Cryptocurrency trading: The good, the bad and the ugly
 The problem digital currencies solve
The problem digital currencies solve
Everyone talks about “sending” files over the Internet. We send messages, photos and documents every day. But when we send things electronically, it’s not like we’re sending them through the mail. Send data over the Internet and you are really making copies of that data.
When you share a photo in WhatsApp or WeChat, you create a copy of the file that exists on your phone. This copy travels to their servers and on to its destination. But the original file is still with you when the copy arrives. You have not transferred ownership of the file.
Imagine if money worked this way!
If sending digital money were like sending a picture, you would never transfer ownership. Instead, you would multiply your assets and be able to spend the “same coin” twice.
This is known as the “double-spending” problem. It is a fundamental problem that must be solved by any system wishing to represent money digitally. How can we guarantee that the “original” asset has been deleted and that the “copy” represents a transfer of ownership? How can we make a digital equivalent of sending a physical package through the mail?
For decades, the only practical solution to the double-spending problem was a trusted third party. To send money to another person, you would have to trust a third party — be it a company, consortium or individual person — to mediate your transaction and protect it from exploitation or censorship. Both sender and receiver would have to trust the third party with their assets, and the third party would guarantee to transfer ownership on their behalf.
Everyone uses trusted third parties like this in the form of banks and brokers.
The first practical solution to the double-spending problem that did not involve a third party was proposed in 2008 by the pseudonymous Satoshi Nakamoto. In a now-famous paper, Nakamoto presented the protocol for a digital currency called Bitcoin, which was subsequently implemented and launched in 2009.
Bitcoin uses a decentralized network of computers to achieve consensus on a transaction, rather than relying on a single party. Each computer in the network stores copies of all transactions, which are collected in a “blockchain”. To add transactions to this chain, computers must solve cryptographic puzzles. When a computer solves a puzzle, it can record a bundle of transactions to the chain within a single “block”.
Solving these puzzles secures the chain. The network counts the longest version of the blockchain as official. If someone wishes to spend the same coin twice, they have to re-compute the puzzle for the block that recorded the first time it was spent. However — and this is the crucial part — they also have to re-compute the puzzles for every subsequent block in the chain. If they fail, their “fraudulent” version of the blockchain will be shorter than the “official” version, which will have continued to grow in the meantime. To achieve this, an attacker would need to control more computing power than everyone else in the Bitcoin network. This is impractical, so long as the network remains sufficiently decentralized.
The Bitcoin protocol solves the double-spending problem by using a decentralized network, not a trusted third party. This is what makes Bitcoin valuable today: it solved a decades-old problem that was fundamental to transferring assets in the digital era. Now, for the first time, we have a digital form of money that does not involve handing control over to a single party. This is a must in the age of the globalized Internet.
The creation of Bitcoin was followed by that of several other networks employing similar principles. Collectively, these became known as cryptocurrencies.
Today, these networks are used to represent much more than just money. They can record ownership transactions for any kind of digital asset. Not long after Bitcoin appeared, the same techniques introduced “smart contracts”, small computer programs that run on a decentralized network. Smart contracts simulate legal agreements over future transactions, which will execute if certain conditions are met.
The group of technologies that allow these different networks to function has become known as “blockchain” — a reference to the original Bitcoin implementation. Blockchains are networks that can represent ownership and interactions with digital assets in decentralized form, without trusting third parties.
On its most fundamental level, blockchain is a technological solution to the problem of trust.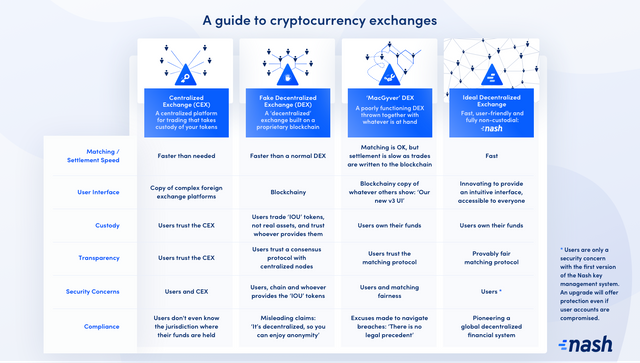 Centralized exchanges: The dangers of custody
Centralized exchanges: The dangers of custody
Cryptocurrencies make a radical proposal. For the first time, they allow us to control our assets directly, without trusting a third party, such as a bank or broker. This is achieved by the use of decentralized networks, collectively known as “blockchains”.
Despite this fact, over 99% of cryptocurrency trading takes place on centralized exchanges (CEXes). Centralized services take custody of users’ assets, allowing them to trade rapidly on a private server. Users are drawn to these services because they offer high speed and volume — however, this is at the expense of the security benefits of decentralization. Indeed, centralized exchanges undermine the fundamental value proposition of the cryptocurrencies they trade: a solution to the problem of trust.
When you send digital assets to a CEX, they are no longer “crypto” currencies — secured by cryptography on the blockchain — but numbers in the CEX’s database. When you deposit your coins to the CEX’s wallet, you lose custody of these coins. In their place, you control a representation of the coins within the CEX’s database, and the CEX promises to give you real coins back when you opt to “withdraw” assets.
But what if the CEX’s wallet or withdrawal system is hacked? What if it is financially irresponsible and cannot redeem your coins, or goes out of business? What if the CEX loses its own keys or its employees embezzle funds? If users do not have custody of their assets, they must trust centralized exchanges to be safe from hackers, insolvency, corruption and plain incompetence.
History shows trusting centralized exchanges to be unwise. Over 700 million USD in assets were stolen from centralized exchanges in the first half of 2018 alone, with that total reaching over 1 billion USD by the end of the year. Indeed, 2018 saw three of the six largest hacks of all time, with thefts amounting to three times those of 2017. Evidence is that centralized exchanges are not improving security over time, and several of the largest exchanges were breached years after commencing operations.
Some of the most popular exchanges, with hundreds of thousands of users today, have been subject to major hacks. In August 2016, Bitfinex lost 72 million USD of Bitcoin, and on 4 March 2014, Poloniex confessed to the theft of 12.3% of its Bitcoin. Of course, no list of hacks would be complete without Mt. Gox, which lost 850,000 Bitcoins, approximately 6% of the circulating supply. This figure demonstrates the absurdity of centralization. The Mt. Gox theft naturally led to the exchange’s insolvency and legal proceedings that affect the market to this day. The CEX as black box: Trust and matching fairness
The CEX as black box: Trust and matching fairness
The problems with centralized exchanges do not stop at custody. Every trade requires a buyer and a seller, and the program that matches buy and sell orders on an exchange is called its matching engine. Not only do you trust the exchange with your coins, but you also trust it to employ a fair matching engine.
By definition, a CEX is a black box. It is a private server, not a public ledger (like a blockchain). You cannot know what is going on inside. This means that unfair manipulation could be occurring within a CEX’s matching engine.
Let’s consider an example.
Say a user places a market buy or sell order on a centralized exchange — that is, an order that can match with a number of smaller buy/sell orders already in its book, and which can hence move the spot price up or down. This gives the exchange privileged access to some key information: it can see how your order will move the market. The exchange can take advantage of this information by holding your order briefly and placing an intermediary order of its own, a practice known as front-running. By “seeing the future” in this way, an exchange can place its own orders to play the market risk-free. Indeed, with some effort, the same strategy can be used for every order (not just market orders), and the privileged information the exchange possesses gives it an advantage even if trades without artificially holding orders back.
It is impossible to know if a CEX is matching trades fairly. You trust the CEX fully with your money, and likewise you trust it not to take advantage of its position.
The solution for this problem in traditional finance is regulation. Exchanges must follow a set of rules on how matching should take place and how the data of trades should be treated. This shifts the issue of trust from the exchange to government auditors, who should guarantee that the exchange follows their rules.
Unfortunately, there is not enough data to quantify how unfair matching is on CEXes today. However, one indicator is the problem of “fake volume”, as measured by projects such as the Blockchain Transparency Institute. Their reports prove that a lot of internal trading occurs within CEX black boxes — and these reports only scratch the surface. Other cases of mysterious activity raise questions about CEX transparency when dealing with hacks. We have to accept their claims, since we cannot look inside the box.
All this is to say nothing of how centralized exchanges can exploit their position without abusing users’ trust directly. From exorbitant listing fees to high trading fees and withdrawal limits that lock users’ funds within their platforms, CEXes have the incentive and the means to take full advantage of their present monopoly.
The solution to these problems sounds simple enough — decentralization. However, there is a reason that 99% of cryptocurrency trading still takes place on centralized exchanges: existing decentralized exchanges leave a lot to be desired.
Let’s examine the problems with such exchanges before turning to Nash, the decentralized platform we have developed to overcome these issues.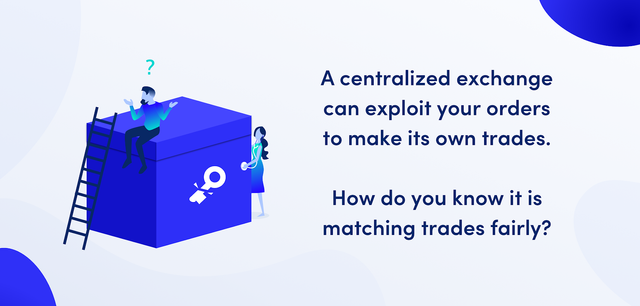 The MacGyver DEX: An imperfect solution
The MacGyver DEX: An imperfect solution
A decentralized exchange (DEX) can circumvent the problem of custody by building its infrastructure on the blockchain. It is possible to use smart contracts to coordinate trades from users’ own wallets. With a DEX, users only have to send funds to a public smart contract, from which they should, in theory, be able to withdraw them to their wallet at any time. In practice, the smart contract must be implemented correctly, with appropriate withdrawal controls — but, in principle, a DEX never requires users to give up control of their assets.
DEXes have their own problems, however, as anyone who has used them can attest. Blockchains are slow by nature. This reduces the number of possible trades per second, limiting volume and liquidity. What’s more, the proximity of DEXes to the blockchain results in a cumbersome user interface based around block explorer and transaction-signing elements.
Speed, volume and user-friendliness aren’t the only limitations of DEXes. The lack of compatibility between different blockchains places restrictions on DEX asset pairs. Relying on smart contract solutions, DEXes can only trade within individual chains. Ethereum-based tokens can be swapped for other Ethereum-based tokens, or NEO-based tokens for NEO-based tokens, but Ethereum cannot be traded directly for NEO.
The most common way for today’s DEXes to support cross-chain trading is token wrapping. Using this method, a “wrapped” token is issued on one chain that represents an asset upon another chain. For example, wrapped Bitcoin (wBTC) is an ERC-20 token on the Ethereum blockchain that corresponds to Bitcoin on the Bitcoin blockchain. The real Bitcoin is held by a custodian outside of the wBTC smart contract. Once a user has wBTC, Ethereum-based DEXes can then trade it against any other token on that network. Unfortunately, this approach has a major problem: users must trust the custodian who is charged with holding their Bitcoin while they hold wBTC. If a custodian is compromised, the Bitcoin that backs wBTC could be stolen, or an attacker could mint unlimited amounts of wBTC to destroy the token’s value.
Other cross-chain techniques, such as atomic swaps, allow you to trade assets directly between chains without trusting a third party. However, these approaches do not scale to large markets and provide new user interface challenges. In particular, for an atomic swap to be safe, both trading parties must monitor chains closely throughout the entire transaction, meaning that a user needs to know in advance when exactly an order will be filled. This defeats the point of orders placed above or below the current price level, which constitute most of the volume on a large exchange.
Finally, there are other ways in which DEXes do not completely eliminate the problem of trust. As with a CEX, matching fairness is a major issue.
Consider an order book based upon the blockchain. When transactions are broadcast to the network, they are not picked up immediately. Rather, they sit in “mempool” of pending transactions, waiting for a miner to generate the next block in the chain. On many networks, transactions can be prioritized by paying a higher “gas” fee to miners. The order in which trades execute will hence not depend on when they were placed, but when they were picked up by miners — which is itself dependent on the number of pending transactions and their gas fees.
These conditions mean that front-running is also possible on DEXes. Even if no malicious intent is present, other problems involving order collisions can occur (e.g. two sellers attempting to fill a buy order, with the later seller’s order being unfairly prioritized). Certain chain-specific protocols offer ways to avoid this problem by taking the order book off the chain. However, this can involve a number of trade-offs, either in terms of potential liquidity, throughput or even the re-introduction of centralized elements in the form of a coordinator.
Trust also plays a more general role in certain aspects of a DEX’s infrastructure. Users must verify that they can withdraw funds from its smart contract if the DEX goes offline. They also trust the DEX to protect them from hackers making malicious trades. In September 2018, 58,000 USD were stolen from the Newdex decentralized exchange by hackers exploiting its asset-listing procedure.
We could refer to exchanges like this as MacGyver DEXes: they are thrown together using whatever parts are at hand and work just well enough to get the job done. But they have various shortcomings in terms of functionality, user-friendliness and even security.
It’s not surprising that the trading volume on existing decentralized exchanges recently hit an all-time low. Beware the fake DEX!
Beware the fake DEX!
A number of so-called “decentralized” exchanges have appeared, or are in development, that attempt to address the problems of MacGyver DEXes. A fake DEX claims to be decentralized because it is built on a blockchain of some kind. However, these blockchains are themselves highly centralized, with nodes usually controlled by the company that built the DEX.
Proprietary blockchains increase the performance of a fake DEX. They can be optimized for trading purposes, with faster block times than chains such as Ethereum, so improved matching speed and volume are possible. They also claim to offer cross-chain trading.
Cross-chain is achieved on a fake DEX through sleight-of-hand. This is similar to the process of token wrapping on MacGyver DEXes. However, while wrapped tokens like wBTC exist on public blockchains, such as Ethereum, a fake DEX uses its own blockchain to issue “IOU” tokens — that is, symbolic tokens that a user hopes to redeem later, much like an informal debt or IOU. Fake DEX users are hence not trading real Ethereum, NEO or Bitcoin, but these “IOU” tokens, which represent them on the fake DEX blockchain. The setup is similar to the internal database of a CEX.
Two security concerns follow from this. Firstly, a user leaves their real assets at the door, entrusting them to a custodian. As we already saw, such custodians can be compromised. Secondly, the fact that a fake DEX uses a private blockchain makes this process similar to trading on the private servers of a centralized exchange. A user has custody of their IOUs, but these IOUs can only be redeemed if they are stored in a secure, trustworthy manner. In short, this approach has all the problems associated with issuing a wrapped token like wBTC but adds the additional complication that users must trust a highly centralized blockchain to manage their “IOU” tokens.
Since their matching operations are based on blockchain technology, fake DEXes face many of the same issues as MacGyver DEXes. In particular, this means poor user interfaces and user experience, combined with the matching fairness issues that arise from establishing time priority in the transaction pool. As with the MacGyver DEX, compromises in terms of centralization or performance must be made if time priority is to be established clearly.
However, it is important not to lose sight of the central issue here: if a DEX is based on a private blockchain, it may as well be centralized. Banks and centralized exchanges do not keep just one copy of their private databases, and a private blockchain is hardly different. In this case, more nuanced arguments concerning time priority within a transaction pool are moot: users are trusting a single entity to have implemented a fair matching protocol with no private tools to enable front-running or other manipulation of transactions.
At best, a fake DEX can provide users with custody of “IOU” tokens. This is custody of nothing at all. Furthermore, when it comes to matching fairness in trading these tokens, a fake DEX is either open to the same problems as a MacGyver DEX or those of traditional centralized exchanges.
Given that they fail to solve the problem of custody, it is debatable whether the speed and cross-chain properties of a fake DEX make it preferable to a MacGyver DEX.
A different solution is required. The DEX with a difference
The DEX with a difference
Nash is a decentralized exchange that combines the speed and functionality of a centralized exchange with the fully non-custodial, trustless nature of an ideal DEX.
We achieve rapid speeds, high volume and cross-chain capacity through an off-chain matching engine. Users’ funds remain under their control within smart contracts, one for each supported blockchain, thus keeping real tokens within their native networks. When trading across chains, users receive a proof that they can update their balance state on each chain. Even if the matching engine disappears, they can submit this to the smart contracts to update their balances.
Although it is not a blockchain, our matching engine is a distributed system, designed to run initially with five nodes and built to be upgradable into a decentralized system. This significantly increases its security. Moreover, this distributed architecture means that our matching engine must be deterministic: it will always match trades in the same way, no matter what conditions it is running under. We are hence able to prove that our matching procedure is always fair. Users can compare input and output logs and verify that the matching engine is working correctly.
Our systems connect to the blockchain via state channel smart contracts. These are smart contracts that can interact both with users’ private wallets and the matching engine itself. Users transfer funds to our contracts in order to trade, but manual withdrawal is possible at all times, even if the platform and matching engine are unavailable. Similarly, users can manually update their on-chain balance to the correct state if the matching engine is unavailable. To maintain speed, the matching engine writes balance updates to these contracts periodically, not after every trade. However, this procedure remains secure, as the matching engine will only adjust users’ contract balances in accordance with orders they have signed cryptographically.
By integrating smart contracts with a secure, off-chain matching engine, we are able to solve the problem of custody while maintaining high performance.
Since Nash is not tied to a blockchain, we are also free to push the boundaries of user experience design. Our simple, intuitive interface is accessible to everyone. Nash creates personal wallets for users that remain entirely under their control, thanks to our zero-knowledge key manager, but which they can easily use within our platform as part of a single account. The experience is like using a centralized exchange, but without giving up custody. We have also developed intuitive tools for simplified trading and effortless asset transfers that go beyond what CEX interfaces offer.
Nash stresses user experience because our goal is to bring decentralized finance to everyone. Our platform is more than just an exchange. Nash is a complete digital asset solution, which at launch will also function as a portfolio management system and fiat gateway (via our banking partners). With the release of our mobile app and payment service later this year, we will expand the possibilities for paying in digital assets, integrating our services directly with websites and dApps.
Our aim is to make the security benefits of decentralized finance available to everyone by ensuring its speed, ease of use and integration within daily life.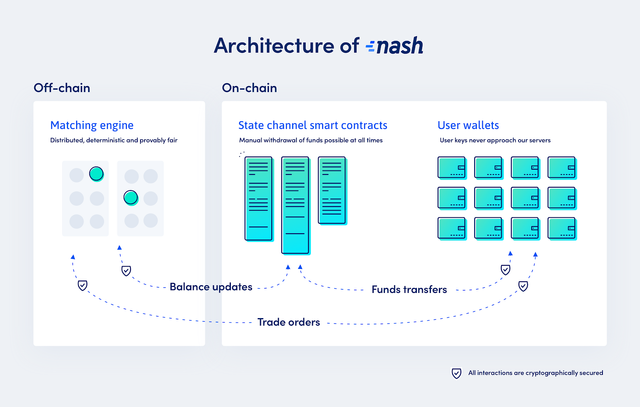 One last word: Compliance
One last word: Compliance
Some proponents of decentralized technology act as if it is beyond the reach of the law. This is not true. States clearly have the power to enforce legislation regarding digital assets, whether for taxation purposes, consumer protection or in the interest of their national economies. The US Securities and Exchange Commission (SEC) recently shut down the EtherDelta decentralized exchange and brought charges against its founder, leaving a number of users with funds locked inside the exchange’s smart contracts. Decentralization was no defense against the charge of operating “an unregistered national securities exchange.”
Nonetheless, existing DEXes and many CEXes shirk legal responsibilities. For example, most DEXes have not obtained the BitLicense and Money Transmitter licenses required to operate in the United States. They meet criticism with weak excuses that there are “no legal precedents” for using decentralized platforms to contravene regulations. This is a misleading claim, since the law cares here about the result of an action, not the technology used to achieve it. Indeed, many exchanges begin operating without licenses from questionable jurisdictions, hoping to make a profit before eventually being closed down — hardly a promising business model, and not one to inspire confidence in users or investors.
By contrast, Nash recognizes the legal reality within which digital assets must find a place. We believe that legal compliance is essential to ensuring the growth of distributed finance.
Firstly, we must create an environment in which the legal status of digital assets is known, thus making them amenable to use by businesses. Distributed ledger technology has enormous disruptive potential. It can increase the freedoms that help economies and businesses grow. But it is not realistic to expect businesses to operate under questionable legal conditions.
Secondly, legal compliance is crucial for safeguarding user and investor capital. Users must know that Nash will not shut down owing to legal troubles, locking up their funds.
To achieve these goals, we strive to work with regulators, ensuring that we are fully compliant in all jurisdictions in which we operate. What’s more, we have broken new legal ground by registering the Nash Exchange token (NEX) as the first digital security token in Europe. This protects Nash investors from market manipulation, fraud and insider trading. It also establishes the legal basis for us to offer investors a share of exchange revenue, giving the token sound economic fundamentals.
We believe that every exchange token is, in practice, a security. They hold no value if the exchanges that issued them cease operations. Other projects continue to operate their platforms without following security and anti-money-laundering (AML) laws. This poses a major risk to investors, as these platforms may suffer harsh consequences when laws are eventually enforced.
By registering Nash as a security, we have laid the groundwork for future companies to release their own digital security tokens.
In addition, we are working to obtain the licenses required to trade this exciting new asset class. We also plan to obtain a variety of licenses in the future that will let us expand our operations.
This legal work is absolutely crucial if we wish to bring decentralized finance to everyone. Not only can our customers be sure that their funds are safe when using Nash, but we are helping to grow the legal infrastructure required for digital assets to realize their full potential.
Revolutionary technology must go hand-in-hand with legal innovation. Nash is committed to delivering both.
Pre-register your Nash account through our referral program and you could win up to $100,000 in Bitcoin! Can’t find a referral code? Try looking on social media for our hashtag #TrustYourselves
Source: https://medium.com/nashsocial/cryptocurrency-trading-the-good-the-bad-and-the-ugly-ef0668bb971c
Credit: Nash Team https://medium.com/nashsocial
Source
Plagiarism is the copying & pasting of others work without giving credit to the original author or artist. Plagiarized posts are considered spam.
Spam is discouraged by the community, and may result in action from the cheetah bot.
More information and tips on sharing content.
If you believe this comment is in error, please contact us in #disputes on Discord
I'm new here sir. Post has been updated already.