810 STEEM ~ Sponsored Writing Contest: Goldilock
Welcome to the @OriginalWorks sponsored writing contest!
Status: CLOSED.
Accepted Languages:
- English
Accepted Languages:
- English
Start Time: 11:50 PM ET, Saturday
End Time: 11:50 PM ET, Tuesday
Special Twitter 0.5 STEEM bonus! Details outlined at the bottom.
This is a call to all great Steemit writers! Goldilock has sponsored a Steemit writing contest!

Prize Pool Total: 810 STEEM
Prizes: 660 STEEM + 150 STEEM (Bonus Increased To: 100 bonuses of 2.5 STEEM!) + Twitter Bonus (Details Below)
- 1st Place: 70 STEEM
- 2nd Place: 60 STEEM
- 3rd Place: 52 STEEM
- 4th Place: 47 STEEM
- 5th Place: 36 STEEM
- 6th Place: 34 STEEM
- 7th Place: 28 STEEM
- 8th Place: 25 STEEM
- 9th Place: 22 STEEM
- 10th Place: 21 STEEM
- 11th Place: 20 STEEM
- 12th Place: 19 STEEM
- 13th Place: 17 STEEM
- 14th Place: 15 STEEM
- 15th Place: 14 STEEM
- 16th - 20th: 11 STEEM
- 21st - 25th: 8 STEEM
- 26st - 30th: 7 STEEM
- 31st - 40th: 5 STEEM
- 41st - 100th: 2 STEEM Bonus
Deadline: 72 Hours
- 1st Place: 70 STEEM
- 2nd Place: 60 STEEM
- 3rd Place: 52 STEEM
- 4th Place: 47 STEEM
- 5th Place: 36 STEEM
- 6th Place: 34 STEEM
- 7th Place: 28 STEEM
- 8th Place: 25 STEEM
- 9th Place: 22 STEEM
- 10th Place: 21 STEEM
- 11th Place: 20 STEEM
- 12th Place: 19 STEEM
- 13th Place: 17 STEEM
- 14th Place: 15 STEEM
- 15th Place: 14 STEEM
- 16th - 20th: 11 STEEM
- 21st - 25th: 8 STEEM
- 26st - 30th: 7 STEEM
- 31st - 40th: 5 STEEM
- 41st - 100th: 2 STEEM Bonus
Deadline: 72 Hours
All articles must be submitted within 72 hours of this post to be considered!
Changes in submission rules below
What is Goldilock?
Goldilock is a revolutionary digital asset security system which acts as remotely disconnected cold storage until such time that the user needs access to their data for its intended purpose.
Goldilock's encrypted nodes remain vaulted offline, physically disconnected from the internet until a user brings their personal device online remotely via a non-IP (not over the internet) command, after which time they can access it using the same bank-level security mechanisms they would with other sensitive data. Once the user is finished using their node to complete transactions, allocate asset rights, or transfer specified data, the node then reverts to an isolated physical air gap environment, invisible and inaccessible from the internet.
Goldilock is built around the premise that anything connected to the internet can and will be hacked. The past few years have seen more than 3 billion data breaches across many sectors, from banking and credit, into personal health data and digital rights, through to billions of dollars stolen in the cryptocurrency industry, proving time and time again that no industry is safe from intrusion.
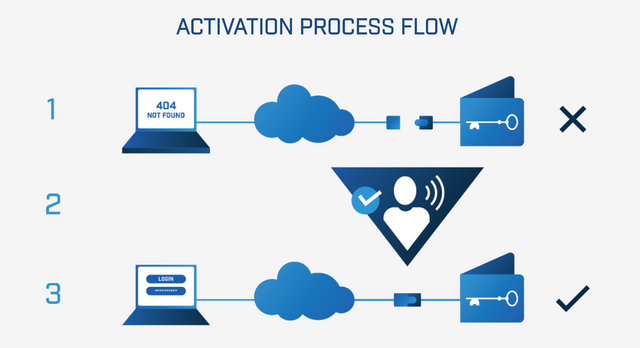
The inherent security vulnerabilities within internet and blockchain infrastructure are why Goldilock uses a physical air gap disconnection method. This means, as the name suggests, that the devices storing sensitive data are physically disconnected from the internet, remaining isolated in a vaulted location.
Current Storage Solutions
Current methods:
● Hot storage: Cloud storage, exchanges, online wallets, online multisig structures
● Cold Storage - personal USB hard drives, Trezor, Ledger Wallet, Xapo or Blockvault (the latter two being vaulted electronic storage for institutions, which takes days to bring online)
Hot Storage
Most individuals in the crypto space are familiar with the shortcomings associated with centralized asset storage methods.
The customer of an exchange or an online wallet generally has no idea or power over how their cryptocurrency is stored. The website could have security flaws, exposing all the user funds to hacks. There are a number of examples in recent history, most notably the famous Mt.Gox case, followed by more recent examples such as Coincheck losing over $500m in NEM, and just last month Bithumb and Coinrail. In 2018 alone, more than $750m in crypto assets have been stolen.
Personal Cold Storage
Personal cold storage offers vast security benefits over keeping your cryptocurrency or other sensitive data online. That being said, there are major issues when it pertains to losing/breaking the physical devices that keep your private information.
Problems with personal cold storage include:
● User must be tech-savvy, not conducive to mass adoption.
● Devices can be broken/lost, causing detrimental losses.
● Data is inaccessible without physical device present.
● Every major electronic hardware wallet has been hacked, including Ledger and John McAfee’s Bitfi wallet, released just last week.
● These solutions cannot be used by institutional clients for custody, leaving hundreds of billions of dollars on the sidelines until secure custody is truly solved.
● These methods apply to crypto only, and cannot be used for larger use-cases involving banks, credit agencies, digital rights holders, healthcare providers, nor any of the other major data custody providers who handle our sensitive data.
Application
There is a wide array of fields where Goldilock technology can be applied.
Goldilock can be used by individuals to store sensitive information, such as cryptocurrencies or personal files, or by larger institutions where security is a priority for their crypto or their customer data.
Identity
Digital personal identity data requires a high level of security. There are many services that require personal data to register, this can range from KYC to signing up for an insurance policy. Traditionally people handle the documents physically or scan and email the information required. This leaves huge security gaps, as your personal documents are stored online on your email account or on a drive, and are prone to hacks and malicious use.
Even with the introduction of blockchain identity services like CIVIC, losing your key means someone can steal your identity, and there not any safe back-up options for those keys. In this case, a provider like CIVIC can benefit from using Goldilock security services.
With Goldilock, users are granted access to their data and digital assets on a per need basis. After the user has finished performing their identity verification, for example, the data goes back offline, inaccessible for anyone to see or access.
Credit Score
Credit scoring companies have also been subject to hacker attacks. Recently, a well-known credit score company, Equifax, was attacked and the personal information of hundreds of millions of consumers was stolen. Consumers were then tasked with freezing their credit through a time-consuming and complex process, which later required them to jump through hoops to bring their credit back to active status – meaning they are again vulnerable.
Banks are partnering with Goldilock, integrating their security layer for larger accounts and for enacting wire transfers, with both being connected only for the duration of intended interaction of data with individual user accounts.
Wallet
Goldilock can be used to store cryptocurrency in a way that offers the security of cold storage, while maintaining the convenience of an online wallet.
Users are able to hold their cryptocurrencies with Goldilock, and the information will be stored offline until such a time that the user requests their individual encrypted node is connected to the internet using an analogue command off the internet, whereupon they can access their data via an encrypted channel over the internet after passing through bank-level security gateways.
Importantly, using the Goldilock model, the private key never leaves the individual node, meaning it cannot be stolen or corrupted while connected.
Voting Machines
The Goldilock patented security protocol can extend to very crucial and practical applications.
Consider it more as hardware that can be added to traditional voting machines. Those machines currently are online, all the time during an election. If each machine has a vaulted, encrypted node inside it which stores all vote data, and those machines in each physical location share a backup mechanism which is completely disconnected from the internet, those votes cannot be hacked. At the moment administrators wish to access the data remotely, they make the remote command to connect the node and deliver the data in a very short connection window thorugh our encrypted channel, thereby lessenning by 99.999% the amount of time machines are online, equally reducing the amount of time hackers have to fine and crack the machines to corrupt data.
Goldilock LOCK Token
LOCK is the utility token that will be used to provide a gateway for Goldilock services.
The LOCK token is required to access the [Goldilock](https://www.goldilock.com/) Wallet. When the user logs into the [Goldilock](https://www.goldilock.com/) Wallet, the Wallet will query the NEO public Blockchain to confirm the user’s public key address owns a LOCK token. If the user’s public key address owns a LOCK token, then the [Goldilock](https://www.goldilock.com/) Wallet will launch in the user’s browser. When the user is granted access, the Wallet will write audit information to our own Private Audit Blockchain. These audit entries will ensure that every time your private key is brought online, this access is written to immutable storage that can be queried from the [Goldilock](https://www.goldilock.com/) Wallet.LOCK token allows Goldilock to provide users with a record of their node activity, while keeping user-owned data encrypted and locked away even from everyone including the Goldilock team.
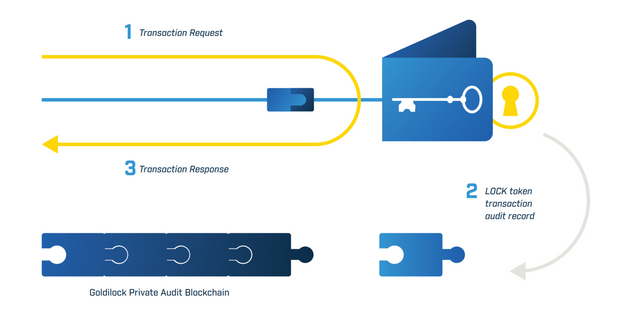
NEO will be the first cryptocurrency to be integrated, with others following shortly thereafter.The Goldilock Wallet service can be paid for on a subscription basis by LOCK.
Use-Case
Personal
Bob loves to travel. He has saved up enough money to quit his job and travel for a year. He will be travelling to big cities as well as remote locations, so he would like to minimize his luggage to essentials.
Throughout his trip, Bob will need:
● Documents - Passport, Driver's License, Visas, Insurance policies, etc.
● Finance – Cryptocurrency hardware wallet, banking USB key
While Bob was packing up his important documents in a small bag, he kept worrying about what would happen to him if he misplaced his documents and related hardware device. His entire trip would be ruined, and it would take him forever to replace all the lost documents.
Bob mentioned his worries to his friend, Alice, who mentioned Goldilock!
With Goldilock, Bob can rest easy. He can leave his documents and cryptocurrency wallets at home where they belong. There is no need for him to carry around such important items and risk losing it all.
Instead, he can store relevant data with Goldilock, and access his data whenever he needs it!
Commercial
A huge insurance company in New York, WeKeepInfoOnline Corporation, has been experiencing security issues. They use the highest layers of security protocols available today, and invest million in cyber security. Even with all of this, they are in constant fear of being infiltrated, since the data they store is extremely personal for their clients and any security breach would mean the end of their prospering business.
While they kept brainstorming ideas of how to improve their online protection, an engineer on the team brought up Goldilock.
The company immediately implemented Goldilock, and changed their name to WeDontKeepInfoOnline, propelling themselves to the forefront of information security. They can now sleep easy knowing that their data is invulnerable to hackers, since it is not online in the first place!
Goldilock provides an incredibly unique storage solution hence the slogan; it is "not hot storage, not cold storage, just right storage." Storage in such a way, that sensitive digital data can finally be fully protected.
For more information watch this short feature intro:
More Information & Resources:
- Goldilock Website
- Goldilock WhitePaper
- Goldilock Tokenomics
- Goldilock Telegram
- Goldilock Discord
- Goldilock Linkedin
- Goldilock Facebook
- Goldilock Twitter
- Goldilock Reddit
- Goldilock Github
Submission
- Write an article about Goldilock and how it will change the way people handle their sensitive digital data! What are the benefits of combining the best of cold and hot storage? How can improved cryptocurrency security and access impact mass adoption? What is the security benefit of keeping the data offline using "airgap" technology? Why did Goldilock opt for NEO as their platform of choice? How can banks, insurance companies, and other institutions benefit from integrating Goldilock technology to their existing systems? Maybe write some cool use cases, crypto and non-crypto related. As always, the topic is fairly open-ended, so be creative!
- To submit please do the following:
- Add the word "goldilock2018" (without the quotes) at the very end of your article.
- Link this post in your submission.
- Post the link to your article as a reply to this post.
- Resteem this contest post.
Rules
The article must be at least 250 words in length and it is recommended(not mandatory) that the length is under ~1500 words.
At least 70% of the submission must be original. Using "article spinners", and other word substitution tools is also not permitted.
All copied text must be in quotes. Feel free to copy links to resources from the contest post, but please be sure to not copy from other contestants.
Please keep discussions relevant to the contest topic. We would like to encourage a good vibe in the comments!
- Write an article about Goldilock and how it will change the way people handle their sensitive digital data! What are the benefits of combining the best of cold and hot storage? How can improved cryptocurrency security and access impact mass adoption? What is the security benefit of keeping the data offline using "airgap" technology? Why did Goldilock opt for NEO as their platform of choice? How can banks, insurance companies, and other institutions benefit from integrating Goldilock technology to their existing systems? Maybe write some cool use cases, crypto and non-crypto related. As always, the topic is fairly open-ended, so be creative!
- To submit please do the following:
- Add the word "goldilock2018" (without the quotes) at the very end of your article.
- Link this post in your submission.
- Post the link to your article as a reply to this post.
- Resteem this contest post.
Rules
The article must be at least 250 words in length and it is recommended(not mandatory) that the length is under ~1500 words.
At least 70% of the submission must be original. Using "article spinners", and other word substitution tools is also not permitted.
All copied text must be in quotes. Feel free to copy links to resources from the contest post, but please be sure to not copy from other contestants.
Please keep discussions relevant to the contest topic. We would like to encourage a good vibe in the comments!
The article must be at least 250 words in length and it is recommended(not mandatory) that the length is under ~1500 words.
At least 70% of the submission must be original. Using "article spinners", and other word substitution tools is also not permitted.
All copied text must be in quotes. Feel free to copy links to resources from the contest post, but please be sure to not copy from other contestants.
Please keep discussions relevant to the contest topic. We would like to encourage a good vibe in the comments!
Video Bonus
- Feel free to use images and media from their website. You can even make your own video and have it in your submission! Videos have a chance of winning a separate bonus based on quality. Videos should be uploaded to YouTube. DTube or IPFS. Please do not remove the videos, or it might impact future eligibility. Feel free to make a new YouTube account for these. We really wanted to use DTube, but sometimes the videos were not view-able at all. We may change this in again in the future. For the time being please ensure whatever service you choose to use is working.
Twitter Bonus
For the Twitter bonus:
- Tweet the link to your article on Twitter.
- Tweet should contain article link, as well as @GoldilockSecure or #Goldilock.
- Add the link to your tweet at the bottom of your competition Steemit post!
- At the end of your article, add the word "goldilocktwitter", without the quotes!
This is great because it will also encourage Twitter users to come join Steemit as well!
The bonus for this 0.5 Steem for every article that tweets and meets a level of quality and contest conditions.
How the winners are decided
The submissions will be passed along to the team at Goldilock, and they will decide the best method for picking winners and the winning articles.
This can mean that the team judges the submissions, or they ask our team to judge it. Regardless of the method, the final say always lies with the sponsor.
More information & recommendations:
- Pay attention to spelling and grammar!
- Feel free to use informal language such as "I would, etc"
- Use information and resources above to learn more about Goldilock!
- If you copy something, use quotes. This is an @OriginalWorks contest after all :)
- Link the company's website: Goldilock so that your readers can do research for themselves.
- Articles can be edited up until the deadline.
After writing an article, within a few minutes you should get one of these as a response to your article post:
If you don't get one, let me know by adding a quick message after you submit your link as a reply here and it will be done manually. Sometimes it can take some time, so don't worry if it isn't instant! Rest assured, as long as your link is shared as a reply here, everything is double checked at contest close to ensure that all articles are submitted!
60 submissions will get 2 STEEM each. The article must meet the contest conditions such as word length and a level of quality.
Disclaimer: @OriginalWorks makes no claims as to the legitimacy or operating procedures of contest topics. @OriginalWorks does not offer any sort of investment advice. This is a writing contest. @OriginalWorks only guarantees prize payout. The contest topic company may choose to share the contest submissions that receive prizes. If for whatever reason there are over 500 submissions, new submissions will not be considered.
https://steemit.com/crypto/@mayorfaruk/goldilock-digital-asset-security
Twitter link:https://twitter.com/Ajibolafaruk3/status/1026850662632640512?s=20
https://steemit.com/crypto/@kwadjobonsu/have-you-heard-of-goldilock
My post
https://steemit.com/originalworks/@ggcarlosr/goldilock-security-for-your-data-and-wallet
My tweet
https://twitter.com/GGCarlosR/status/1026524064612077573
my entry here
My tweet:
https://twitter.com/aerossone?lang=es
goldilocktwitter
Good day @OriginalWorks
Thank you for all the awesome things you've been doing. Please, included below is the link to my entry.
https://steemit.com/crypto/@sirpee/goldilock-the-right-storage
Happy Sunday Stemianos, this is my little contribution to the contest
Fuente
https://steemit.com/scrypto/@maxili63/goldilock-security-system
Twitter link:
goldilocktwitter: https://twitter.com/maxili03/status/1026181539267338240
Hi guys, here is my entry to the contest
https://steemit.com/blockchain/@merryslamb/goldilock-the-solution-to-keep-your-digital-data-safe
My twitter link:
https://twitter.com/MerrysLamb/status/1026284141430616064
My entry:
https://steemit.com/crypto/@liltom/goldilock-the-right-storage-for-cryptocurrencies
https://steemit.com/crypto/@hayomide/introducing-digital-asset-lock-security-by-goldilock
Here's my entry.
https://steemit.com/goldilock/@osigbhemeh/goldilock-an-avenue-to-keep-digital-datas-safe