How to use Proxies to deal with DDos attacks?
In today's world, DDoS attacks (Distributed Denial of Service Attacks)have become a major threat to businesses and websites. They will flood the target server with a large amount of forged traffic, causing the server to be unable to process normal requests, thus bringing down websites and disrupting business. Proxies can be used not only to hide your real identity and access other websites, but also play an important role in defending against DDoS attacks. In this article, we will discuss how Proxies can be used in DDoS defense and how we should use them.
Why do DDoS attacks happen?
Attackers usually implement DDoS attacks for the following purposes:

Business Competition: Malicious competition exists in some industries (e.g., the gaming industry), where competitors disrupt their rivals' online services through DDoS attacks, leading to a massive flow of customers from their rivals in order to gain an advantage in business competition.
Extortion: By attacking a targeted website, the attacker blackmails the website owner, demanding a ransom to stop the attack.
Demonstration or political motivation: Certain organizations or individuals conduct cyber protests through DDoS attacks to attract public attention or to express their political advocacy, etc.
Principles of DDoS attacks
DDoS attacks essentially hit a target server with a large amount of forged traffic in an attempt to exhaust the server's resources and render the service unavailable.
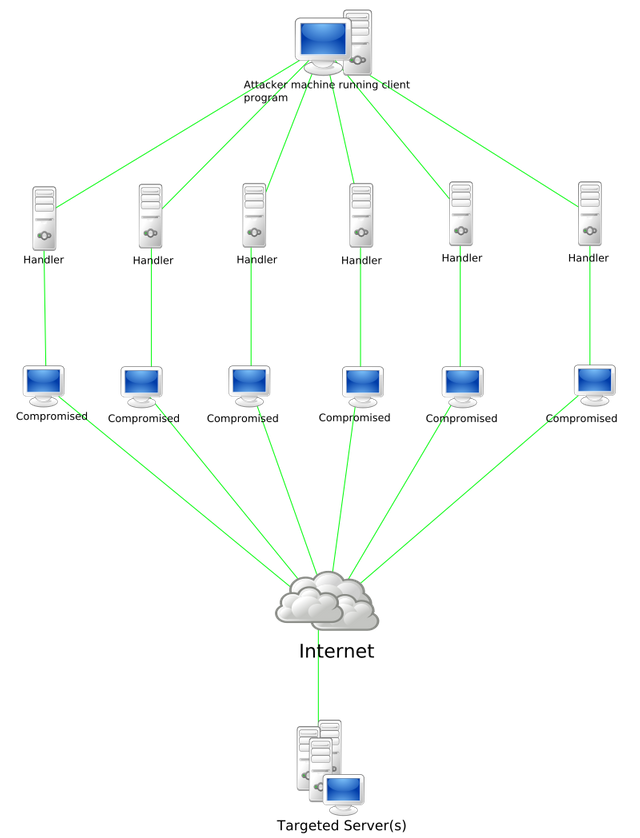 In a DDoS attack, the attacker exhausts the resources of the target system or website by controlling a large number of network devices (e.g., personal computers, servers, and IoT devices) and sending out massive access requests to the attack target (e.g., websites, web servers, network devices, etc.) that are not out of normal business needs, so that the user cannot use the system or access the website normally, thus achieving the destruction of the website or online service, so as to disrupt the normal operation of the website or online service.
In a DDoS attack, the attacker exhausts the resources of the target system or website by controlling a large number of network devices (e.g., personal computers, servers, and IoT devices) and sending out massive access requests to the attack target (e.g., websites, web servers, network devices, etc.) that are not out of normal business needs, so that the user cannot use the system or access the website normally, thus achieving the destruction of the website or online service, so as to disrupt the normal operation of the website or online service.
Attackers can take advantage of security weaknesses, such as malware or vulnerabilities in the attack target system, to take control of devices (i.e., "puppet machines") that access the Internet on the attack target side. At the same time, remote commands are sent to the controlled device, allowing it to launch DDoS attacks on the target website or service. It is often difficult to distinguish the access traffic of the controlled device from normal access traffic. This kind of attack will not only lead to downtime of enterprise websites and services, but also cause financial losses, brand reputation damage, and may even affect the entire supply chain. Without effective defenses, enterprises may face tremendous economic and security pressures.
How to recognize a DDoS attack?
When under a DDoS attack, the response time of a website or service can suddenly slow down or become inaccessible. Be alert for a DDoS attack when there are the following signs:

The website or online service is suddenly inaccessible or the access speed slows down significantly when the network connection is normal, and the server is suddenly disconnected and users are dropped.
A surge in network traffic from a single source IP address or range of addresses.
Unexplained spikes in server CPU or memory utilization.
Unusual traffic conditions occur, such as frequent (e.g., every few minutes) traffic spikes at unusual times.
There are other more specific signs of a DDoS attack, depending on the type of attack, such as a sudden increase in specific types of requests (SYN requests) in a network layer DDoS attack. So how should you go about preventing it efficiently?
What can Proxies IP do for me?
 Proxiescan be an effective tool in a defense scheme against DDoS attacks.
Proxiescan be an effective tool in a defense scheme against DDoS attacks.
The core principle is to improve the stability of the network by introducing Proxy Services between the request and the target server, spreading the malicious traffic to multiple IP addresses so that the attack cannot focus on a single target.
- Traffic Distribution: Proxies IPs can act as triage nodes, spreading requests from different sources to be processed on multiple IP addresses. When an attacker launches a large-scale traffic attack, Proxy Services are able to distribute the traffic among different IPs, avoiding the attack from being all focused on the main server. In this way, the impact of the attack is weakened and the target server is able to continue to operate.
Hiding the real server: Attackers usually attack the main server IP of an organization directly, but if an organization hides its real IP address through Proxies, it will be difficult for attackers to target the real target. This "hiding" strategy allows attackers to launch DDoS attacks against Proxy Services rather than core systems.
Rotating IPs: In some high-intensity DDoS attacks, fixed Proxies IPs may still be under great pressure. At this time, IP address rotationthrough Proxies IP can effectively avoid the same IP continuously under attack. This rotation mechanism enables Proxy Services to constantly change IPs, improving the flexibility and security of defense.
The Critical Role of Proxies IPs
Proxies are more than just simple traffic distribution tools, they are an integral part of the DDoS defense architecture. By dispersing traffic, hiding real servers, Rotating IPs, and combining with load balancersand WAFs, Proxies are able to effectively disperse and digest DDoS attack traffic, protect core servers from attacks, and ensure business continuity.
For organizations facing increasingly sophisticated DDoS attacks, Proxy IPs are not only a great tool for defense, but also an important part of building a more Secure Proxies network architecture.
 At this time, choosing a good and efficient Proxy IP provider is the key to solving the problem. I recommend Proxy4Free Residential Proxies, which provides a powerful Proxy IP service that can effectively help organizations to disperse the attack traffic and protect their servers from large-scale attacks.
At this time, choosing a good and efficient Proxy IP provider is the key to solving the problem. I recommend Proxy4Free Residential Proxies, which provides a powerful Proxy IP service that can effectively help organizations to disperse the attack traffic and protect their servers from large-scale attacks.
As the industry's leading IP Proxies service provider, it not only provides unlimited traffic and bandwidth, but also offers high speed internet with over 30Mbps. Proxies can be selected from 195 countries/regions in the world So far, it has provided efficient Proxies for 20,000+ individual users and 100+ enterprise users!
 Can also be applied to brand protection , and advertising monitoring and Price comparison and other scenarios. Proxies are also highly anonymous and secure, safeguarding your privacy from being violated, and are easy to configure and use, ensuring an ideal choice for an efficient web experience!
Can also be applied to brand protection , and advertising monitoring and Price comparison and other scenarios. Proxies are also highly anonymous and secure, safeguarding your privacy from being violated, and are easy to configure and use, ensuring an ideal choice for an efficient web experience!
Conclusion
DDoS attacks paralyze servers through massive amounts of malicious traffic, putting enormous pressure and risk on businesses. However, the introduction of Proxies IP greatly enhances network protection. At its core, it makes it difficult for attackers to focus on attack targets through multi-layer Proxy Service triage and IP address Rotating. At the same time, hiding the IP address of the real server ensures the security of the enterprise's core resources. By combining with other defense technologies, Proxies IP is not just a simple tool, but a key part of the DDoS defense architecture!