Cryptocurrency Security Best Practices: Protect Your Digital Assets in 2025
Cryptocurrency offers unparalleled financial freedom, but its decentralized nature also makes it a prime target for cybercriminals. In 2023 alone, over $4 billion was lost to crypto hacks and scams. Whether you’re a seasoned investor or new to blockchain technology, securing your digital assets is non-negotiable.
This guide dives into the most critical cryptocurrency security best practices, covering common threats like phishing and fake wallets, actionable steps to safeguard your crypto, and tools to stay ahead of attackers. Let’s ensure your investments remain safe in an increasingly risky digital landscape.
Why Cryptocurrency Security Matters
Cryptocurrencies operate on decentralized networks, eliminating intermediaries like banks. While this boosts transaction speed and autonomy, it also shifts full responsibility for security to users. A single mistake—like leaking your private key or falling for a phishing scam—can lead to irreversible losses.
Key risks include:
- Irreversible Transactions: Crypto transactions cannot be reversed once confirmed.
- Anonymity: Pseudonymous wallets make tracing stolen funds nearly impossible.
- High Reward for Attackers: Cybercriminals target crypto due to its high value and global accessibility.
By adopting robust security practices, you mitigate these risks and ensure your assets remain under your control.
Top Cryptocurrency Security Threats to Avoid
Understanding common threats is the first step toward protection. Here are the most prevalent attacks targeting crypto users:
1. Phishing Scams
Fraudsters impersonate legitimate platforms via fake emails, websites, or social media posts to steal login credentials or private keys. Example: A fake Coinbase login page redirecting users to a malicious server.
2. Fake Wallets and Exchanges
Malicious apps mimic trusted wallets or exchanges to trick users into sharing seed phrases. Always verify URLs and download software from official sources.
3. Pump-and-Dump Schemes
Scammers artificially inflate a token’s price using false hype, then sell their holdings, leaving investors with worthless assets.
4. Malware and Ransomware
Malicious software can log keystrokes to steal wallet passwords or encrypt your data until a ransom is paid.
5. Social Engineering
Attackers exploit human psychology—like impersonating customer support—to gain access to sensitive information.
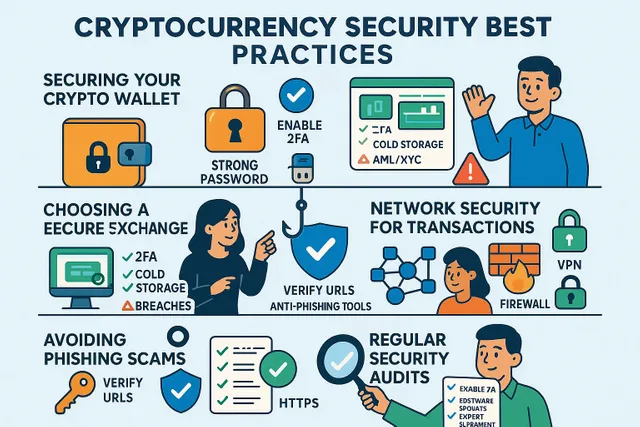
Cryptocurrency Security Best Practices for 2025
1. Secure Your Wallet Like a Fortress
Your crypto wallet is the gateway to your assets. Follow these steps:
- Use Hardware Wallets: Store large amounts offline with devices like Ledger or Trezor.
- Enable Multi-Factor Authentication (MFA): Add an extra layer of security beyond passwords.
- Backup Seed Phrases: Write them on paper and store them in a fireproof safe—never digitally.
Pro Tip: Avoid discussing your holdings publicly to reduce targeting risks.
2. Strengthen Exchange Security
Choose exchanges with proven security measures:
- Cold Storage: 95% of funds should be kept offline.
- Regular Audits: Look for platforms with third-party security certifications (CCSS).
- Withdrawal Whitelists: Restrict crypto withdrawals to pre-approved addresses.
3. Avoid Phishing and Social Engineering
- Verify URLs Manually: Ensure website addresses match official domains (e.g., binance.com vs. binance-net.com).
- Ignore Unsolicited DMs: Legitimate companies will never ask for private keys via email or social media.
- Use Anti-Phishing Tools: Browser extensions like MetaCert flag suspicious sites.
4. Protect Your Network and Devices
- Use a VPN: Encrypt internet traffic to prevent eavesdropping on public Wi-Fi.
- Install Antivirus Software: Detect and block malware targeting crypto wallets.
- Update Firmware Regularly: Patch vulnerabilities in wallets, routers, and devices.
5. Implement Advanced Security Measures
- Transaction Signing: Confirm recipient addresses via QR codes or hardware wallet verification.
- Decentralized Exchanges (DEXs): Trade directly from your wallet without depositing funds on centralized platforms.
- Monitor Blockchain Activity: Tools like Etherscan track suspicious transactions in real time.
How to Recover from a Security Breach
Despite precautions, breaches can occur. Act swiftly to minimize damage:
- Freeze Accounts: Contact your exchange immediately to halt unauthorized transactions.
- Report to Authorities: File a report with the FTC or local cybercrime units.
- Rotate Credentials: Change passwords and generate new private keys for unaffected wallets.
Conclusion
Cryptocurrency security demands vigilance, education, and the right tools. By securing wallets with hardware devices, avoiding phishing traps, and choosing audited exchanges, you significantly reduce risks. Stay proactive—update software regularly, monitor transactions, and never share sensitive data.
Ready to fortify your crypto holdings? Explore our curated list of ultra-secure software wallets and tools at CryptoCrafted.org to start your journey toward ironclad security today.