Common Cryptocurrency Scams and How to Avoid Them
No one wants to lose their cryptoassets, but crypto is stolen every day because users either aren’t careful or are unaware of the numerous scams and safety concerns that exist in the crypto world.
Don’t be taken by scammers. Here are a number of common cryptocurrency scams and some precautions you can take to avoid them.
Note: Remember that cryptocurrency transactions are immutable, meaning they cannot be reversed. This is a benefit of cryptocurrency because records can’t be tampered with, it protects businesses against chargebacks, etc. But it also means there may be no chance for forgiveness if you make a mistake, leave yourself open to attack, or are duped into sending your funds to a criminal.
Common Cryptocurrency Scams
1. Fake or Cloned Websites
One common scam is to lead a user to a website that is copied and made to like exactly like a known, trustworthy website. Often the URL, or web address, will be quite similar to the website you are searching for, such as having a small spelling mistake, and sometimes these cloned websites will even appear in Google ads. And scammers are getting quite savvy - check out this fake site for the popular exchange, Binance.com:
Notice how the letter "n" has a dot below it. This scam would be particularly difficult to catch! Image by Reddit user u/Games_sans_frontiers.
Prevention Tip: Always double check the URL you are visiting before entering any personal information such as usernames or passwords. Even better, once you are sure you are at the correct site, create a bookmark in your internet browser and always use the bookmark to access that site.
2. Wallet Generator Scams & Fake Wallets
It’s not uncommon to generate a new wallet and private key through a web service such as MyEtherWallet.com or Blockchain.info. However, not all online wallet generators or wallet applications are honest. Some have been created by scammers and will provide you with the address to a wallet the scammer controls. After you send your crypto to your newly created wallet, you will find that someone has sent your crypto elsewhere or the private key you were given does not work. There have even been reports of fake wallet apps showing up in the iPhone app store.
Prevention Tip: Always use a trusted wallet program to store your crypto. You can search for recommended wallets through a cryptocurrency’s official website. If you’re going to generate a wallet through a web service, make sure you research the web service first. And always double check the URL!
Learn more about wallets by reading my overview of different Cryptocurrency Wallet Types & Safety.
3. Hardware Wallet Resale Scams
Hardware wallets are touted as being some of the safest ways to store cryptocurrency, and they are... as long as you set them up yourself. Upon setting up a hardware wallet like the Nano S, your seed phrase is generated and shown to you on the hardware wallet’s screen.
However, there have been accounts of resellers altering the contents that come with the hardware wallet by providing different instructions along with a “scratch-off card” containing a seed phrase. This means the reseller has already set up the wallet, knows the seed phrase, and has created the scratch-off card to dupe the buyer into thinking the wallet is safe. The buyer then unknowingly sends all of their funds to a wallet under the scammer’s control.
Your Ledger device should provide you with a newly generated seed phrase and allow you to set your own PIN - ON THE SCREEN - when you first use it. You should NOT be given a PIN or seed phrase on paper.
Prevention Tip: I recommend buying your hardware wallet directly from the company that makes it. Even though some creative criminals have engineered a scam around hardware wallet resale, actual hardware wallets have never been compromised; so, even if you receive a wallet like the one above, your hardware wallet can still be used by resetting it to factory conditions (on the Nano S you simply enter the PIN incorrectly three consecutive times) and starting a fresh set up with a newly generated seed phrase.
Here's my review of the Nano Ledger S if you'd like to learn more.
4. Gaining Control of Exchange Accounts by Controlling Your Email and/or Text Messages
If you store your crypto through a third party, such as an exchange, you give control of your assets to the exchange and run a few different risks.
First, there’s the risk that the exchange closes, gets hacked, or for whatever reason decides to lock you out of your account. Many consider this risk to be small, and while I agree, there have been major hacks over the last few years that have resulted in the loss of millions.
Second, you run the risk of a hacker gaining access to your account login information, which is a much more common occurrence.
Here’s how it works: most exchanges require some form of secondary authentication when you log in. This method of making you provide two forms of authentication is called two-factor authentication (otherwise known as 2FA). The most basic of these requires you to confirm your login by inputting a code the exchange sends you via email or text message.
Unfortunately, it can be easier than you think for a determined hacker to gain access to email accounts and phone numbers. Phishing scams and malware can result in stolen passwords, and criminals can obtain access to your mobile account by calling your mobile company and tricking them into switching your phone number to their phone (known as phone porting).
Podcaster Travis Wright, a victim of phone porting, describes his experience and further explains these types of hacks on episode 41 of The Bad Crypto Podcast.
Prevention Tip #1: If you have a subjectively sizeable amount of crypto, it’s recommended to store it using your own wallet instead of leaving it in the custody of a third party. Nobody can steal from a personally controlled wallet without your private keys.
Prevention Tip #2: If you have an exchange account, use an app like Google Authenticator or Authy as your second form of authentication. These apps connect to your exchange account and provide an access number that automatically changes every 60 seconds. This more secure form of authentication means a hacker would need your actual phone instead of just access to your phone number in order to steal your crypto.
To take it a step further, you can even make your Gmail account more secure by enabling 2FA to access your email. Note that Gmail and most exchanges let you activate the 2FA feature under your account settings tab.
You can read my quick overview of Why You Should Be Using 2FA.
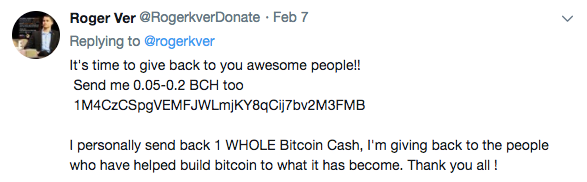
5. Social Media Scams
There has been a recent surge of fake accounts, especially on Twitter, where scammers pretend to be notable people giving away cryptocurrency. Usually the scam involves sending a small amount of a certain crypto and then (not) receiving a larger amount of it back.
In this case, our scammer has created a fake account for Roger Ver, of Bitcoin and now Bitcoin Cash fame. The picture is exactly the same as Roger's real account, and notice that the scammer tweeted this in reply to one of Roger Ver's actual tweets... so Roger's followers might be more likely to come across it. And as with fake web addresses, many of these scammers will create twitter handles that are only a few letters off from an official account.
Prevention Tip: Be cautious about anything that sounds too good to be true, and in general don't send crypto to random people over the internet unless you are donating or paying for something.
Other Important Safety Precautions
1. Private Keys Should Always Be Private
Never, ever give your private keys or seed phrase to someone else. If anyone asks you for these, immediately become wary of them. Also, don’t type your private keys or seed phrases into any device, and don't store them on your computer or phone.
2. Your Wallet is the Safest Wallet
The safest way to store your crypto is by using a wallet only you can access. Storing through a third party always poses some form of risk.
3. Always Double-Check Addresses When Sending Crypto
If you send cryptoassets to the wrong address, they are likely lost forever. Make sure you double-check the receiving address before finalizing the transaction. Personally, I like to double-check the first 3-5 characters and last 3-5 characters of the address before clicking send.
4. Use a Two Factor Authentication (2FA) App When Available
As stated above, use an app like Google Authenticator or Authy to make your exchange accounts (and even your Gmail account) more secure from hackers.
5. Use Anti-Phishing Phrases to Guarantee Authenticity of Emails
Many exchanges allow you to choose a personalized anti-phishing phrase or code. This phrase will always appear in any official email sent to you by the exchange, making it easy to determine whether an email is authentic or a phishing scam (trying to obtain your private information such as passwords).
6. Research Projects and Services Before Using or Investing in Them
Whether it’s an online wallet generator or new ICO you want to invest in, do your homework. Check for reviews, whether the code is open source, who the creators are, etc. Don’t lose your crypto due to laziness.
7. Sound Too Good to Be True? Then It Probably Is.
Use common sense. If a cryptocurrency project guarantees X% returns on your investment, there's a good chance it's a Ponzi scheme or some other type of scam.
Remember: There are a lot of people out there who want your crypto. Be safe!
Have I forgotten any scams you'd like added to this list? Let me know in the comments.