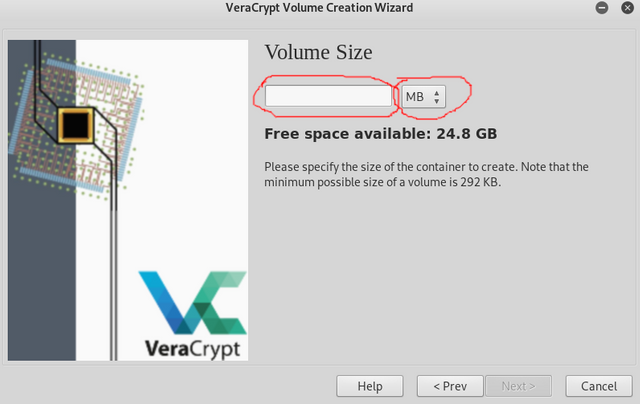
Now we need to choose how big you want the volume to be. This number is up to you based on your needs. Type the size you want and MB, GB, TB, etc... then click next.
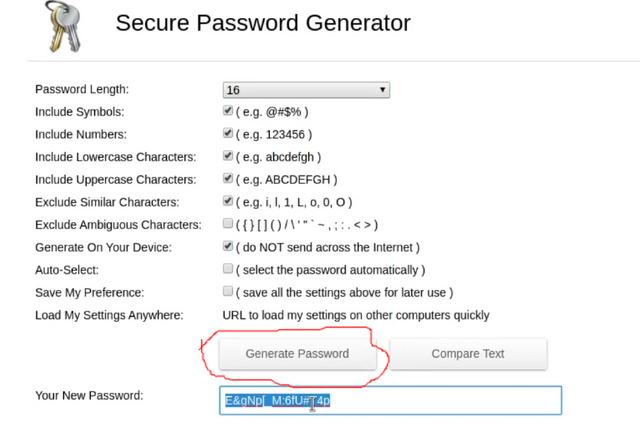
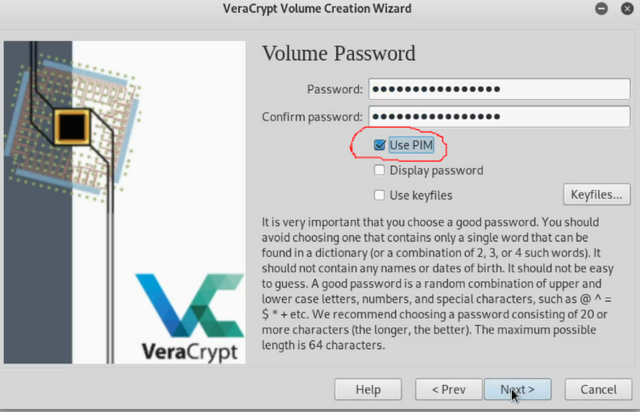
Now it's time to choose our volume password. This is very important to do correctly! Go to https://passwordsgenerator.net and choose at least a 16 character password. Copy it into password box and make sure "Use PIM" is selected and click next. DO NOT USER THE SAME PASSWORD YOU USE FOR YOUR SYSTEM!!!
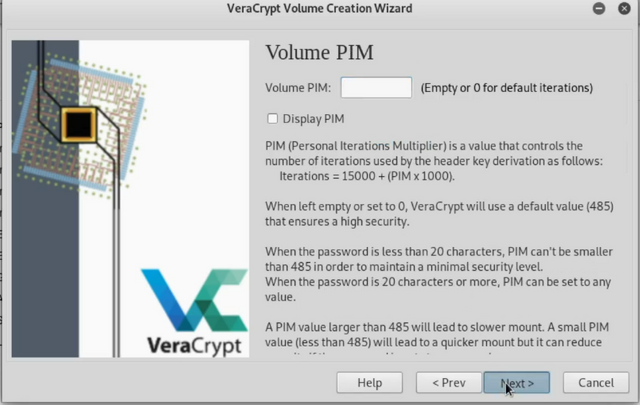
Leave Volume PIM blank and click Next
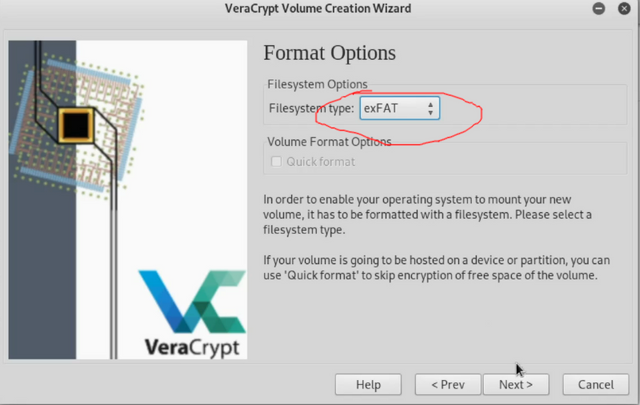
Choose the format you want( I recommend NTFS or exFAT especially if you're storing files over 4GB) and click Next
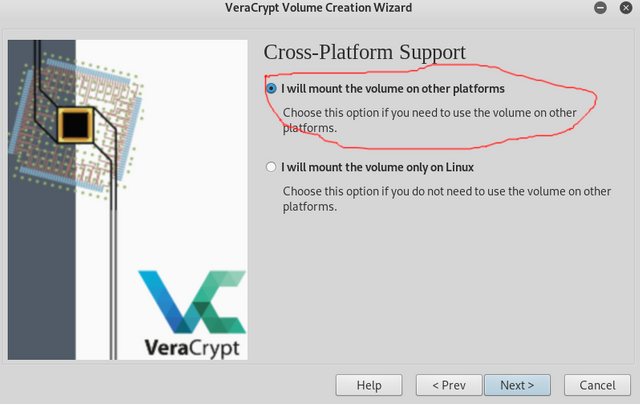
For Cross platform support I recommend you choose "I will mount on other platforms"(this will let you make your data portable and able to be used on various platforms.(If this option doesn't show up don't worry about it)
Next we need to move our mouse around until the bar is completely filled and then click format. Click Yes to any pop ups and it will begin creating it.
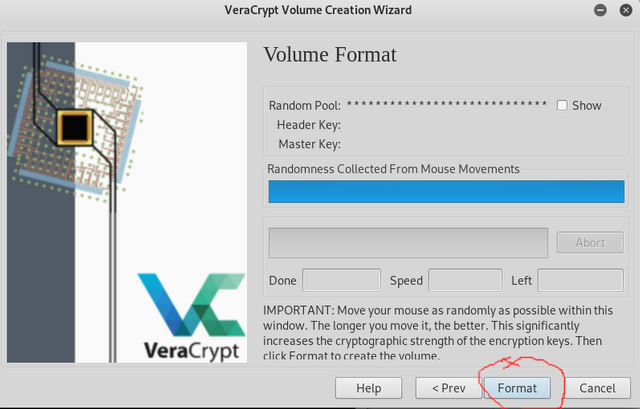
Once it's done a pop up will appear click OK then exit.
Mounting it:
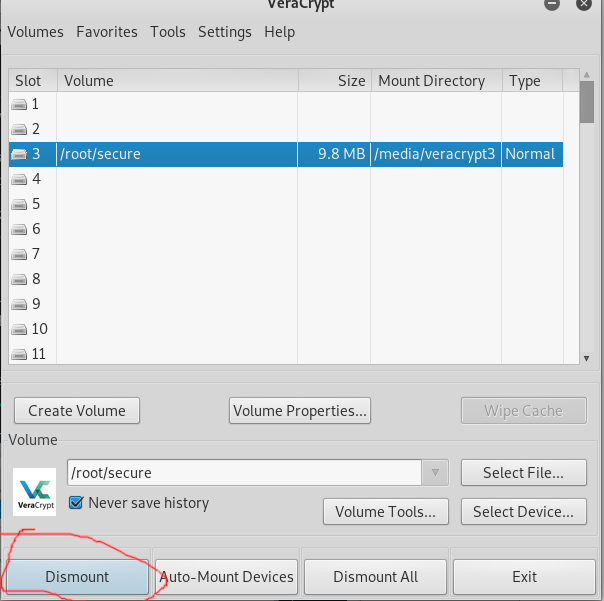
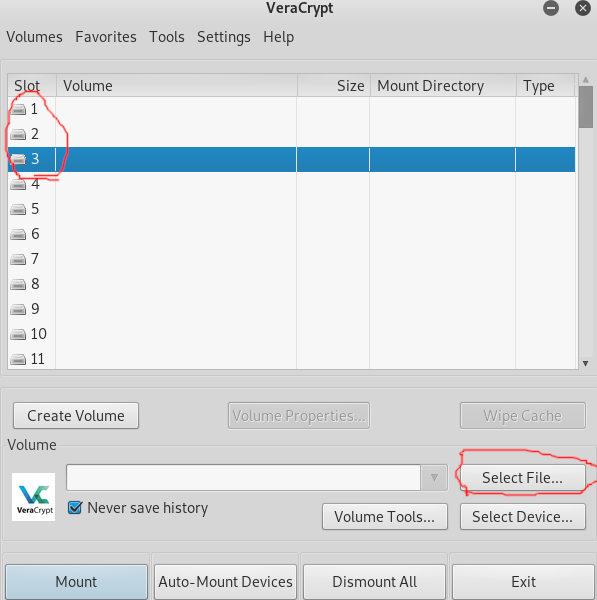
Go into Veracrypt click on a numbered drive(the drives going down from on to 11) and click select File
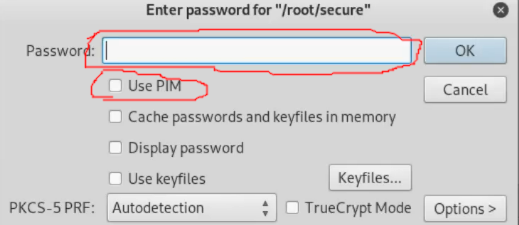
Now it's time to enter our password and select Use PIM and hit OK.
Our container is now available via the file explorer menu(hit Win key and type Files or File Explorer or go to start menu and do so-both Win/Linux). The volume will look like so.
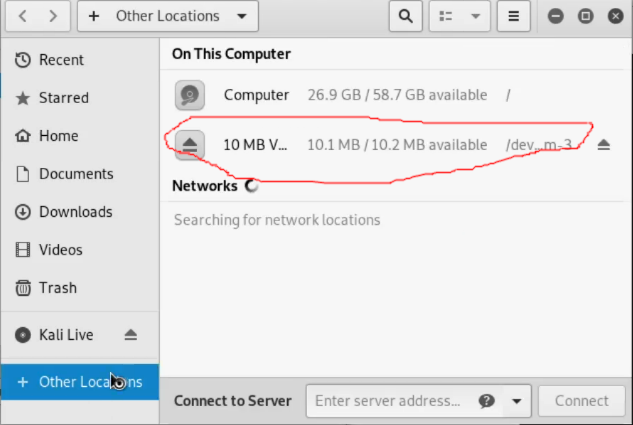
You can now use this like any other flash or hard drive by simply dragging and dropping your files in it and clicking Dismount when done using it.
When you click dismount the drive shown in file explorer will disappear(however the actual encrypted file will remain where you left it.)
You now have an encrypted container that you can move between computers for all your most sensitive data.
Only keep it open when needed.
In my future tutorials I'll teach you how to hide data inside of an image or mp3 that no one can tell is there and forensically delete files. I hope you enjoyed this tutorial if you did please upvote and as always comment if you have any questions or, well... comments. Get it? Or well? ;)